Storage accounts and the differences between SAS keys and Access keys.
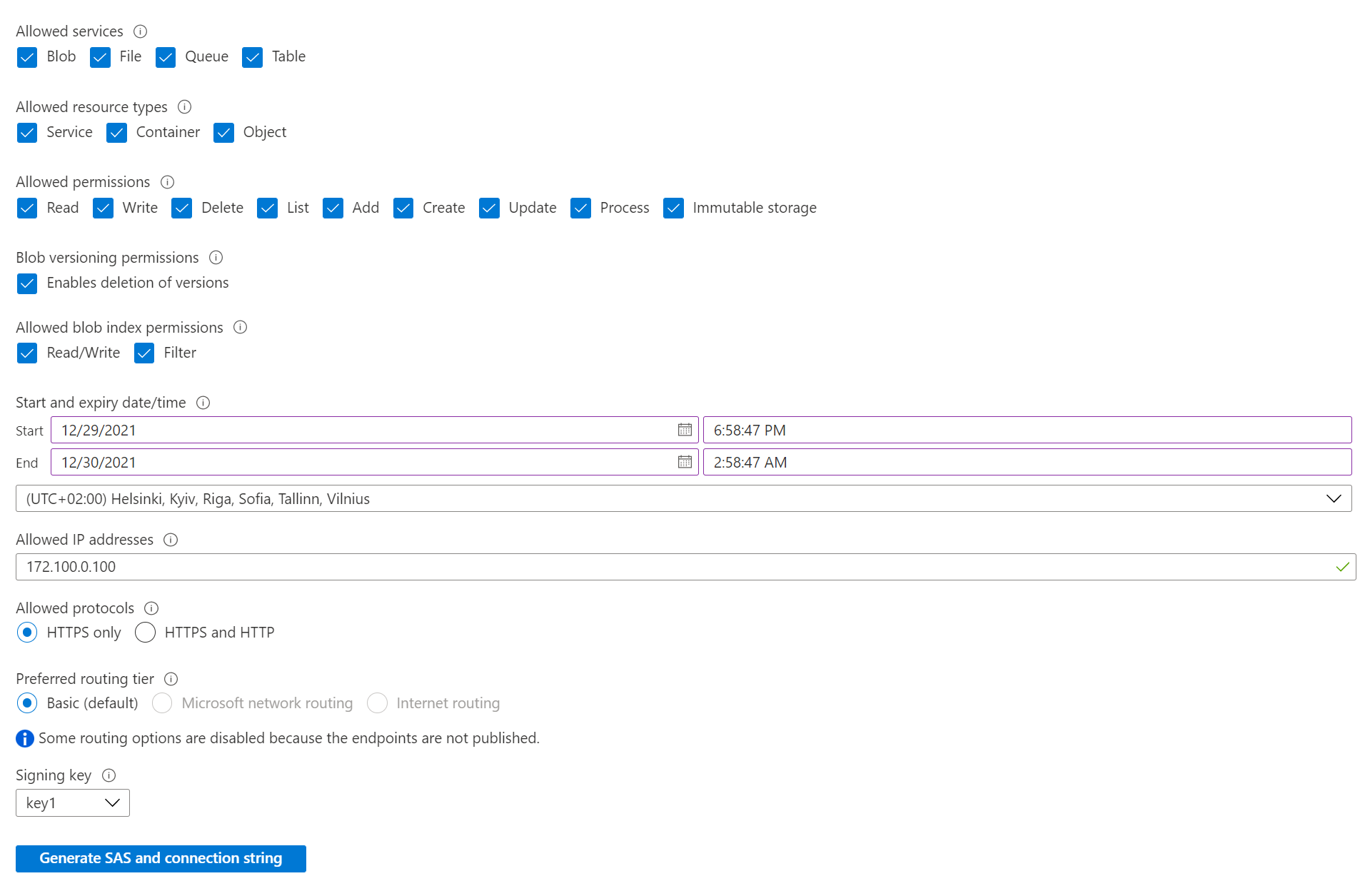
When you click Generate you will get a random string based on the settings you chose, one for each service type.
