Power Platform and customer-managed encryption key (preview) with some HSM
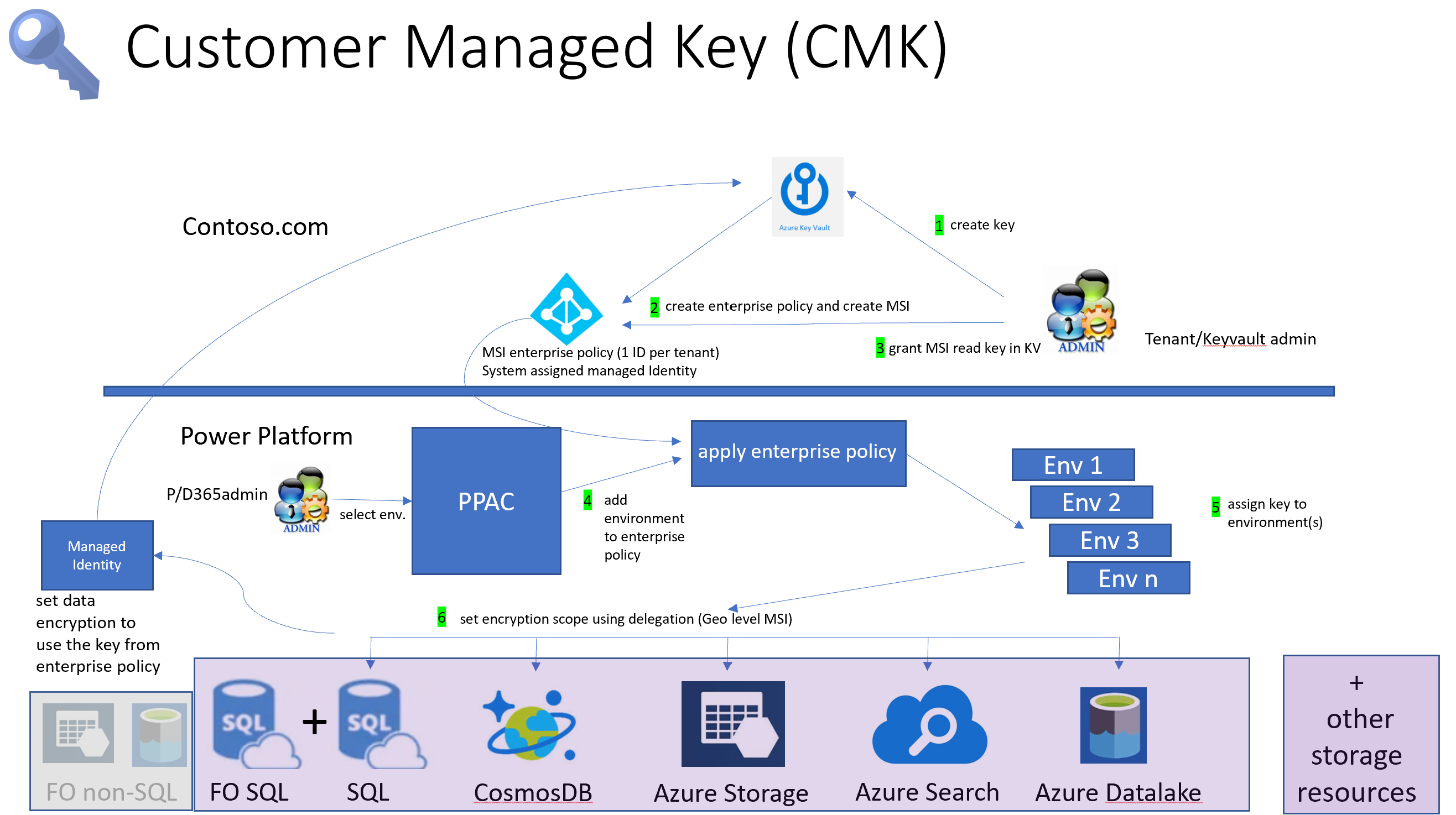
This is huge for all the Power Platform users. Now you can use Key vault to store your key, if you aren't familiar with concept of Key vault, let me open it a bit.
What features will be supported?
Power Platform stores all client data using strong encryption keys that are handled by Microsoft by default. You don't have to since Microsoft saves and maintains the database encryption key for all of your data. But Power Platform offers this customer-managed encryption key (CMK) for further data protection control, allowing you to manage the database encryption key connected to your Microsoft Dataverse environment on your own.
