Microsoft Entra Verified ID went GA!
Back in 2018 Microsoft joined ID2020 alliance and started collaborating with Accenture and Avanade on a blockchain-based identity prototype for Azure. The intention was to give people means to identify them selves easily.

Partnering for a path to digital identity - The Official Microsoft Blog
And finally Yesterday Microsoft released the final product!

Microsoft Entra Verified ID now generally available
Entra Verified ID
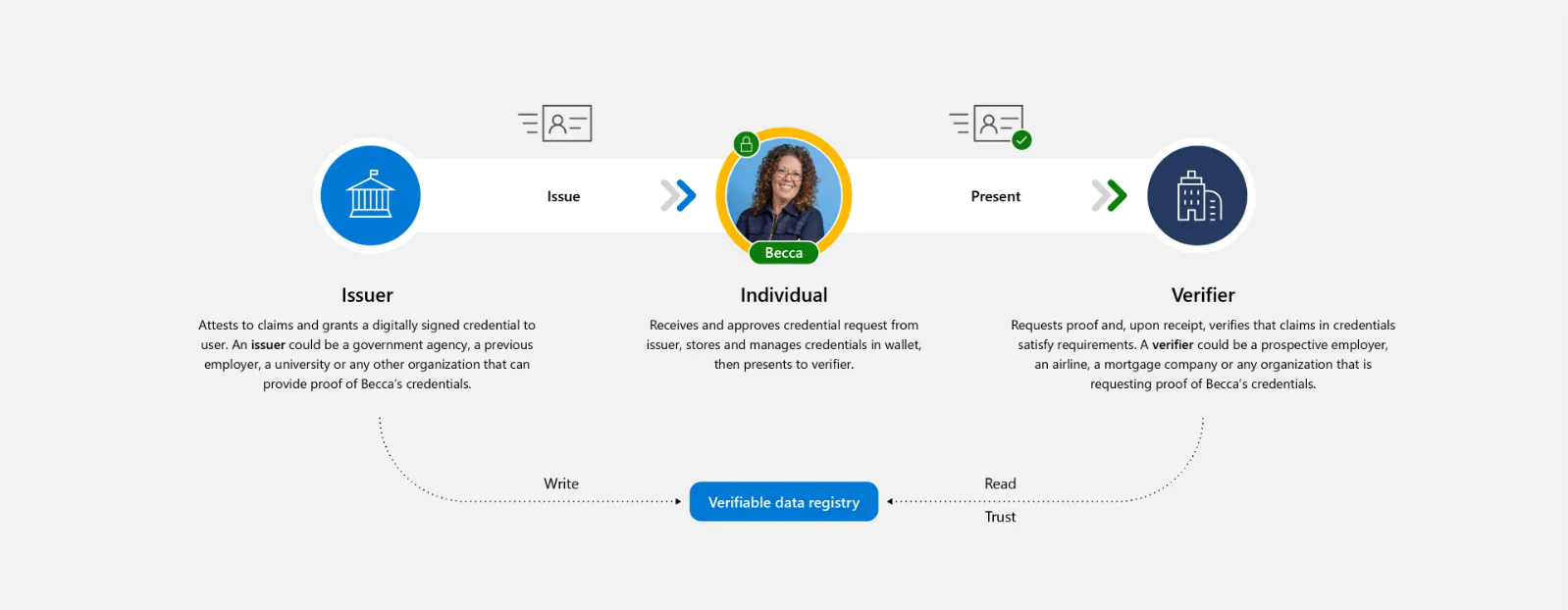
How does it work?
1. W3C Decentralized Identifiers (DIDs). IDs users create, own, and control independently of any organization or government. DIDs are globally unique identifiers linked to Decentralized Public Key Infrastructure (DPKI) metadata composed of JSON documents that contain public key material, authentication descriptors, and service endpoints.
2. Trust System. In order to be able to resolve DID documents, DIDs are typically recorded on an underlying network of some kind that represents a trust system. Microsoft currently supports two trust systems, which are:
- ION (Identity Overlay Network) ION is a Layer 2 open, permissionless network based on the purely deterministic Sidetree protocol, which requires no special tokens, trusted validators, or other consensus mechanisms; the linear progression of Bitcoin's time chain is all that's required for its operation. We have open sourced a npm package to make working with the ION network easy to integrate into your apps and services. Libraries include creating a new DID, generating keys and anchoring your DID on the Bitcoin blockchain.
