What's new with Secure score in Microsoft Defender portal (and some other tips)
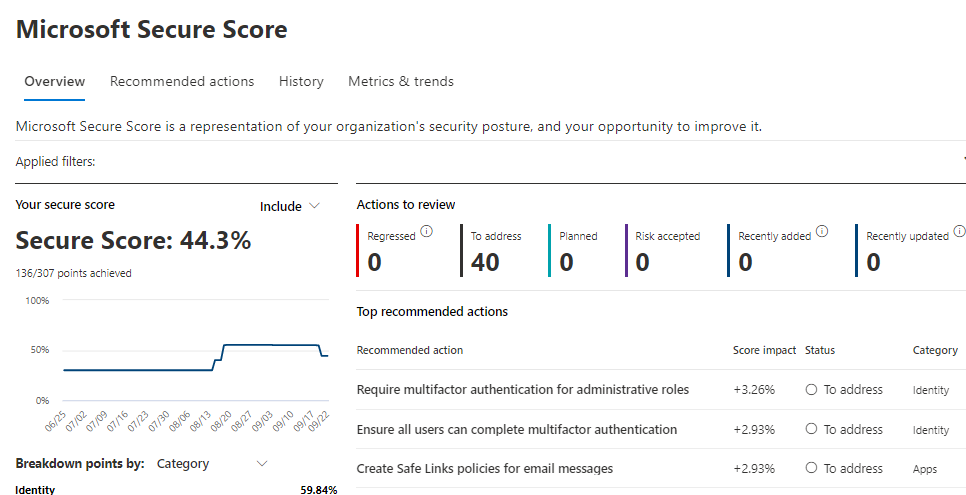
What is Secure score?
Microsoft releases suggestions on security settings that should be turned on to enhance your security posture against external and internal threats.
You're given points for the following actions:
- Configuring recommended security features
- Doing security-related tasks
- Addressing the improvement action with a third-party application or software, or an alternate mitigation
Each improvement activity is worth no more than ten points, and the majority of them are assessed in a binary manner. You receive all of the points if you carry out the improvement activity, such as setting up a new policy or turning on a certain setting. Points are awarded as a proportion of the overall configuration for additional enhancement actions.
If you safeguard all of your users with multi-factor authentication, you receive 10 points, according to an enhancement activity. You receive a partial score of 5 points because you only have 50 of the 100 total users protected (50 protected / 100 total * 10 maximum points = 5 points).
How it compares with other scores?
The are different scores, don't get mixed up which one is for which service model.
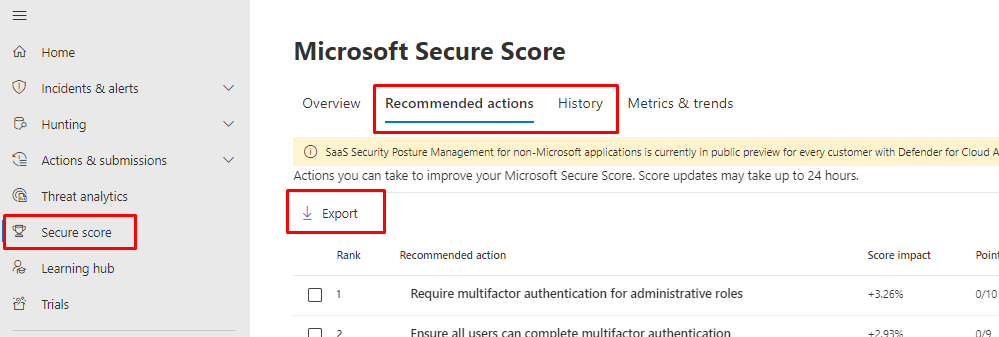
How to access?
Portal
You will find it from https://security.microsoft.com/securescore
And you can export the suggested actions and the history of the score calculations and actions. The format is only CSV.
Graph
But you can also use Graph calls to get those scores.
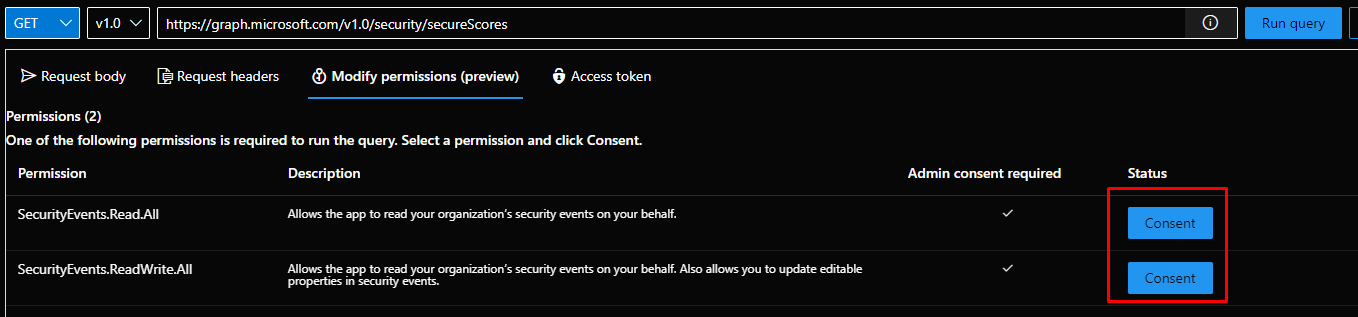
PowerShell
If you like to use PowerShell rather than Graph calls, you can use this one.
Import-Module Microsoft.Graph.Security # List scores Get-MgSecuritySecureScore # List score controls Get-MgSecuritySecureScoreControlProfile

