Section 3 - Manage application access
How to manage custom roles?
First open Your Azure CLI.
And type az to start CLI.
Listing custom roles
Find out the current custom roles with.
az role definition list --custom-role-only true --output json --query '.{roleName:roleName, roleType:roleType}'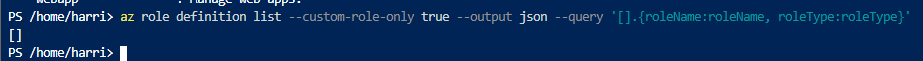
And we have none, so let's create one.
Creating custom role
First we need to create a JSON file, for this what would be a better tool than Visual Studio Code for the Web
Figuring out what resource providers to use.
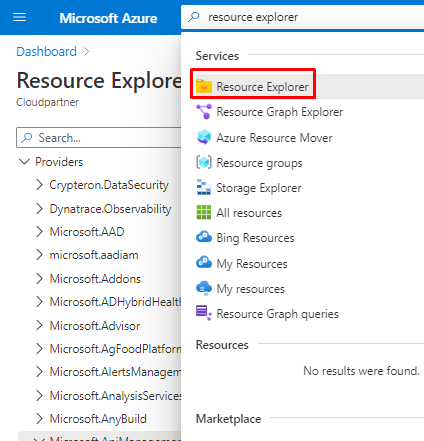
Microsoft has an excellent resource to browse thru different resources and it's called Resource Explorer.
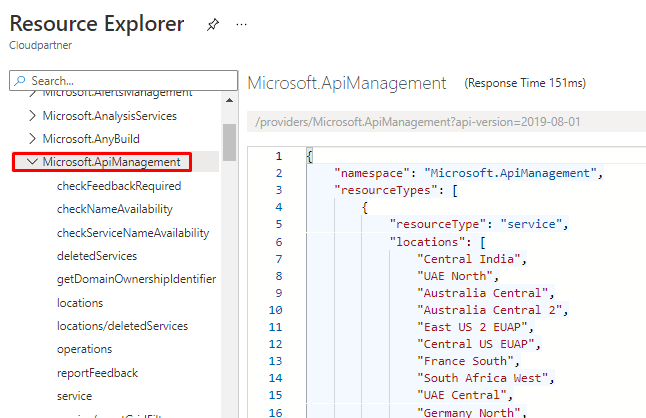
Let's find Microsoft.ApiManagement provider.
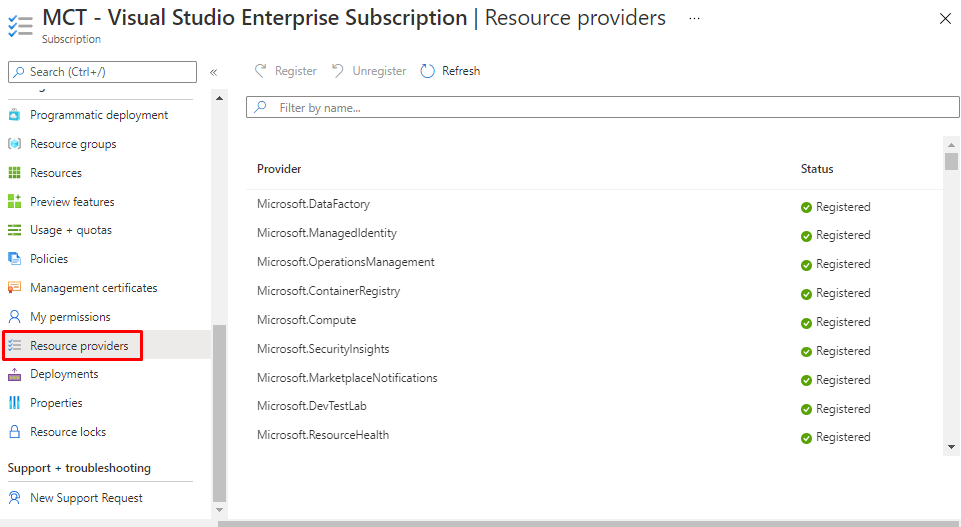
Enabling resource providers
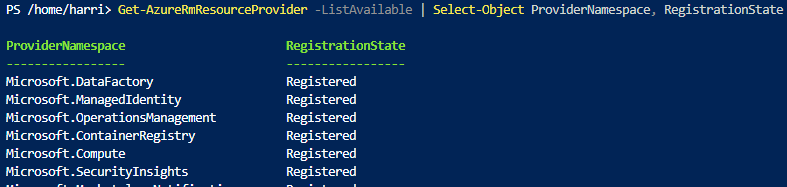
You can check what resource providers have been registered from GUI and register them.
