Microsoft Compliance rebranded as Microsoft Purview
What?
Microsoft rebranded Microsoft 365 compliance to Microsoft Purview and the solutions within the compliance area.
Azure Purview is now Microsoft Purview, which makes a lot of sense as they all belong under Compliance offering.
How to access?
Open the new portal from here

Microsoft Purview compliance portal
What is inside?
- Communication Compliance
- Foster a safe and compliant workplace by detecting sensitive or inappropriate content shared across your organization’s communication channels. Learn more
- Compliance Manager
- Reduce risk by translating complex regulatory requirements into specific improvement actions that help you raise your score and track progress. Learn more
- Data Lifecycle Management
- Classify and govern data at scale to meet your legal, business, privacy, and regulatory content obligations. Learn more
- Data Loss Prevention
- Automatically protect sensitive information from risky and unauthorized access across apps, services, endpoints, and on-premises files. Learn more
- Data Map and Data Catalog
- Maximize the business value of data for your consumers by creating a unified map to automate and manage metadata from hybrid sources. Make data easily discoverable and understand the origin of your data with interactive data lineage visualization. Learn more
- eDiscovery
- Discover and manage your data in-place with end-to-end workflows for internal or legal investigations. Learn more
- Information Protection
- Discover, identify, classify, and protect sensitive data that is business critical, then manage and protect it across your environment. Learn more
- Insider Risk Management
- Detect, investigate, and take action on critical risks in your organization, including data theft, data leaks, and security policy violations. Learn more
Renamed products
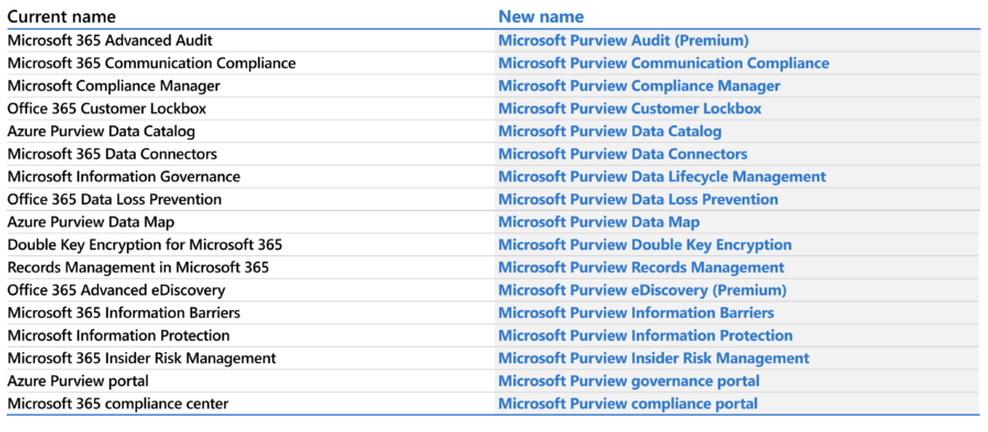
And here is the full list
| Former Name | New Name | Description |
|---|---|---|
| Microsoft 365 Advanced Audit Microsoft 365 Basic Audit | Microsoft Purview Audit (Premium) Microsoft Purview Audit (Standard) | Auditing solutions provide an integrated solution to help organizations effectively respond to security events, forensic investigations, internal investigations, and compliance obligations. To learn more, see Microsoft Purview Advanced Audit (Premium) and Microsoft Purview Advanced Audit (Standard). |
| Microsoft 365 Communication Compliance | Microsoft Purview Communication Compliance | Communication Compliance helps minimize risks by helping you quickly detect, capture, and take remediation actions for company communication channels and policy violations. To learn more, see Microsoft Purview Communication Compliance. |
| Microsoft Compliance Manager | Microsoft Purview Compliance Manager | Compliance Manager can help you throughout your compliance journey, from taking inventory of your data protection risks to managing the complexities of implementing controls, staying current with regulations and certifications, and reporting to auditors. To learn more, see Microsoft Purview Compliance Manager. |
| Microsoft 365 Customer Key | Microsoft Purview Customer Key | Customer Key provides extra protection against viewing of data by unauthorized systems or personnel, and complements BitLocker disk encryption in Microsoft data centers. To learn more, see Microsoft Purview Customer Key. |
| Office 365 Customer Lockbox | Microsoft Purview Customer Lockbox | Customer Lockbox ensures that Microsoft can't access your content to do service operations without your explicit approval. Customer Lockbox brings you into the approval workflow process that Microsoft uses to ensure only authorized requests allow access to your content. To learn more, see Microsoft Purview Customer Lockbox. |
| Data Loss Prevention | Microsoft Purview Data Loss Prevention | DLP helps protect sensitive data and reduce risk by preventing users from inappropriately sharing that data with people who shouldn't have it. To learn more, see Microsoft Purview Data Loss Prevention. |