Get-MgSecuritySecureScore (Microsoft.Graph.Security)
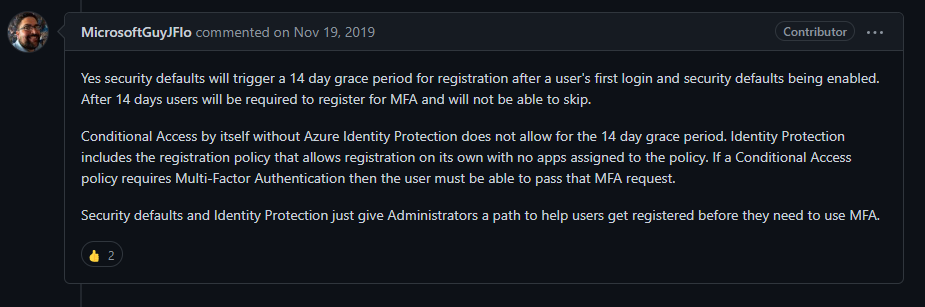
But I already have Security defaults enabled?
That's great and you will awarded with extra points to your score.
- Ensure all users can complete multi-factor authentication for secure access (9 points)
- Require MFA for administrative roles (10 points)
- Enable policy to block legacy authentication (7 points)

Providing a default level of security in Azure Active Directory - Microsoft Entra
Security defaults enforcement will be effective for the following roles immediately after enablement but there is a 14-days grace period.
- Global administrator
- Application administrator
- Authentication administrator
- Billing administrator
- Cloud application administrator
- Conditional Access administrator
- Exchange administrator
- Helpdesk administrator
- Password administrator
- Privileged authentication administrator
- Security administrator
- SharePoint administrator
- User administrator
But there is also other things to consider.
Conditional access and MFA
The first notice for enabling CA policies is to disable Security defaults if in use.
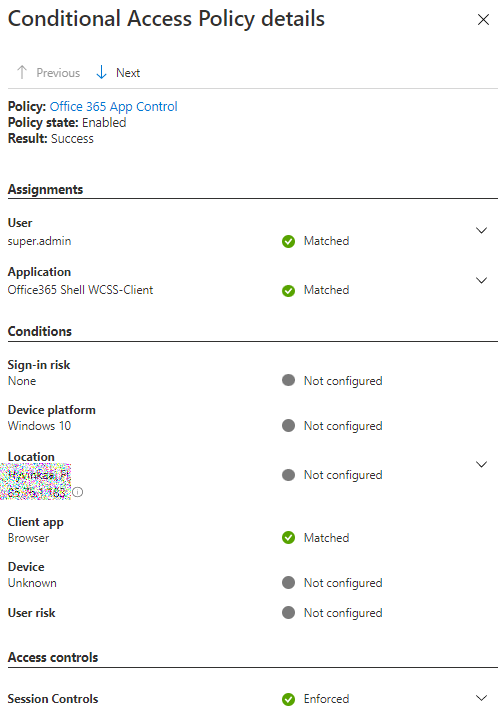
Section 9 – Implement an Authentication and Access Management Solution – Plan, implement and administer conditional access
And also see the Authentication methods explanation, you should really enable more than "Approve / Deny" methods. MFA fatigue is a real risk, just see what happened to Uber.
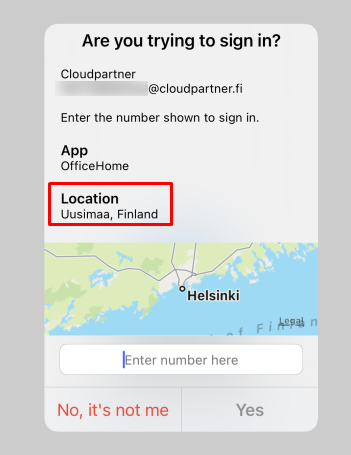
Microsoft managed Authentication Methods Policy (Preview)
What's new for September?
New Microsoft Defender for Office 365 recommendations for anti-phishing policies are now available as Secure Score improvement actions:
- Set the phishing email level threshold at 2 or higher
- Enable impersonated user protection
- Enable impersonated domain protection
- Ensure that mailbox intelligence is enabled
- Ensure that intelligence for impersonation protection is enabled
- Quarantine messages that are detected from impersonated users
- Quarantine messages that are detected from impersonated domains
- Move messages that are detected as impersonated users by mailbox intelligence
- Enable the ‘show first contact safety tip’ option
- Enable the user impersonation safety tip
- Enable the domain impersonation safety tip
- Enable the user impersonation unusual characters safety tip
A New SharePoint Online recommendation is now available as a Secure Score improvement action:
- Sign out inactive users in SharePoint Online

What’s new in Microsoft Secure Score