- DID:Web is a permission based model that allows trust using a web domain’s existing reputation.
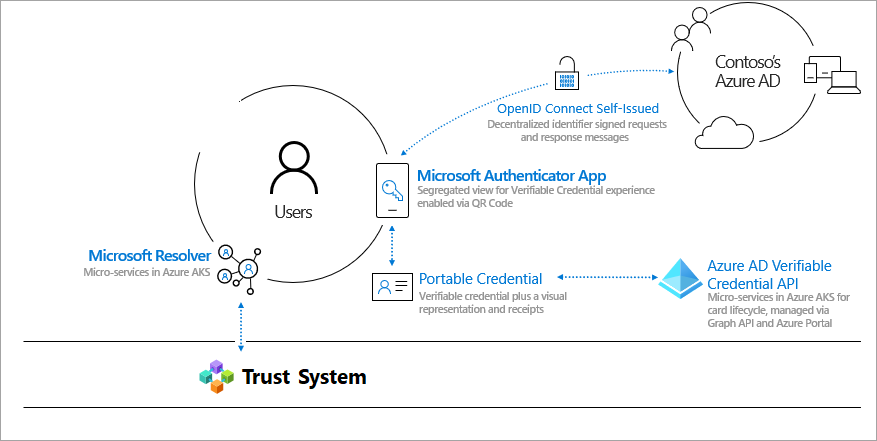
3. DID User Agent/Wallet: Microsoft Authenticator App. Enables real people to use decentralized identities and Verifiable Credentials. Authenticator creates DIDs, facilitates issuance and presentation requests for verifiable credentials and manages the backup of your DID's seed through an encrypted wallet file.
4. Microsoft Resolver. An API that connects to our ION node to look up and resolve DIDs using the did:ion method and return the DID Document Object (DDO). The DDO includes DPKI metadata associated with the DID such as public keys and service endpoints.
5. Azure Active Directory Verified Credentials Service. An issuance and verification service in Azure and a REST API for W3C Verifiable Credentials that are signed with the did:ion method. They enable identity owners to generate, present, and verify claims. This forms the basis of trust between users of the systems.
Customer example
Avanade reimagines access to training and skills management using Microsoft Entra Verified ID
Pricing
Customers can get started with Azure AD free and start using Entra Verified ID today.
Azure AD Premium license will be required for enterprise scale that has more than 50,00 transactions monthly.
If you are wondering what other limitations does Azure AD free and premiums have.

Service limits and restrictions - Azure Active Directory - Microsoft Entra
But when you get the premium version, you will also get more security features.
| Feature | Azure AD Free - Security defaults (enabled for all users) | Azure AD Free - Global Administrators only | Office 365 | Azure AD Premium P1 | Azure AD Premium P2 |
|---|---|---|---|---|---|
| Protect Azure AD tenant admin accounts with MFA | ● | ● (Azure AD Global Administrator accounts only) | ● | ● | ● |
| Mobile app as a second factor | ● | ● | ● | ● | ● |
| Phone call as a second factor | ● | ● | ● | ● | |
| SMS as a second factor | ● | ● | ● | ● | |
| Admin control over verification methods | ● | ● | ● | ● | |
| Fraud alert | ● | ● | |||
| MFA Reports | ● | ● | |||
| Custom greetings for phone calls | ● | ● | |||
| Custom caller ID for phone calls | ● | ● | |||
| Trusted IPs | ● | ● | |||
| Remember MFA for trusted devices | ● | ● | ● | ● | |
| MFA for on-premises applications | ● | ● | |||
| Conditional access | ● | ● | |||
| Risk-based conditional access | ● | ||||
| Identity Protection (Risky sign-ins, risky users) | ● | ||||
| Access Reviews | ● | ||||
| Entitlements Management | ● | ||||
| Privileged Identity Management (PIM), just-in-time access | ● |
Deployment
Scripted approach
Prerequisites
- If you don't have Azure subscription, create one for free.
- Sign up for Azure Active Directory Premium editions subscription in your tenant.
- Ensure that you have the global administrator permission for the directory you want to configure.
- Ensure that you have PowerShell 7.0.6 LTS-x64, PowerShell 7.1.3-x64, or later installed.