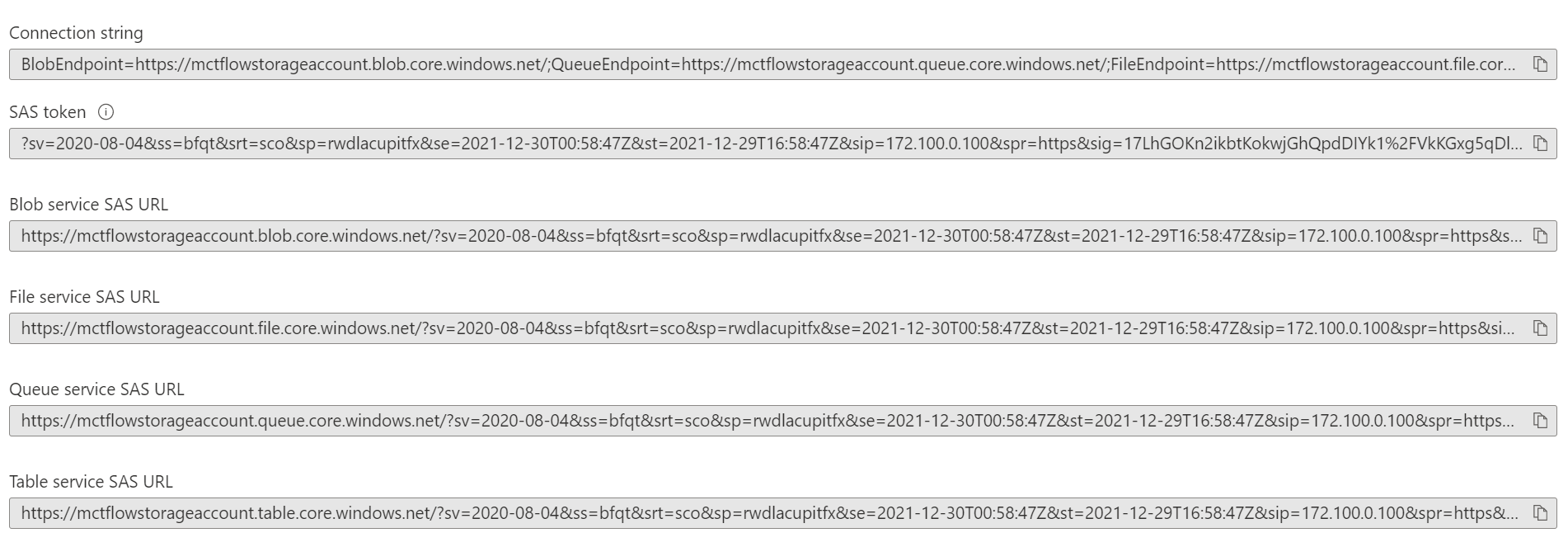
Let's have a closer look at the File service SAS URL. Here you can see the ip-address and the start and the end times for the string generated.

And you can use this string to connect example with Azure Storage Explorer.
And choose either one.
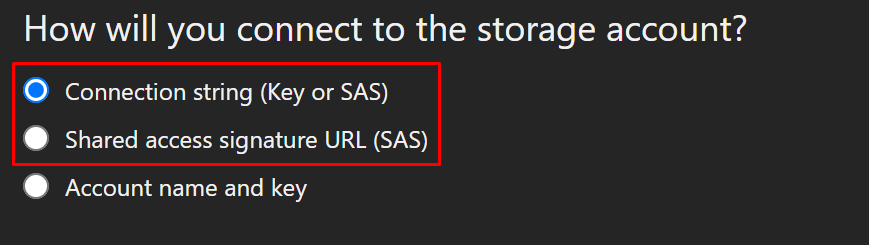
Paste in the connection string that was generated.
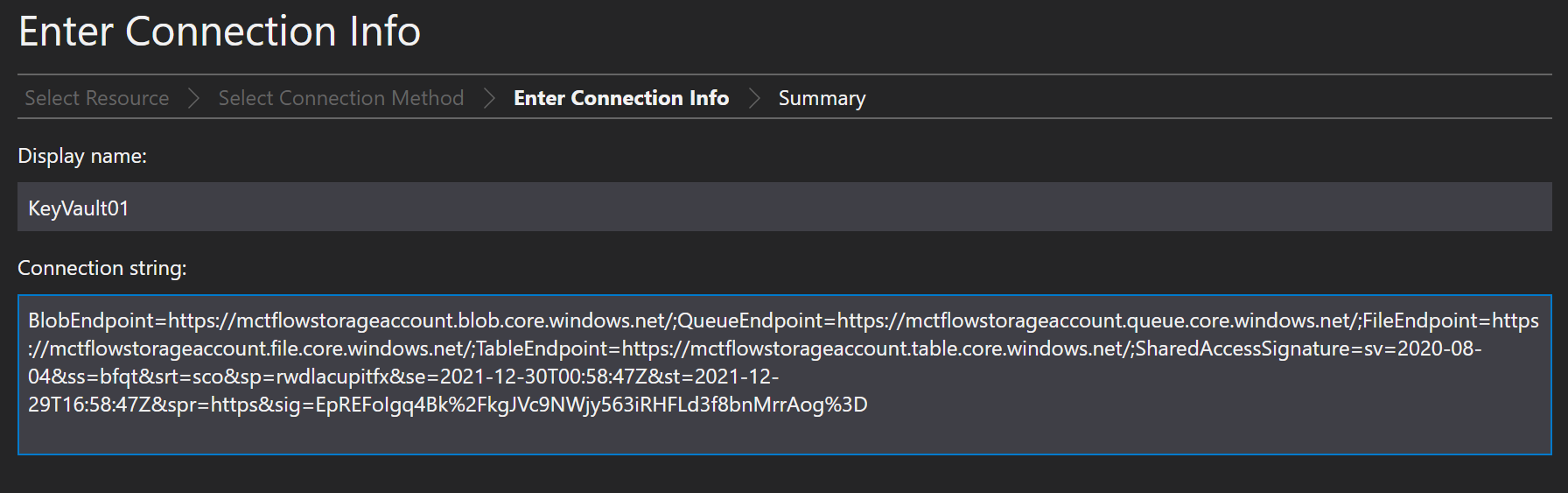
And hit connect after reviewing the settings are correct.