- Dataverse (Custom solutions and Microsoft services)
- Chat for Dynamics 365
- Dynamics 365 Sales
- Dynamics 365 Customer Service
- Dynamics 365 Customer Insights
- Dynamics 365 Omnichannel
- Dynamics 365 Commerce (Finance and operations)
- Dynamics 365 Field Service
- Dynamics 365 Retail
- Dynamics 365 Finance (Finance and operations)
- Dynamics 365 Intelligent Order Management (Finance and operations)
- Dynamics 365 Project Operations (Finance and operations)
- Dynamics 365 Supply Chain Management (Finance and operations)
- Dynamics 365 Fraud Protection (Finance and operations)
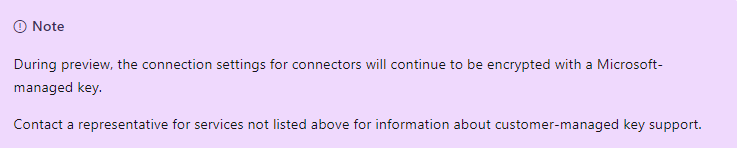
And that Key vault need to open during the preview period, be sure that you close it down from Internet as soon as it's possible!
Setup
First you have to enable Enterprise policies to your subscription, easiest way is to use AZ CLI for, just open that prompt and switch to Bash mode.
Resource providers
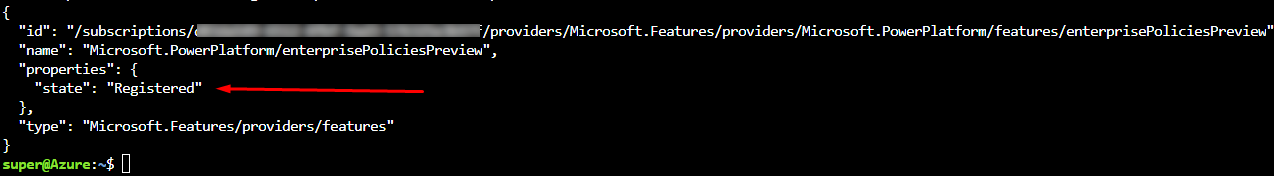
Run the following commands
# Login with device code az login # Get Azure Subscription ID subscriptionId=$(az account show --query id -o tsv) # Register Microsoft.PowerPlatform provider az provider register --namespace 'Microsoft.PowerPlatform' # Enable Enterprise policy with rest call az rest --method post --uri https://management.azure.com/subscriptions/$subscriptionId/providers/Microsoft.Features/providers/Microsoft.PowerPlatform/features/enterprisePoliciesPreview/register?api-version=2014-08-01-preview
Once you run them , the result should like this
Key vault
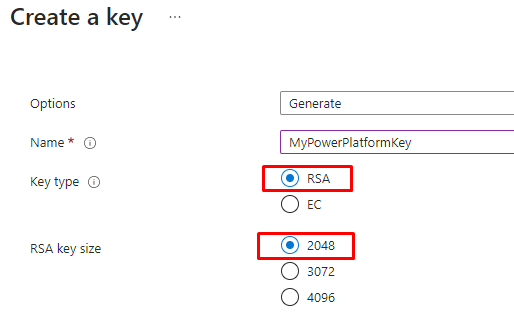
And you have to use either use RSA and the key size can only 2048
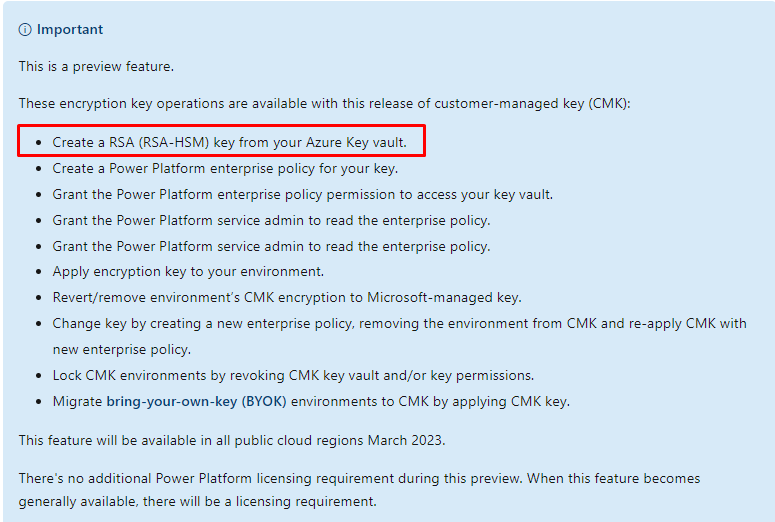
Or RSA-HSM , which translates that you need your own Managed HSM instance.