Create a Service Principal
Connect to to Azure AD with Connect-AzAccount -TenantId switch
If You will use Connect-AzAccount with out any switches, You will get an warning.
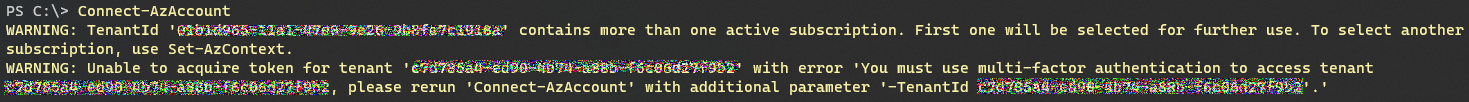
# These commands install and import the Az module if ((Get-Module -ListAvailable -Name "Az.Accounts") -eq $null) { Install-Module -Name "Az.Accounts" -Scope CurrentUser } if ((Get-Module -ListAvailable -Name "Az.Resources") -eq $null) { Install-Module "Az.Resources" -Scope CurrentUser } # Replace <your-tenant-ID> with your Azure AD tenant ID Connect-AzAccount -TenantId <your-tenant-ID> # The AppId bbb94529-53a3-4be5-a069-7eaf2712b826 refers to the Verifiable Credentials Microsoft service. New-AzADServicePrincipal -ApplicationId "bbb94529-53a3-4be5-a069-7eaf2712b826" -DisplayName "Verifiable Credential Request Service" # You can check the Enterprise application with the following get-AzADServicePrincipal -ApplicationId bbb94529-53a3-4be5-a069-7eaf2712b826Or You can check the Application from Enterprise applications.
Create a key Vault
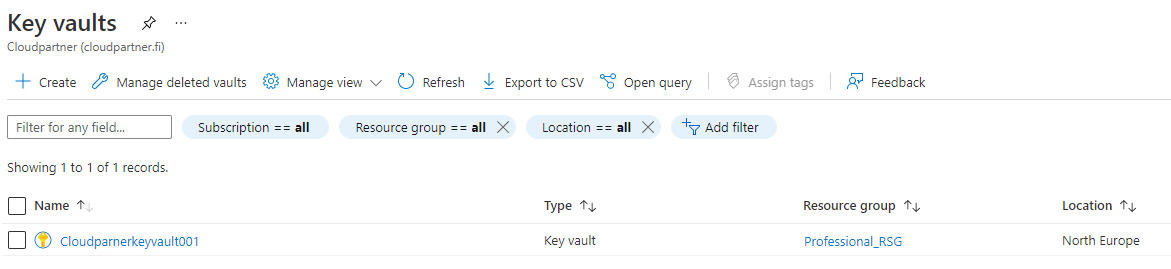
You can create the Key vault with the following command
# Choose a name, Resource group and geographical location New-AzKeyVault -Name Cloudparnerkeyvault001 -ResourceGroupName "Professional_RSG" -Location "North Europe"
And then You can see it inside Your portal.
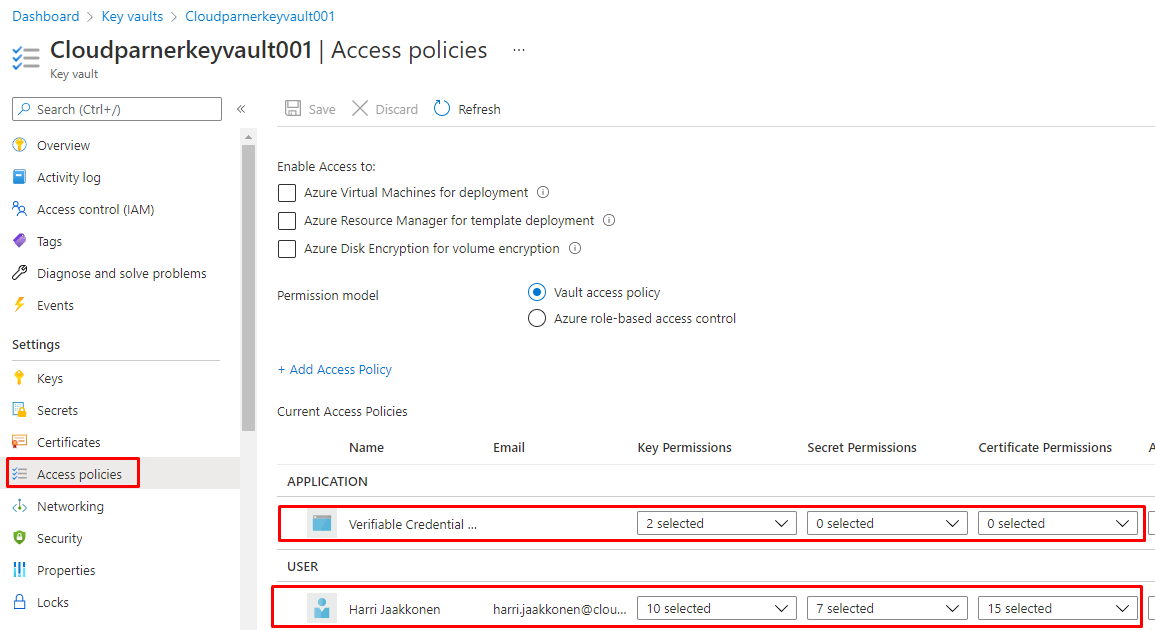
Permissions
You can add the permissions with the following.