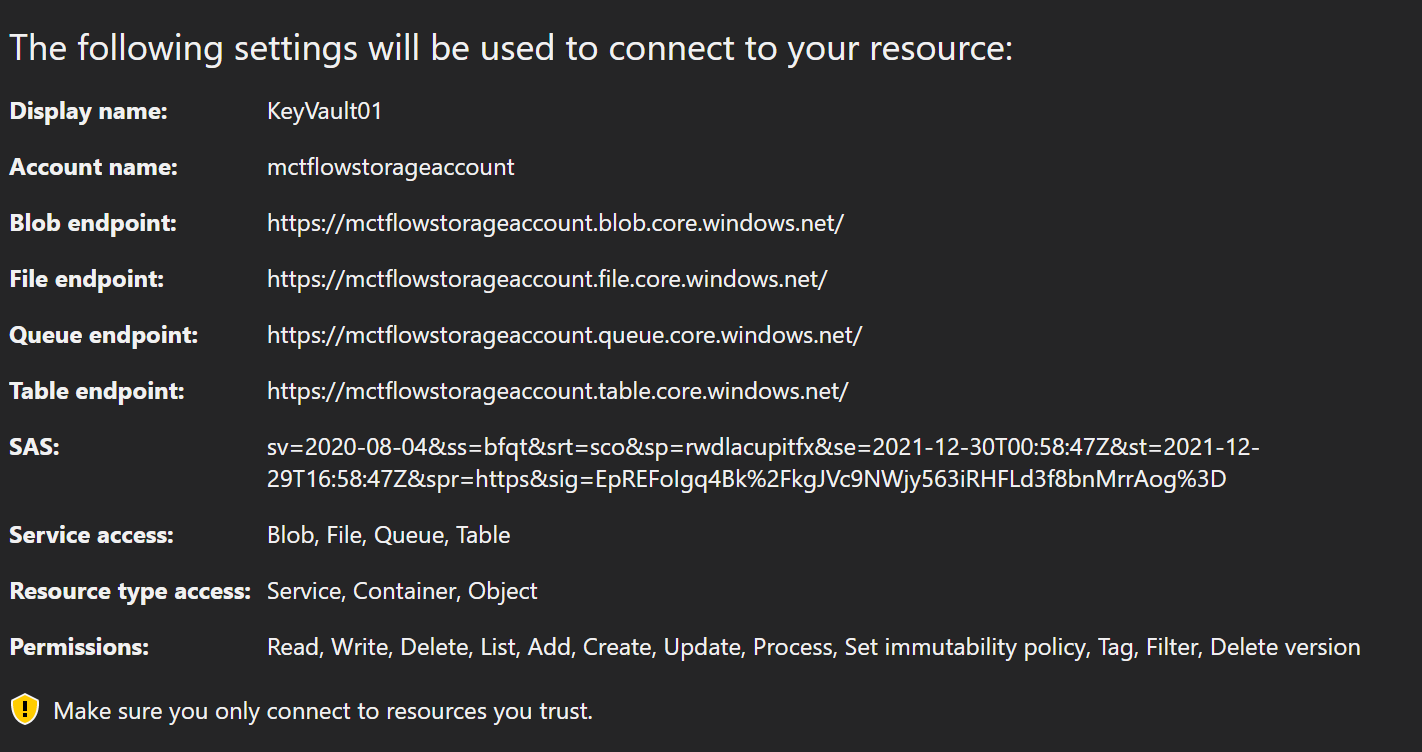
And you can see the services under the connection we just made.
Access Keys
Access keys authenticate your applications’ requests to this storage account. Keep your keys in a secure location like Azure Key Vault, and replace them often with new keys. The two keys allow you to replace one while still using the other.
You have two keys.
And again you can connect to the Storage Account with the key and name of the account, like this.
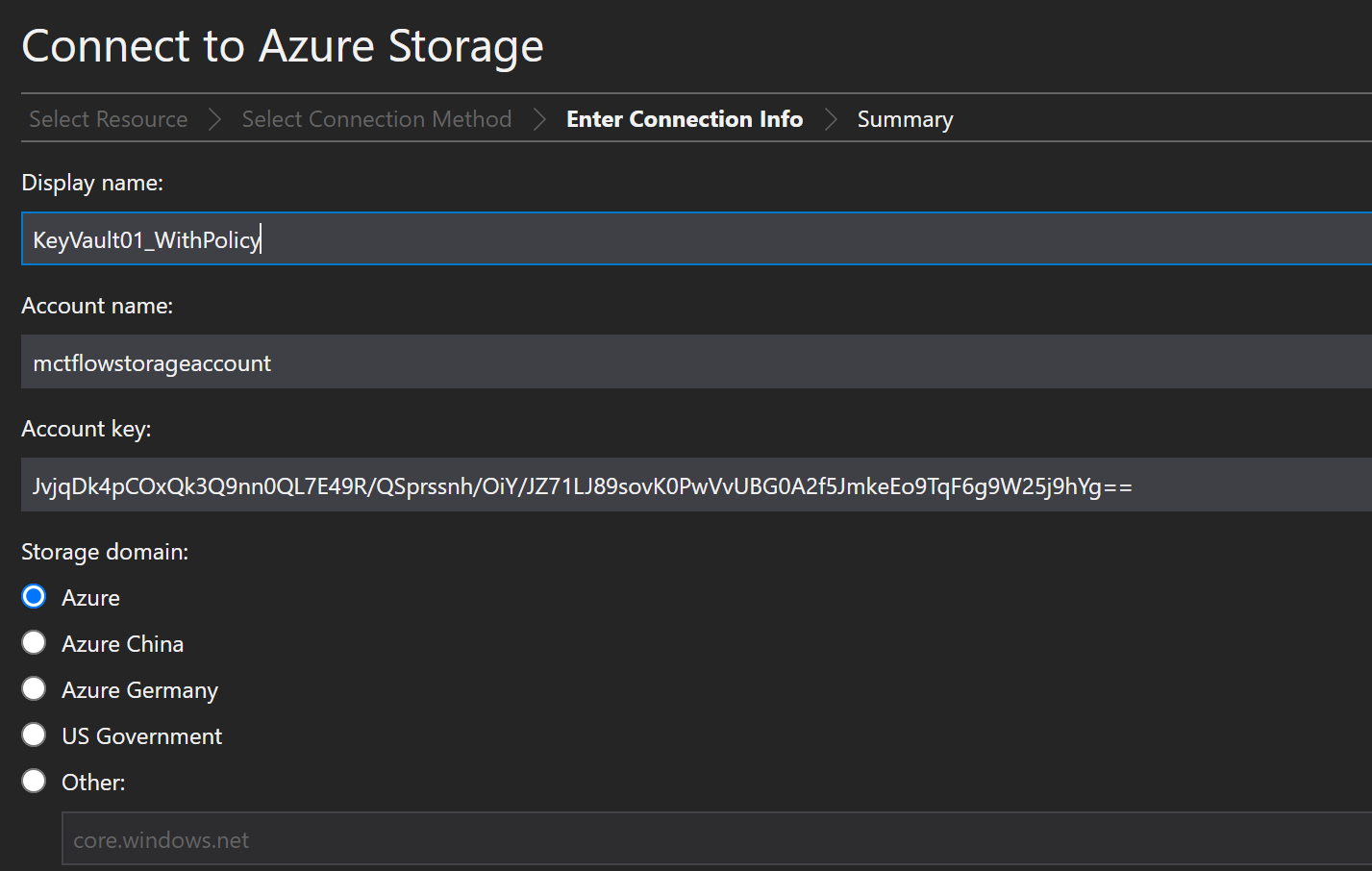
Verify settings and connect.