With Shell.
Get-AzureRmResourceProvider -ListAvailable | Select-Object ProviderNamespace, RegistrationState
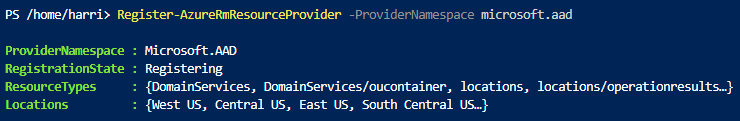
And register a provider.
Register-AzureRmResourceProvider -ProviderNamespace microsoft.aad
Creating JSON
First we need to find Your subscription ID You are currently logged in:
az account show --query id --output tsv
Or all subscription You have:
az account list --output table
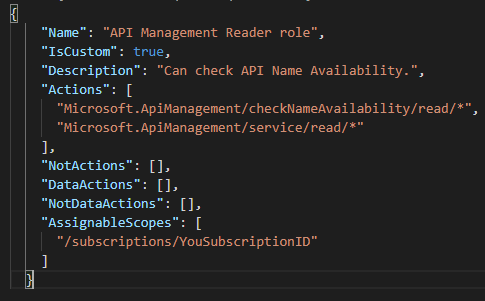
And then we construct the JSON file.
{ "Name": "API Management Reader role", "IsCustom": true, "Description": "Can check API Name Availability.", "Actions": , "NotActions": , "DataActions": , "NotDataActions": , "AssignableScopes": }Uploading JSON
Open Upload / Download file menu from Shell.
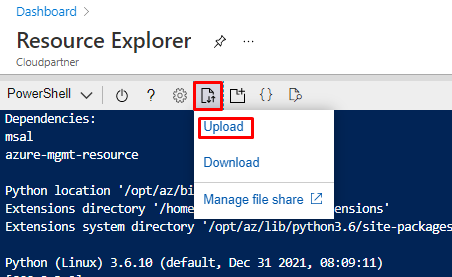
And Upload Your JSON file.
And the file is there.
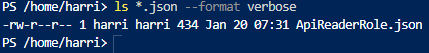
Creating a role based on JSON
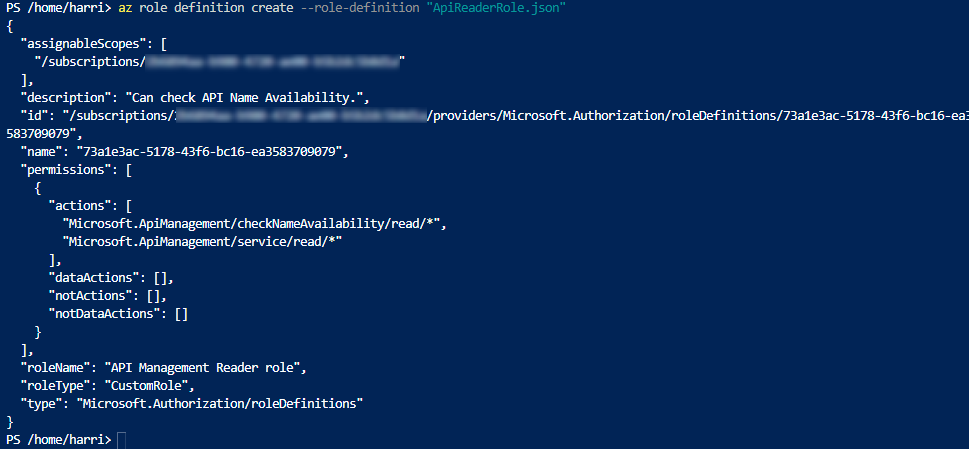
Create new custom role with the following.
az role definition create --role-definition "ApiReaderRole.json"
And You will see output for the command.