# Setting right permissions for Your user to Key vault Set-AzKeyVaultAccessPolicy -VaultName "Cloudparnerkeyvault001" -UserPrincipalName firstname.lastname@domain.fi -PermissionsToKeys get,list,update,create,import,delete,recover,backup,restore,sign # And rights for the Service Principal Set-AzKeyVaultAccessPolicy -VaultName "Cloudparnerkeyvault001" -UserPrincipalName bbb94529-53a3-4be5-a069-7eaf2712b826 -PermissionsToKeys get,sign
Then You can see the permissions inside the Key vault.
App registration
# Add App registration with the following New-AzADApplication -DisplayName Verifiable-credentials-app
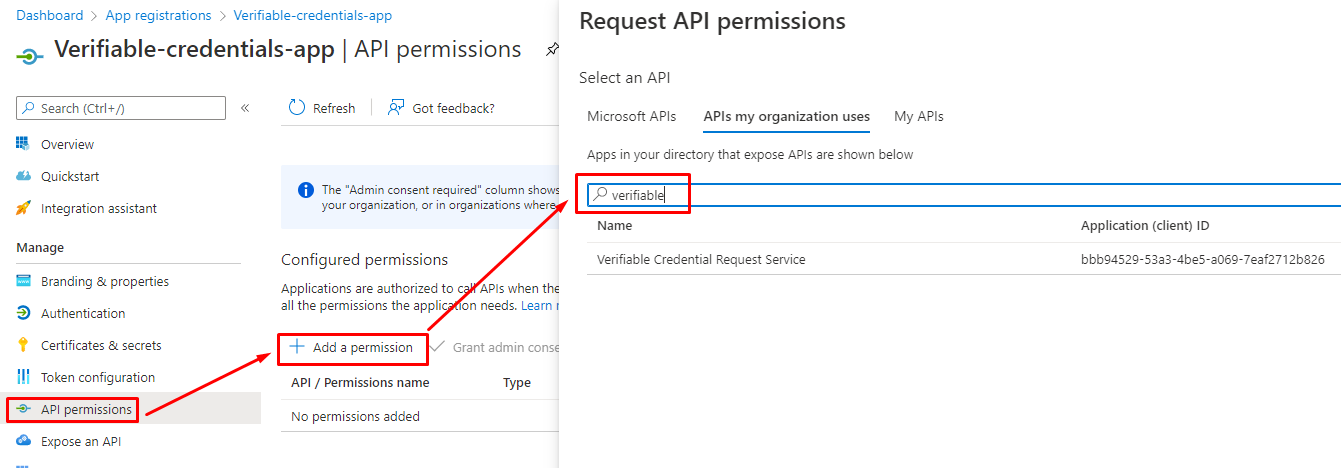
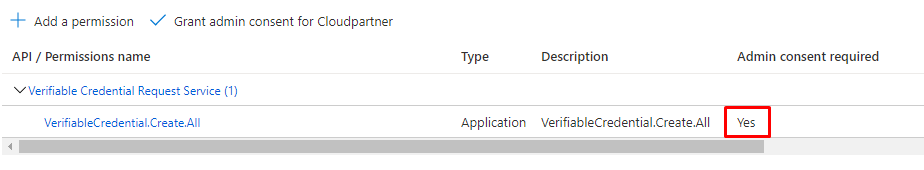
App registration permissions
Add permissions to the App for the API created in the earlier steps.