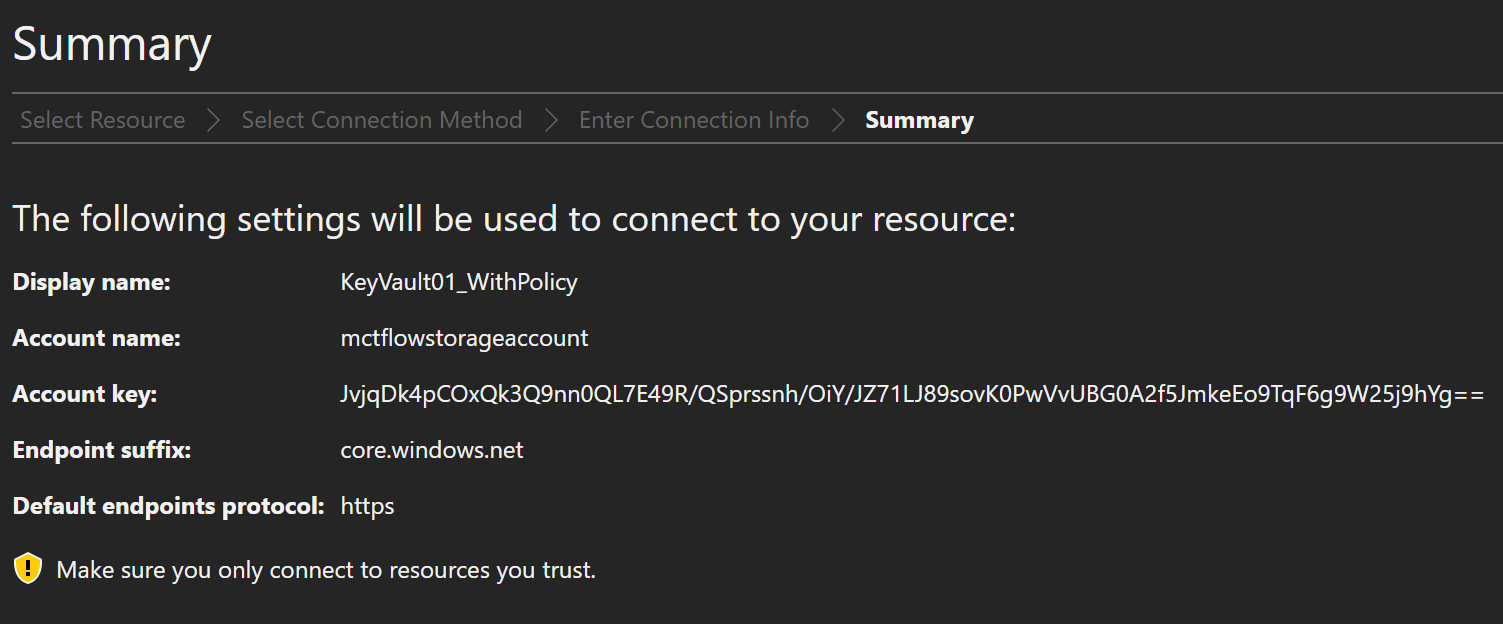
Now you can see the connection we just made in the Explorer.
Shared Access Tokens
A shared access signature (SAS) is a URI that grants restricted access to an Azure Storage container. Use it when you want to grant access to storage account resources for a specific time range without sharing your storage account key.
You can find the Access tokens under the corresponding service but not Azure Files, there is an preview for a feature that allows you to add Azure AD users directly to Azure Files, yes without Azure Domain Services.