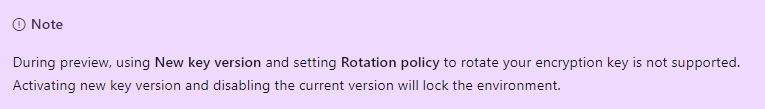
And note that auto-rotation isn't available during preview. Every time a new key is generated the environment will be locked. During the preview you can only add Sandbox environments
See the full Learn article to try it ourself, once this will be generally available, it will great feature to use, now there are still many limitations to it.

Manage your customer-managed encryption key in Power Platform - Power Platform
Migrate from BYOK (preview)
Another great feature is that you can migrate from Bring Your Own Key to CMK, greatness all the way!
See from Learn

Migrate from BYOK to self-managed key with Power Platform - Power Platform
So let's see what is Managed HSM, first it uses Key vault APIs to give access to Cloud native services, so it will differ from the Dedicated HSM solutions with that integration.
What is Managed HSM?
Each HSM pool is an isolated single-tenant instance with its own security domain providing complete cryptographic isolation from all other HSM's sharing the same hardware infrastructure.
Managed HSM uses Marvell LiquidSecurity adapters. So yes, you got it right. It is a Shared physical device and there is separate physical cards that hosts your content.
It has the following data-plane address.
| Resource type | Key protection methods | Data-plane endpoint base URL |
|---|---|---|
| Managed HSMs | HSM-protected | https://{hsm-name}.managedhsm.azure.net |
There are three different FIPS levels, and they are based on The Federal Information Security Management Act (FISMA), which was established as standards and guidelines for federal computer systems by the National Institute of Standards and Technology (NIST) and approved by the Secretary of Commerce. These standards and guidelines are developed when there are no existing industry standards or solutions that meet a certain regulatory requirement. FIPS were developed for use by the federal government, although many firms voluntarily adopt them. Managed HSM has the highest FIPS Level of 3.
You will use it almost like normal Key vault, once you have it provisioned you will see Managed HSM in the service that you plan to use the Keys. You can generate the keys with AZ CLI or with the GUI like below.
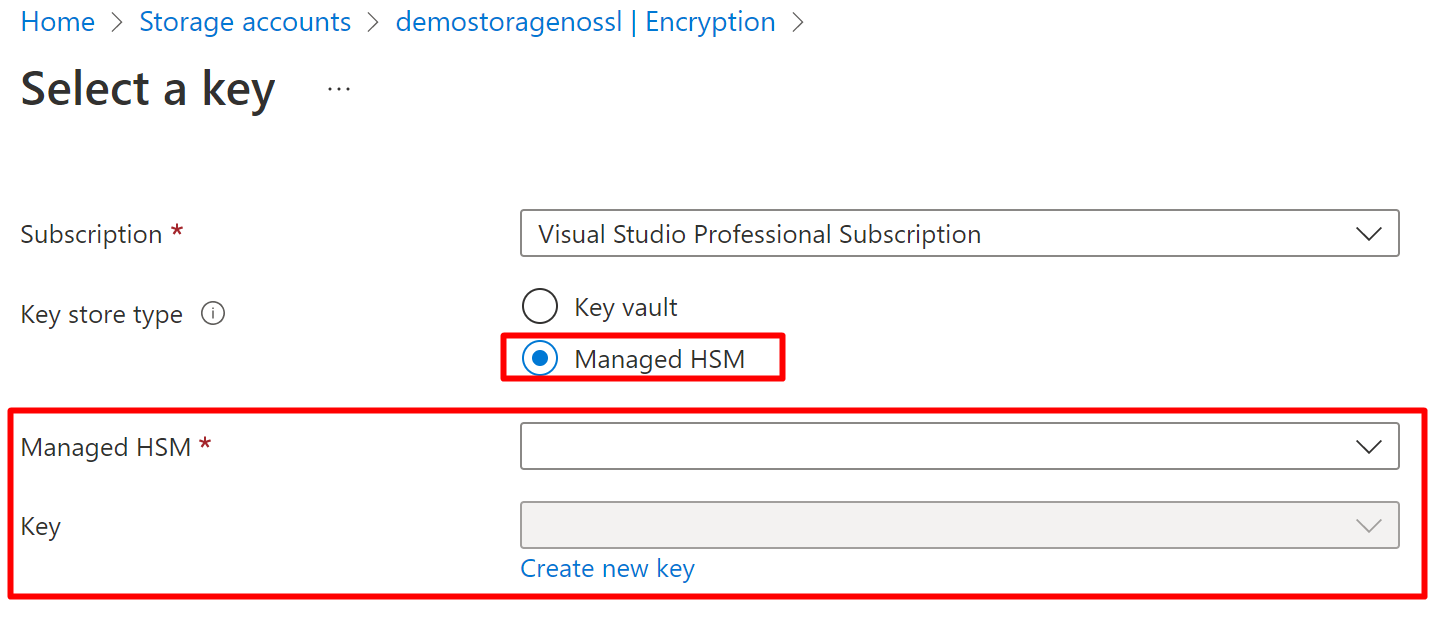
And when you have Managed HSM RSA key in place
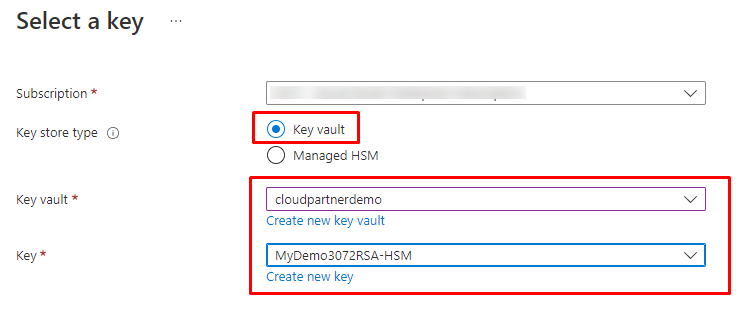
Why to use it?