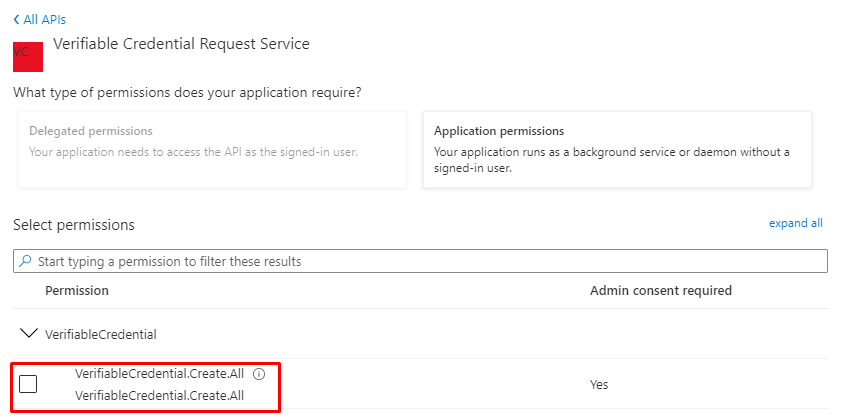
And grant admin consent.
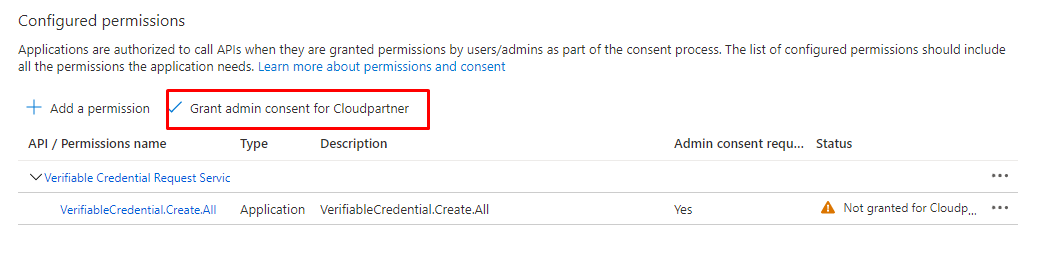
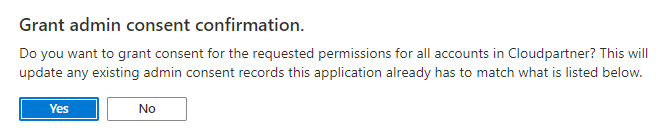
And done.
Set up Verified ID
Prerequisites
- Set up a tenant for Azure AD Verifiable Credentials.
- To clone the repository that hosts the sample app, install GIT.
- Visual Studio Code, or similar code editor.
- .NET 5.0.
- ngrok (free).
- A mobile device with Microsoft Authenticator:
- Android version 6.2108.5654 or later installed.
- iOS version 6.5.82 or later installed.
Create a storage account
You can create a storage account with PowerShell.
# Creating the storage account New-AzStorageAccount -ResourceGroupName professional_rsg -Name cloudpartnervcstorage -Location northeurope -SkuName Standard_LRS # Grant Your user access to Storage account New-AzRoleAssignment -SignInName firstname.lastname@domain.fi -RoleDefinitionName 'Storage Blob Data Reader' -Scope /subscriptions/You Subscription ID/resourceGroups/professional_rsg/providers/Microsoft.Storage/storageAccounts/cloudpartnervcstorage
Create container under Storage account
# Get storage account keys $StorageAccountKeys = Get-AzStorageAccountKey -ResourceGroupName professional_rsg -Name cloudpartnervcstorage # Select first key and expand value $Key0 = $StorageAccountKeys | Select-Object -First 1 -ExpandProperty Value # Put key1 value to $Context variable # Create new container with context New-AzstorageContainer -Context $Context -Name cloudpartnervccontainer
Remove public access from Storage Account
# Removing the public access from the Storage account Set-AzStorageAccount -ResourceGroupName professional_rsg -Name cloudpartnervcstorage -PublicNetworkAccess Disabled
The GUI way

Tutorial - Configure your tenant for Microsoft Entra Verified ID (preview) - Microsoft Entra
And rest of the setup
Create configuration files
Azure AD Verifiable Credentials uses two JSON configuration files, the rules file and the display file.