Create an Azure file share with Azure Active Directory (preview)
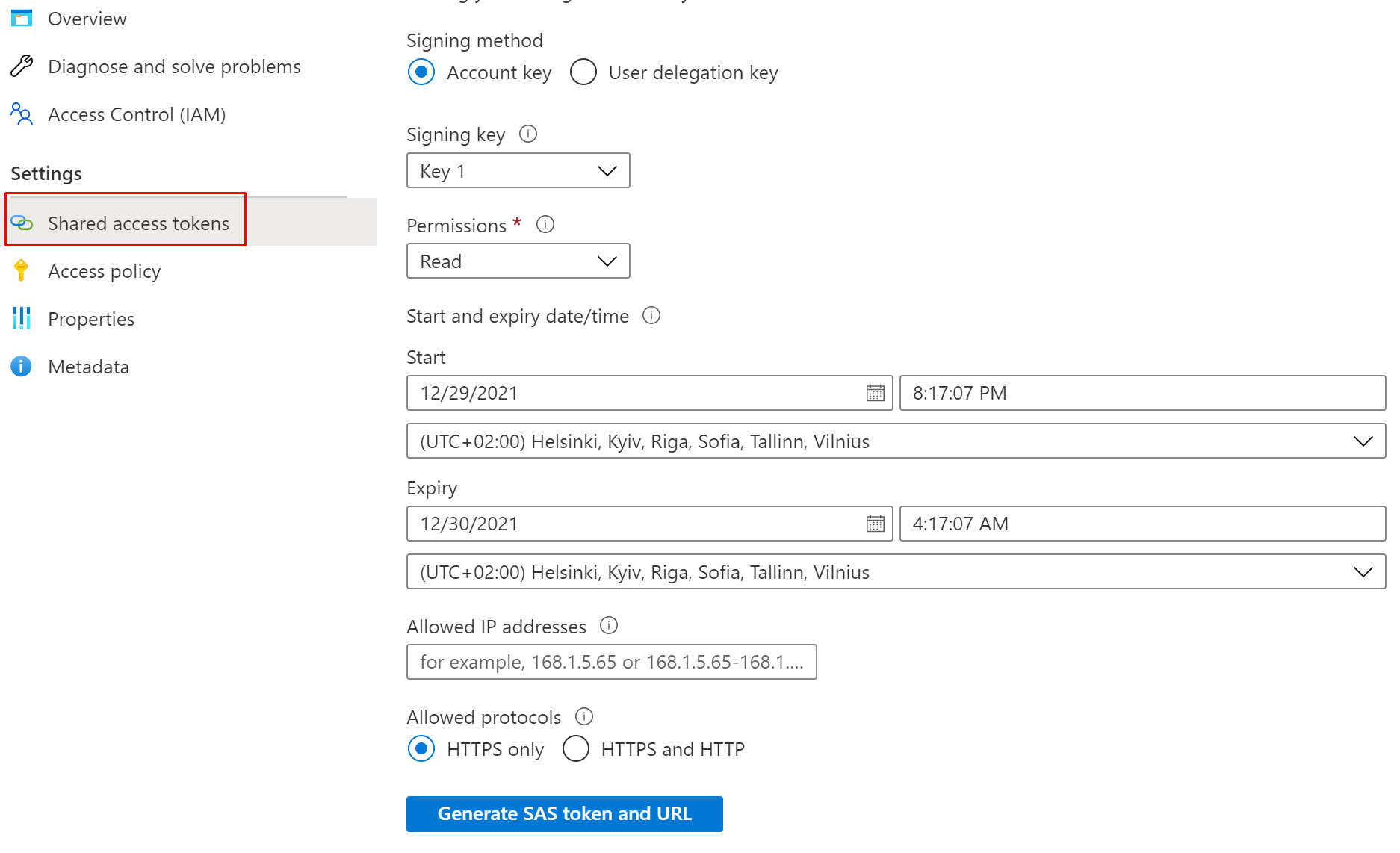
Generating the token is the same as with the Connection string so I won't be going thru this one.
Access policy
You can also allow access to specific services with Access policies.