Querying the custom role
With the following command You can find Your custom role and display only Rolename and RoleType columns.
az role definition list --custom-role-only true --output json --query '.{roleName:roleName, roleType:roleType}'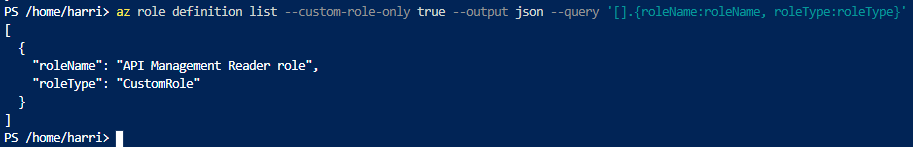
Or find the Custom role with GUI.
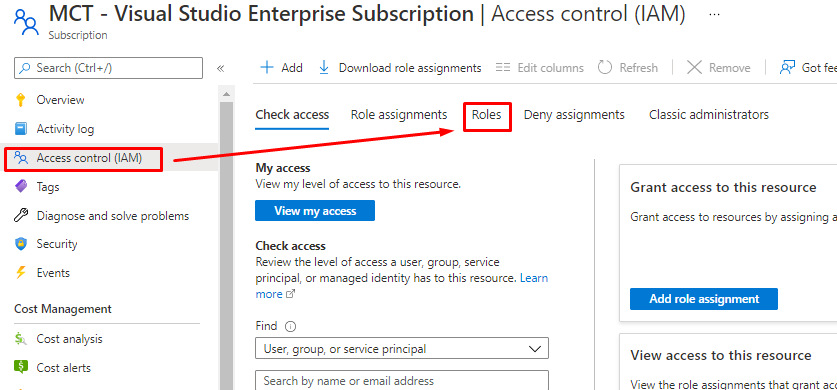
And select only Custom roles.
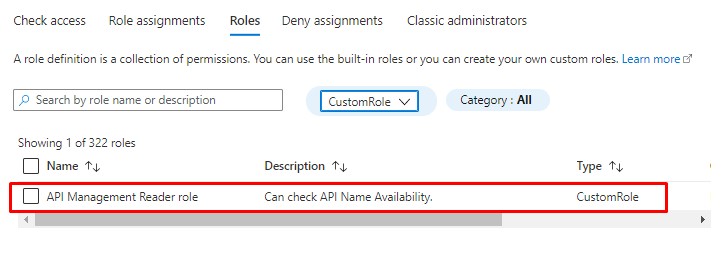
Adding a role assignment
You can now add the created Custom role to identities.
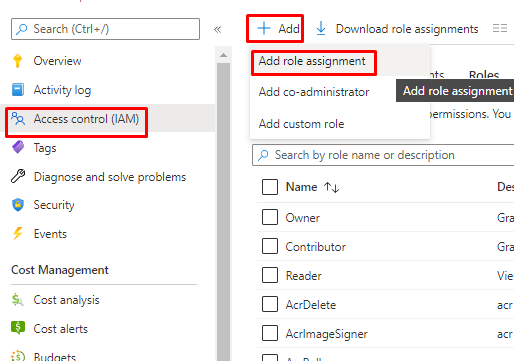
You can choose Users or Managed identities.