- The rules file describes important properties of verifiable credentials. In particular, it describes the claims that subjects (users) need to provide before a verifiable credential is issued for them.
- The display file controls the branding of the credential and styling of the claims.
Create two files, first one VerifiedCredentialExpertDisplay.json
{ "default": { "locale": "en-US", "card": { "title": "Verified Credential Expert", "issuedBy": "Microsoft", "backgroundColor": "#2E4053", "textColor": "#ffffff", "logo": { "uri": "https://didcustomerplayground.blob.core.windows.net/public/VerifiedCredentialExpert_icon.png", "description": "Verified Credential Expert Logo" }, "description": "Use your verified credential to prove to anyone that you know all about verifiable credentials." }, "consent": { "title": "Do you want to get your Verified Credential?", "instructions": "Sign in with your account to get your card." }, "claims": { "vc.credentialSubject.firstName": { "type": "String", "label": "First name" }, "vc.credentialSubject.lastName": { "type": "String", "label": "Last name" } } } }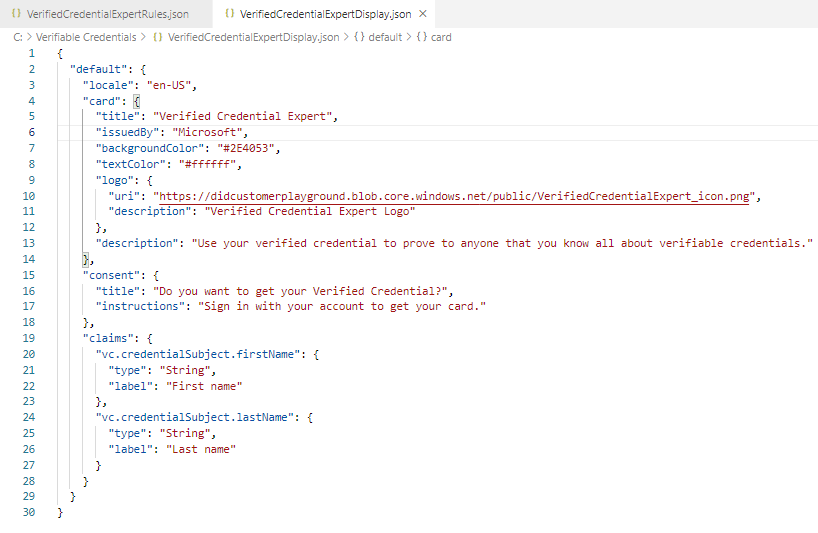