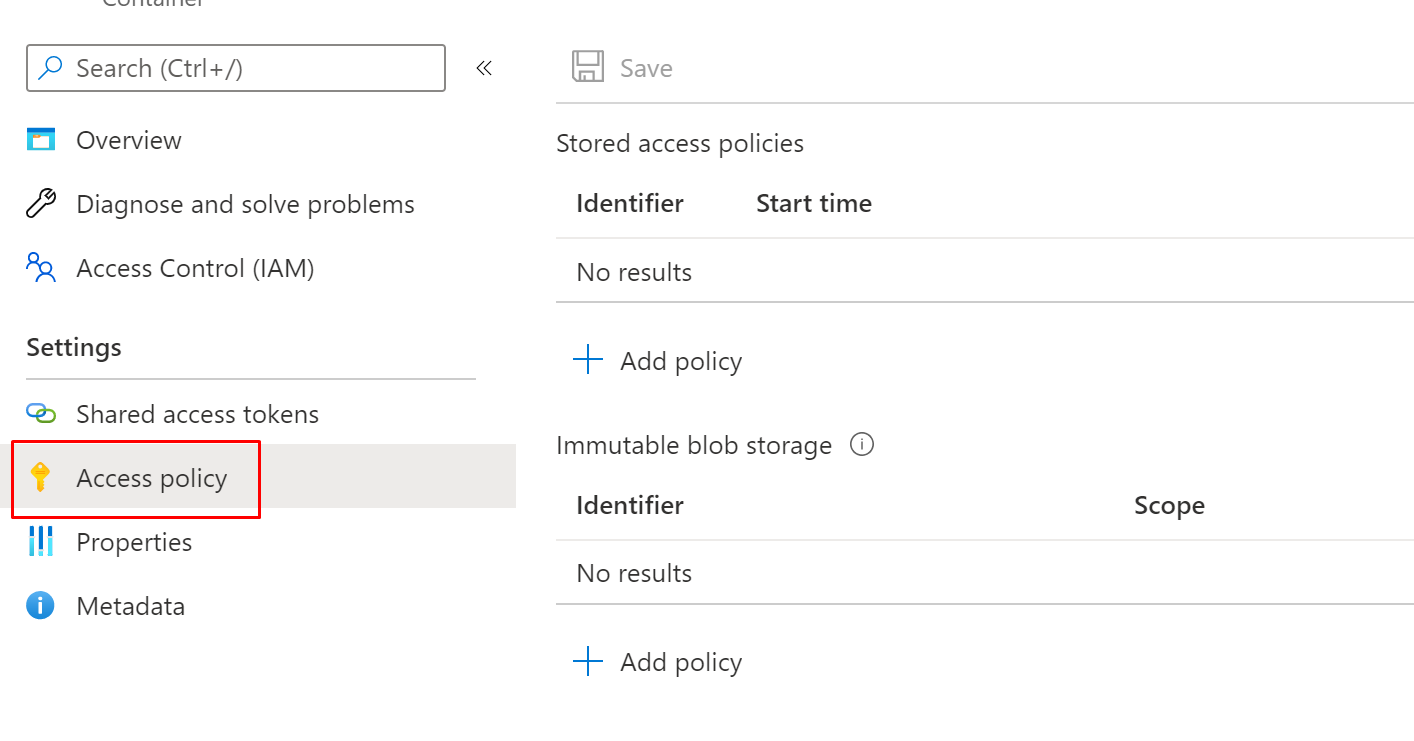
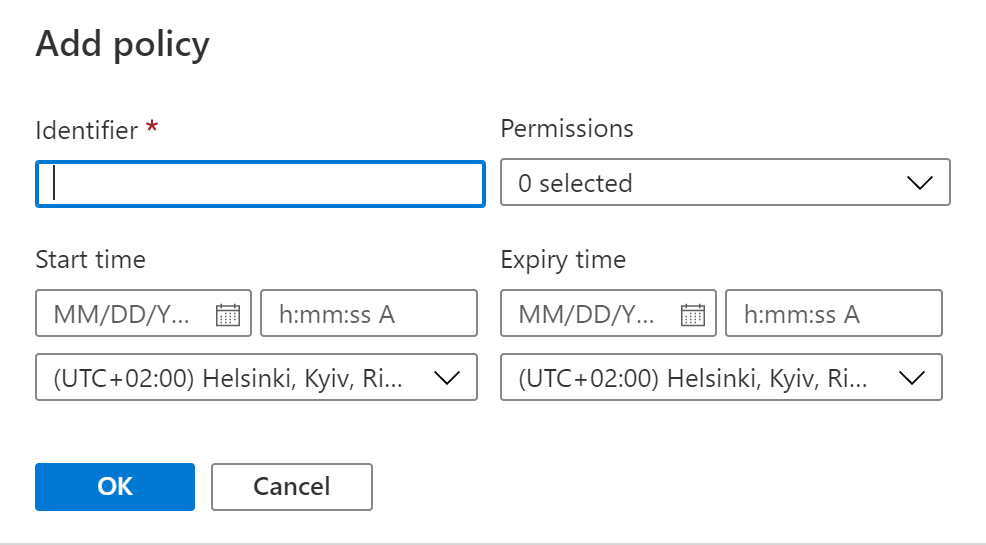
When you click Add policy you will get almost the same options than with Access keys.
You can add permissions and time limit for the policy.
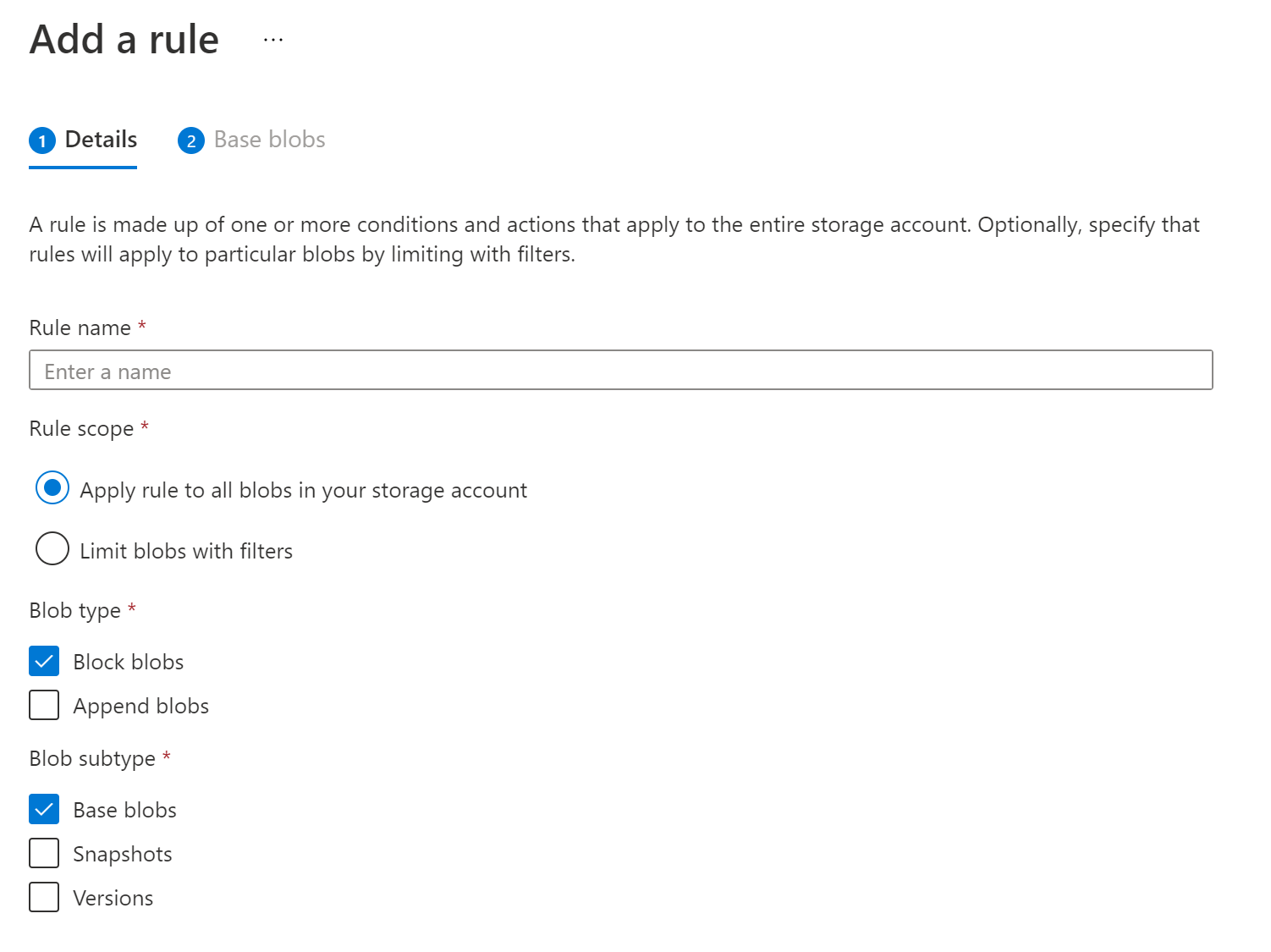
Lifecycle management
With the lifecycle management policy, you can:
- Transition blobs from cool to hot immediately when they are accessed, to optimize for performance.
- Transition blobs, blob versions, and blob snapshots to a cooler storage tier if these objects have not been accessed or