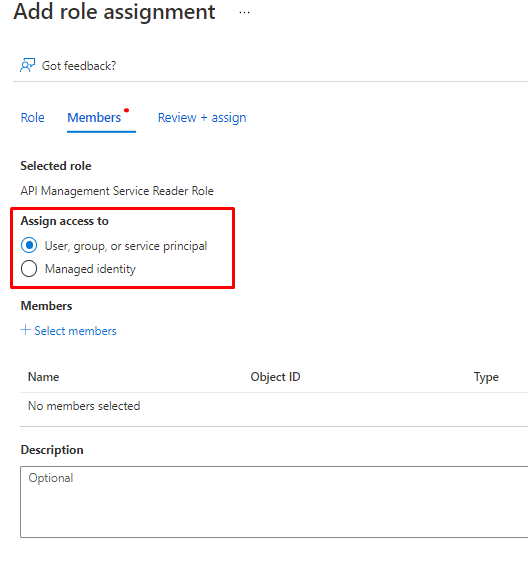
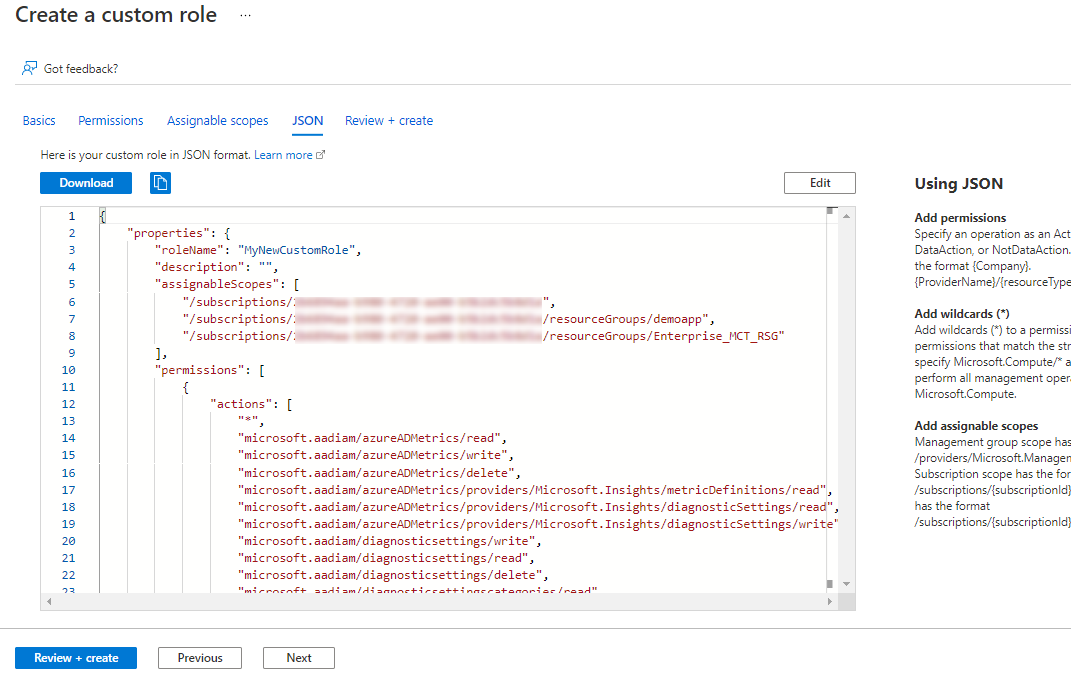
And you can also create the Custom role from GUI with cloning an existing role, Creating from Scratch or from JSON.
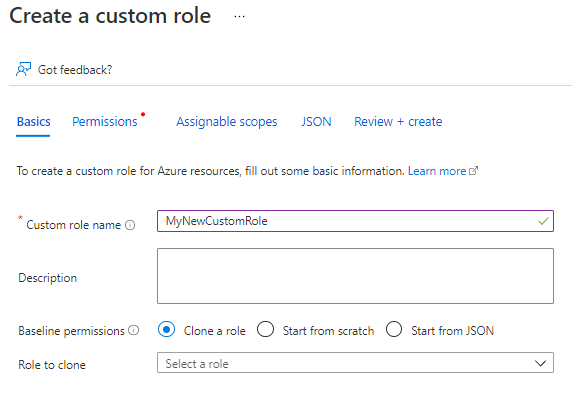
With cloning You can select any existing role and copy it to a Custom role.