Regulations and compliance based on our industry is one of the biggest reasons. Content has to encrypted with your own keys, that you generate and hold. With HSM you have the root of trust but also the responsibility to backup your infrastructure and content.
See some excellent examples from Azure Architecture Center for HSM deployments.

Browse Azure Architectures - Azure Architecture Center
Availability and pricing
Here you can find the availability
Azure Products by Region | Microsoft Azure
And pricing per B1 pool is 3,323€ per hour and for the keys.
| HSM-protected keys | Premium | |
| RSA 2048-bit keys | €1.039 per key per month1 + €0.032/10,000 transactions | |
| Advanced key types1— | First 250 keys | €5.192 per key per month |
| From 251 – 1500 keys | €2.596 per key per month | |
| RSA 3072-bit, RSA 4096-bit, and Elliptic-Curve Cryptography (ECC) keys | From 1501 – 4000 keys | €0.935 per key per month |
| 4001+ keys | €0.416 per key per month | |
| + €0.156/10,000 transactions |
If you are thinking about the Keys length, RSA-3072 is a safe choice to go with as it's the highest than can be used in all of the Azure services. Don't get me wrong, by best practices you should generate different
How to provision?
You don't find Managed HSM inside Azure Marketplace, it will be provisioned with Azure CLI
# Once connected to Azure CLI, login AZ login # Provision you HSM to your location az group create --name "HSMResourceGroup" --location northeurope # Getting the logged in user to $OID, add it as admin once provioning HSM oid=$(az ad signed-in-user show --query id -o tsv) az keyvault create --hsm-name "YouHSMName" --resource-group "HSMResourceGroup" --location "northeurope" --administrators $oid --retention-days 7 Note! Managed HSM instances are considered always-in-use. If you choose to enable purge protection using the --enable-purge-protection flag, you will be billed for the entirety of the retention period. # Generate three RSA-2048 certificates openssl req -newkey rsa:2048 -nodes -keyout cert_0.key -x509 -days 365 -out cert_0.cer openssl req -newkey rsa:2048 -nodes -keyout cert_1.key -x509 -days 365 -out cert_1.cer openssl req -newkey rsa:2048 -nodes -keyout cert_2.key -x509 -days 365 -out cert_2.cer # Download security domain (boundary) and Activate your HSM az keyvault security-domain download --hsm-name YouHSMName --sd-wrapping-keys ./certs/cert_0.cer ./certs/cert_1.cer ./certs/cert_2.cer --sd-quorum 2 --security-domain-file YourHSMName-SD.json
Managed HSM Key auto-rotation
And Key auto-rotation is generally available for Managed HSM, see more from Learn

Configure key auto-rotation in Azure Key Vault Managed HSM
And you need System-managed identities for the auto-rotation, so let's what it's about.
System-managed identities
Read more from my previous blogs on the Key vault auto-rotation feature and how to enable it with system-managed identities.
How to use Azure Key Vault with managed identities and generating keys with auto-rotation
Closure
So that's it, Key vault and Power Platform CMK is soon a reality, remember that Key vault and Managed HSM can be used in many different scenarios and is essential to build an highly regulated environment.
Key vault can be used in an completely isolated environments and it will provide you with safety of double RBAC access restriction, one with Azure RBAC and one with Managed HSMs own RBAC and it's isolated Security boundary.