modified for a period of time, to optimize for cost. In this scenario, the lifecycle management policy can move objects from hot to cool, from hot to archive, or from cool to archive.
- Delete blobs, blob versions, and blob snapshots at the end of their lifecycles.
- Define rules to be run once per day at the storage account level.
- Apply rules to containers or to a subset of blobs, using name prefixes or blob index tags as filters.
Geo-replication
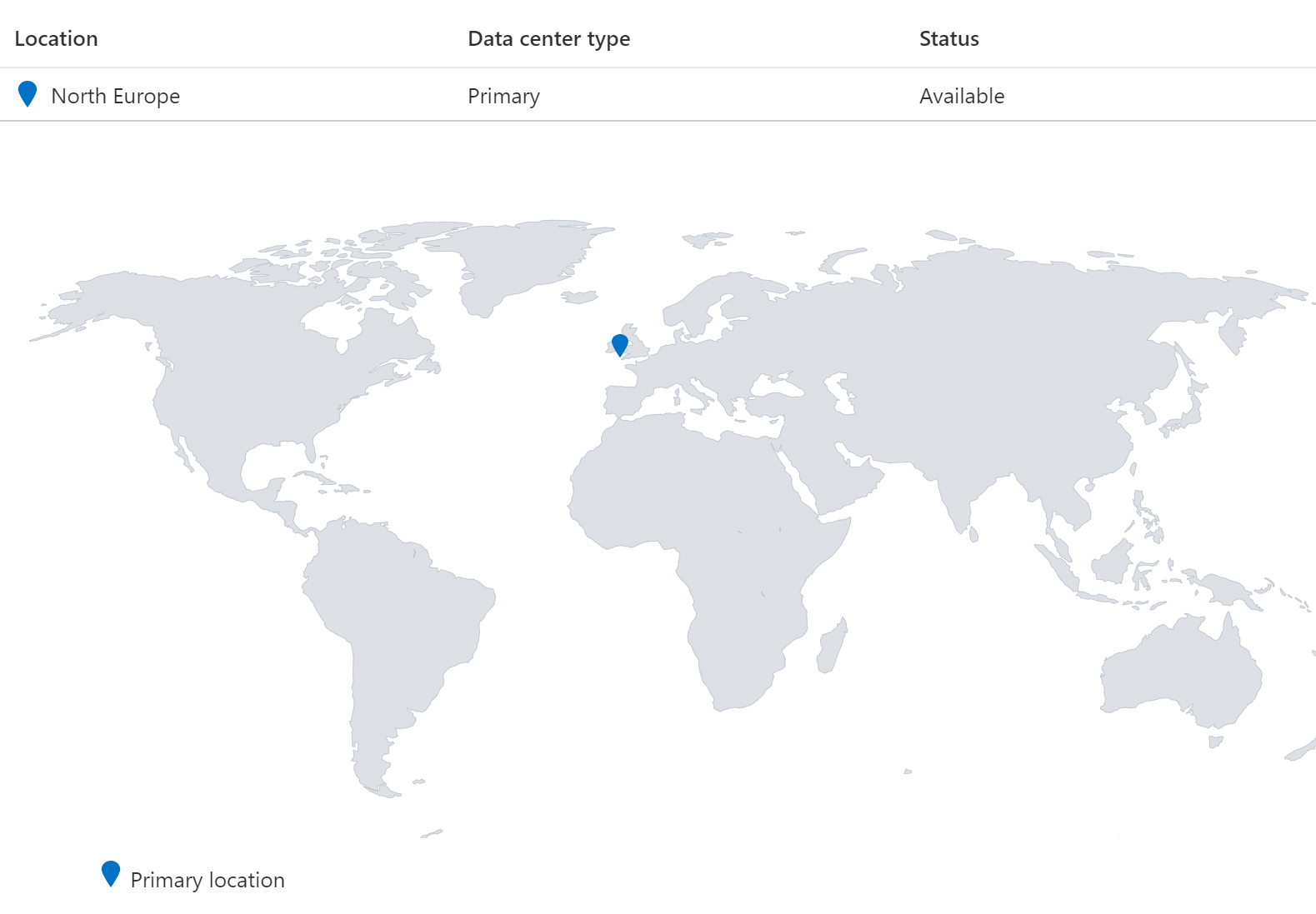
You can enable your geo-replication inside the configuration.