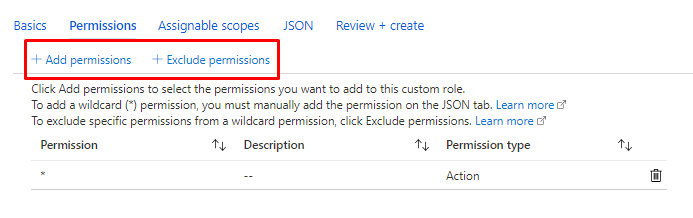
You can add or exclude permissions.
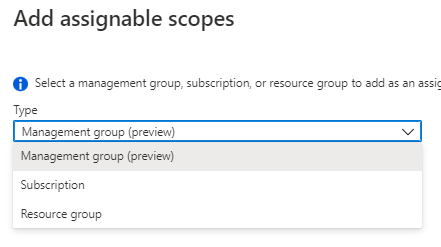
And add Assignable scopes. Management group is still in preview so it won't be coming to the test but it's a nice feature.
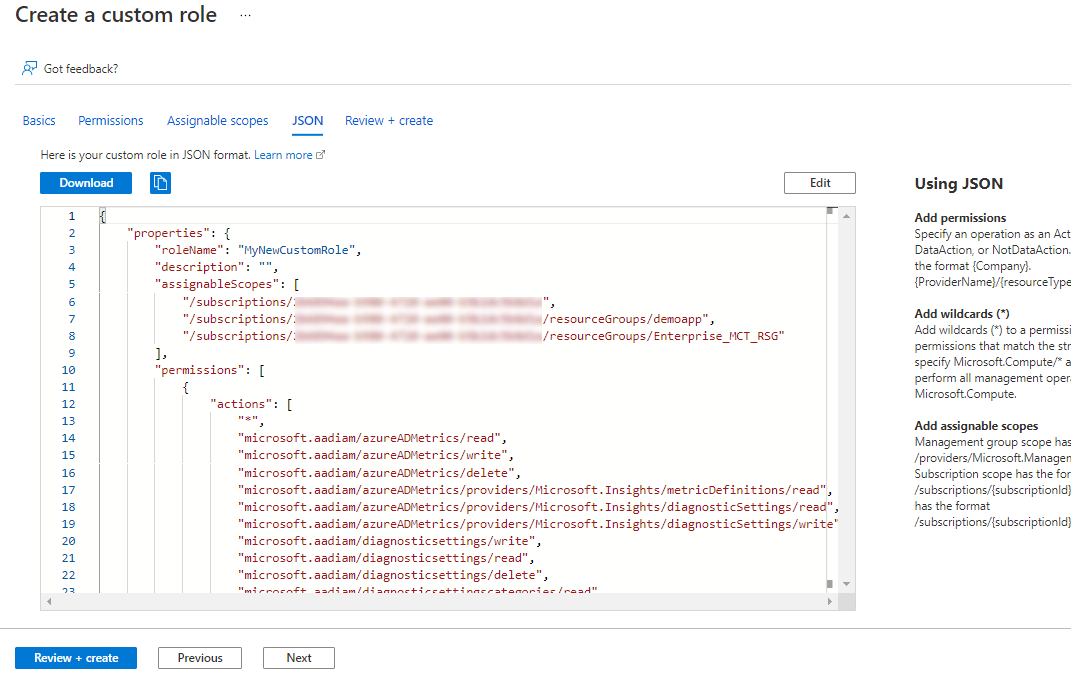
And when You select what You want, You will get a freshly created JSON. How cool is that!
Configure an authentication method for a service principal
What is a Service Principal?
Automated tools that use Azure services should always have restricted permissions. Instead of having applications sign in as a fully privileged user, Azure offers service principals.