And the second one VerifiedCredentialExpertRules.json
{ "attestations": { "idTokens": }, "validityInterval": 2592001, "vc": { "type": } }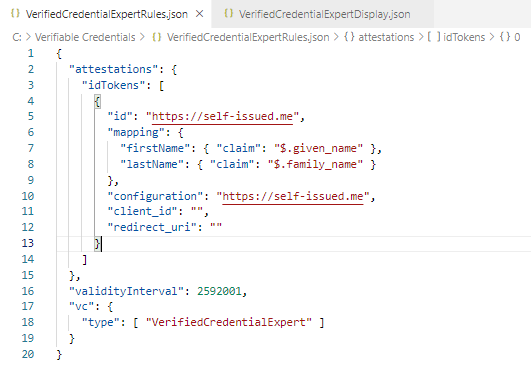
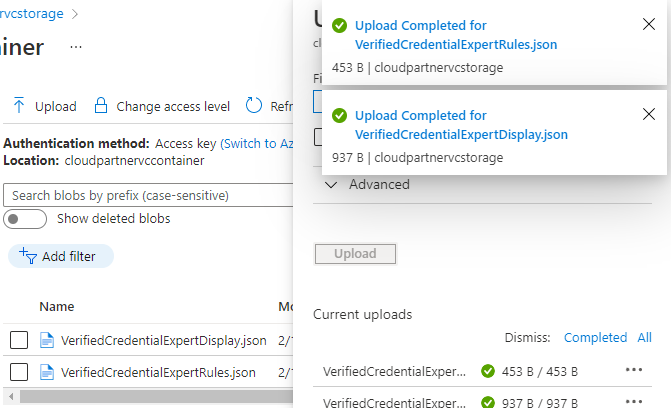
Upload the configuration files
Open the container You created earlier and upload the json files
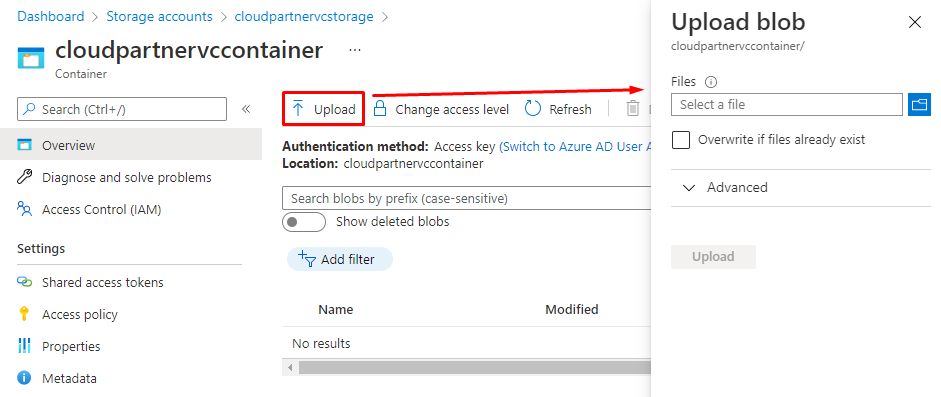
And done.
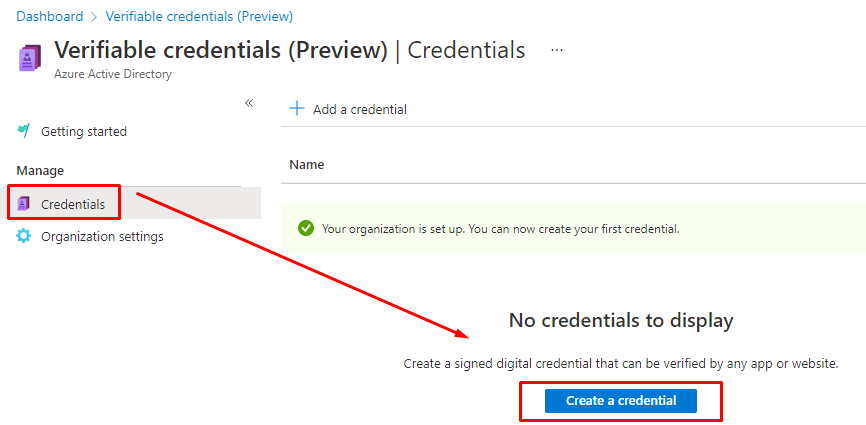
Creating Verified ID's
Search for Verifiable and open Credentials, then Create.
Select the files that we just uploaded.
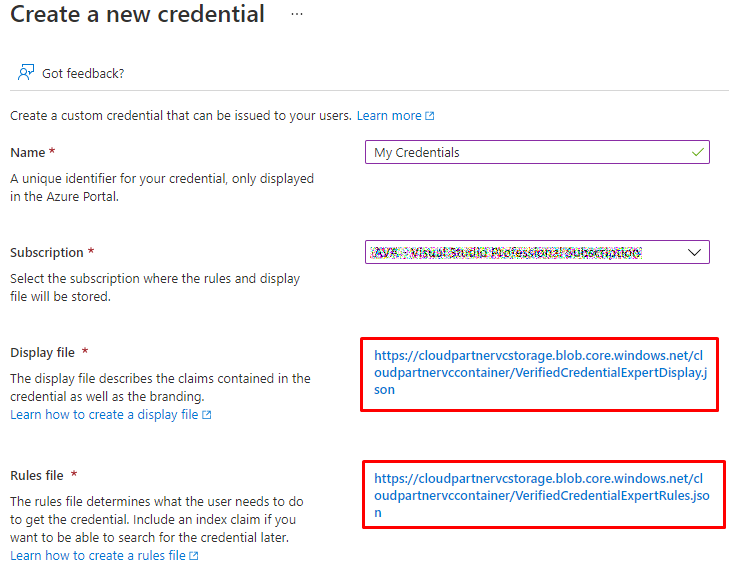
And done.
Final thoughts
With Verifiable credentials you will be able to provide other proof of Your identity like passport, driving license, work agreement or even a school diploma.
Verified ID gives a new options to verify your self with other means than only your username, happy days!