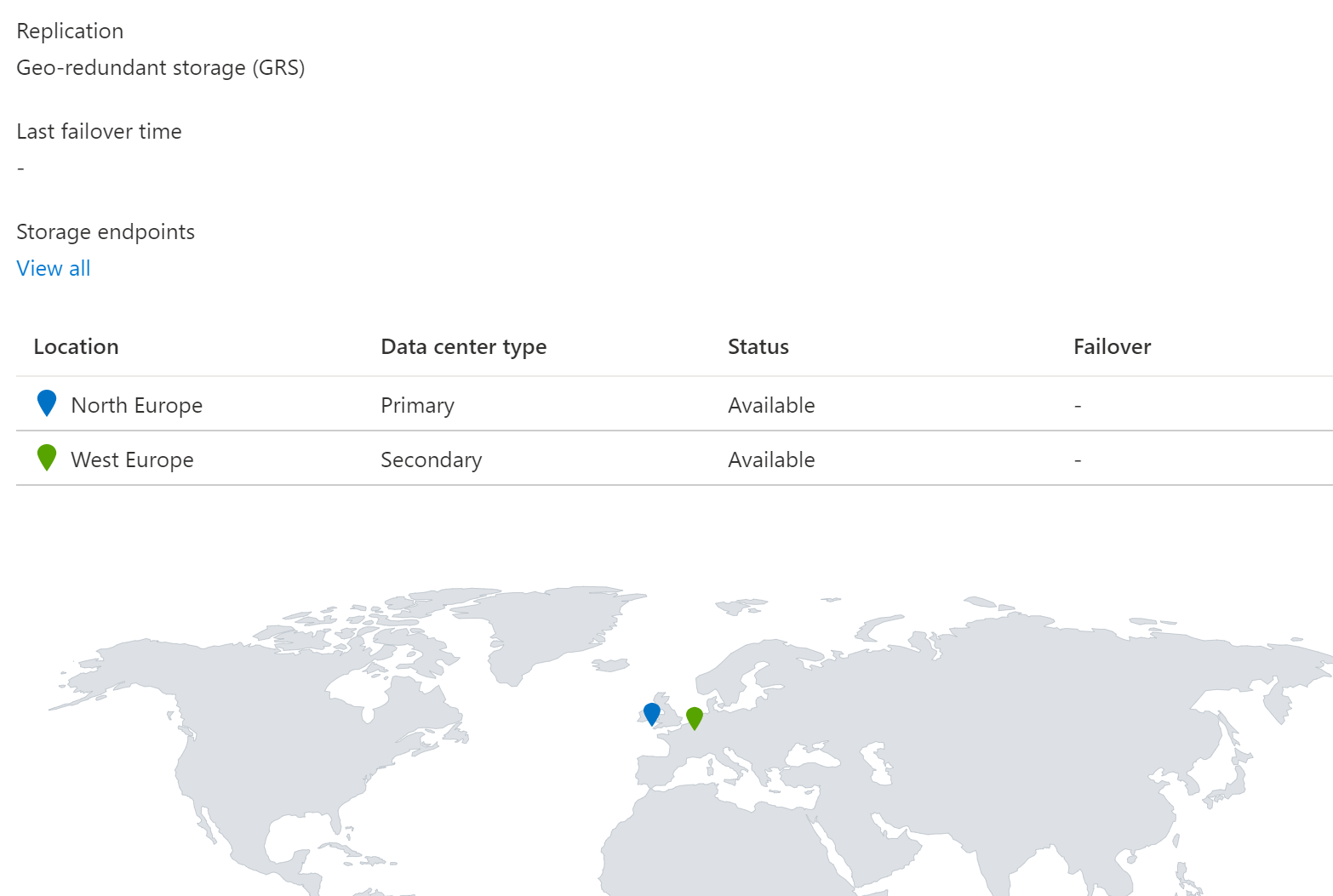
And now you can see two different Data centers inside the geo-replication.
Closure
In my example we connected with Azure Storage Explorer but you can do it also directly from your application or from different services.
Microsoft has a vast variety of services available inside Storage Accounts and in the next part I will show the security aspect that you must do with these publicly available services to protect them.