An Azure service principal is an identity created for use with applications, hosted services, and automated tools to access Azure resources. This access is restricted by the roles assigned to the service principal, giving you control over which resources can be accessed and at which level. For security reasons, it's always recommended to use service principals with automated tools rather than allowing them to log in with a user identity.
Creating Service Principal
PowerShell with pre-hydrated password
You can create a Service principal with PowerShell.
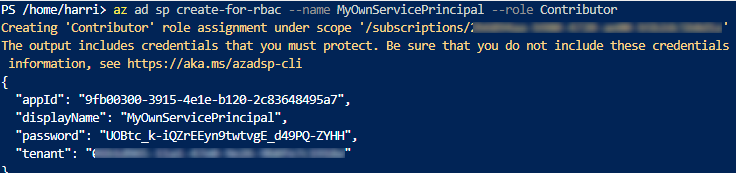
az ad sp create-for-rbac --name MyOwnServicePrincipal --role Contributor
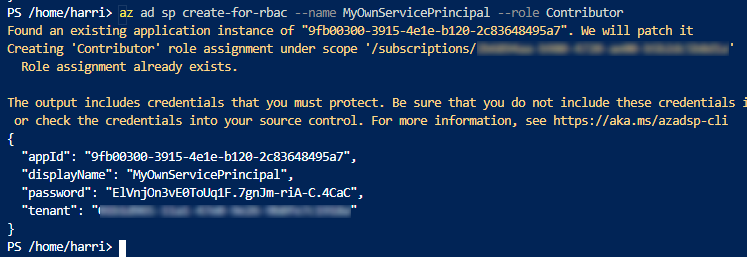
Running the command again will patch the existing Application instance.
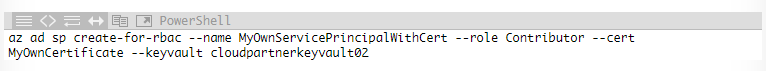
PowerShell with Certificate
You can have Your own certificate for this but You can also use one from Key Vault.
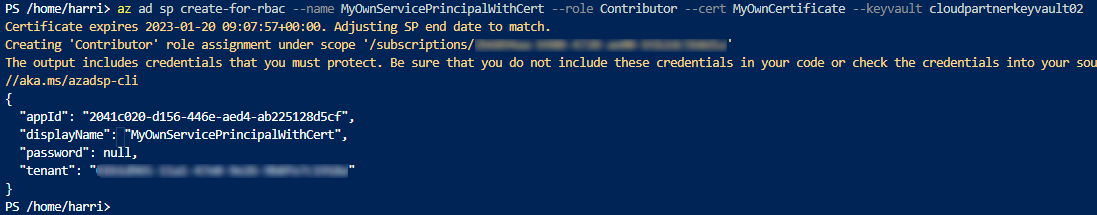
az ad sp create-for-rbac --name MyOwnServicePrincipalWithCert --role Contributor --cert MyOwnCertificate --keyvault cloudpartnerkeyvault02
And this is the output.
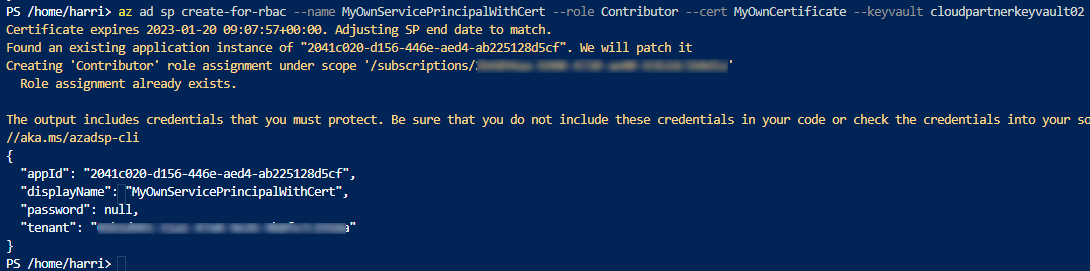
If You run the command again, it will patch Application instance.
If You choose Your own certificate it has to be in an ASCII format such as PEM, CER, or DER. Pass the certificate as a string, or use the @path format to load the certificate from a file. Make sure any tool that uses this service principal has access to the certificate's private key.
Listing Service Principal roles
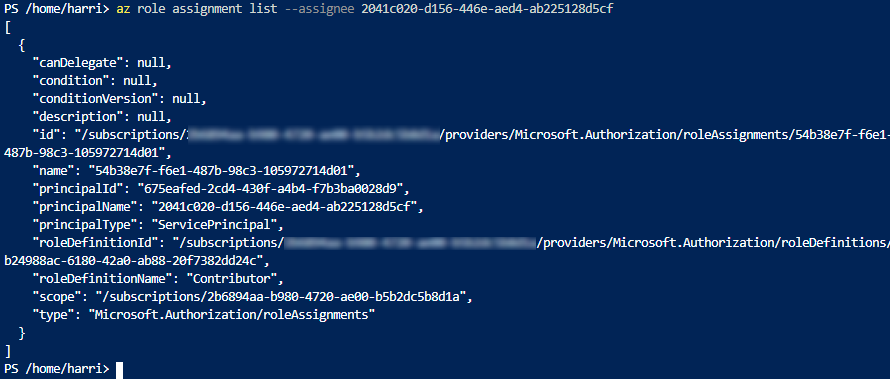
You can list the roles with the following. Note that You have to use AppID from the Service Principal.
az role assignment list --assignee 2041c020-d156-446e-aed4-ab225128d5cf
And the output.
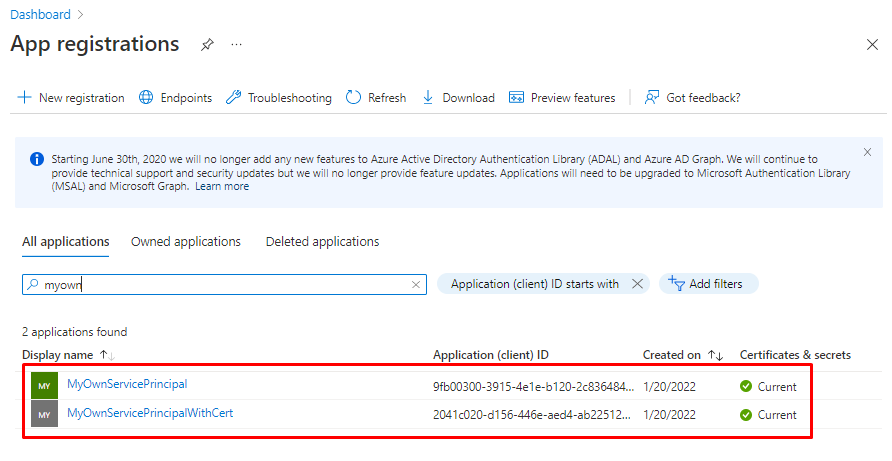
Adding permissions to Service Principal
Open App registrations and find Your Service Principals.
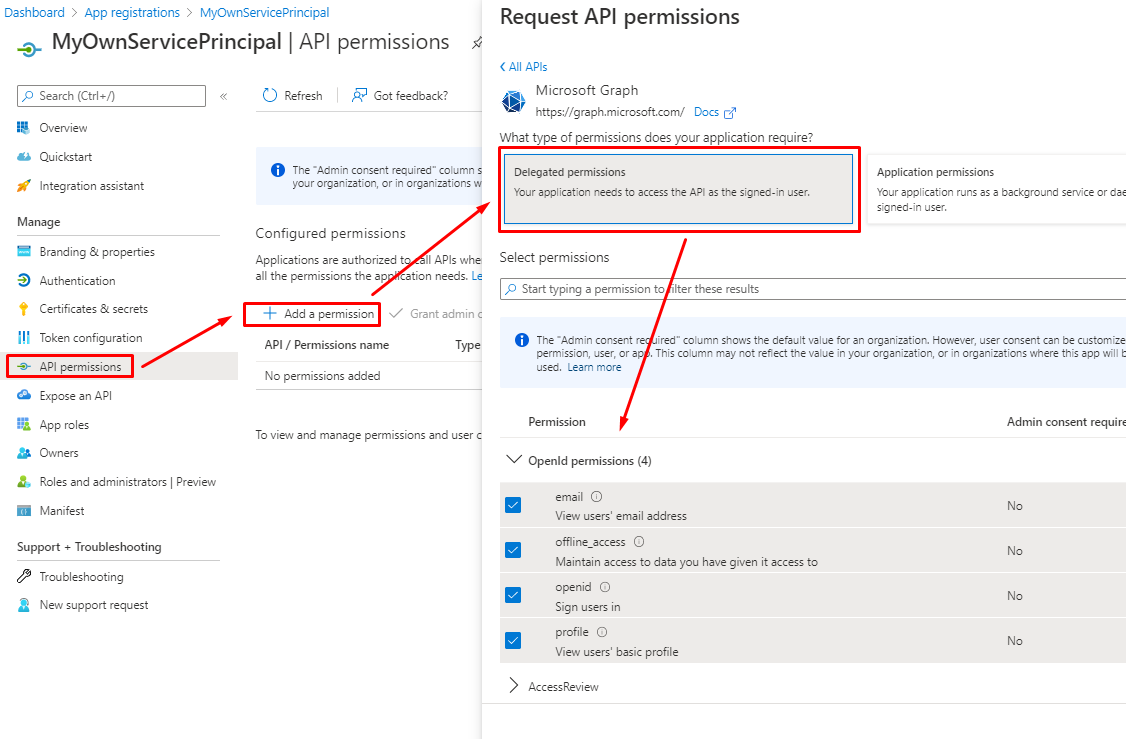
Add permissions like in last post for any App registration.
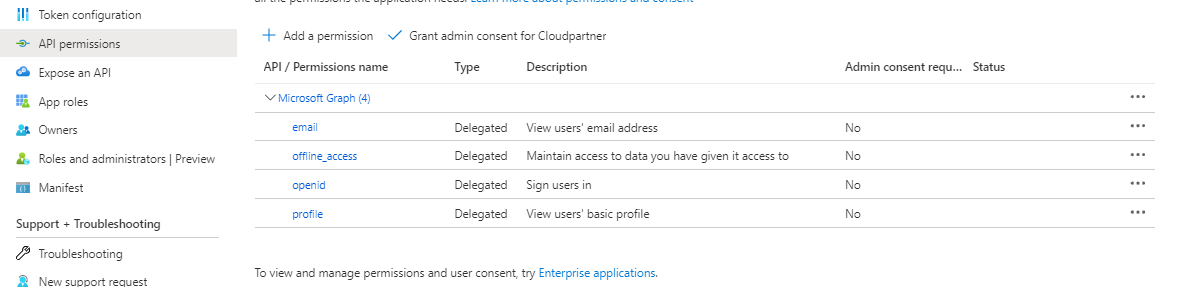
And the permissions appear to the list.
Thing to remember
You can create Custom roles by cloning an existing role, Creating from Scratch or from JSON.
Service Principal is an App registration
JSON format and what are actions You have to have and what scope could assigned. For the scopes You also assign Resource groups not only the whole Subscription.
Authentication can be done with a Pre-hydrated password or certificate (Remember Keyvault)
Remember Az role commands.
| az role assignment | Manage role assignments. |
| az role assignment create | Create a new role assignment for a user, group, or service principal. |
| az role assignment delete | Delete role assignments. |
| az role assignment list | List role assignments. |
| az role assignment list-changelogs | List changelogs for role assignments. |
| az role assignment update | Update an existing role assignment for a user, group, or service principal. |
| az role definition | Manage role definitions. |
| az role definition create | Create a custom role definition. |
| az role definition delete | Delete a role definition. |
| az role definition list | List role definitions. |
| az role definition update | Update a role definition. |