| Double Key Encryption for Microsoft 365 | Microsoft Purview Double Key Encryption | Double Key Encryption (DKE) uses two keys together to access protected content. Microsoft stores one key in Microsoft Azure, and you hold the other key. To learn more, see Microsoft Purview Double Key Encryption |
| Microsoft 365 Information Barriers | Microsoft Purview Information Barriers | Information Barriers is a solution which restricts communication and collaboration between certain people inside your organization to safeguard internal information. To learn more, see Microsoft Purview Information Barriers. |
| Microsoft Information Protection | Microsoft Purview Information Protection | Information protection helps you discover, classify, and protect sensitive information wherever it lives or travels. To learn more, see Microsoft Purview Information Protection. |
| Microsoft Information Governance | Microsoft Purview Data Lifecycle Management | Data lifecycle management provides you with tools and capabilities to retain the content that you need to keep and delete the content that you don't. To learn more, see Microsoft Purview Data Lifecycle Management. |
| Microsoft 365 Insider Risk Management | Microsoft Purview Insider Risk Management | Insider risk management uses the full breadth of service and 3rd-party indicators to help you quickly identify, triage, and act on risky user activity. To learn more, see Microsoft Purview Insider Risk Management. |
| Office 365 Message Encryption | Microsoft Purview Message Encryption | With Message Encryption, your organization can send and receive encrypted email messages between people inside and outside your organization. To learn more, see Microsoft Purview Message Encryption. |
| Privileged Access Management in Microsoft 365 | Microsoft Purview Privileged Access Management | Privileged Access Management helps protect your organization from breaches and helps to meet compliance best practices by limiting standing access to sensitive data or access to critical configuration settings. To learn more, see Microsoft Purview Privileged Access Management. |
| Microsoft data connectors | Microsoft Purview data connectors | Microsoft 365 lets administrators use data connectors to import and archive non-Microsoft, third-party data from social media platforms, instant messaging platforms, and document collaboration platforms, to mailboxes in your Microsoft 365 organization. To learn more, see Microsoft Purview data connectors. |
| Microsoft 365 Advanced eDiscovery Microsoft 365 Core eDiscovery | Microsoft Purview eDiscovery (Premium) Microsoft Purview eDiscovery (Standard) | Electronic discovery, or eDiscovery, is the process of identifying and delivering electronic information that can be used as evidence in legal cases. To learn more, see Microsoft Purview eDiscovery (Premium) and Microsoft Purview eDiscovery (Standard). |
| Microsoft 365 compliance center | Microsoft Purview compliance portal | Admin portal to access solutions and solution catalog within the Microsoft 365 E5 Compliance suite. To learn more, see Microsoft Purview compliance portal. |
Extra content for compliance
For DLP
(D)ata (L)oss (P)revention, content escapes your hands
Have no fear coz DLP is here and it won’t let your data to escape, at least if you made right configuration. It isn’t an automatic feature that you enable and forget. There a lot of different aspect you have to consider with DLP policies. What to protect? You can protect what you want, it

Announcing general availability of Microsoft Purview Data Loss Prevention for macOS endpoints
As workplaces transition from remote to hybrid, workers are moving fluidly between work and home devices and networks. This shift poses new set of challenges, and organizations are concerned about worker’s inadvertent mistakes and unsafe data practices leading to more data breaches and exfiltration.…
For AIP
(A)zure (I)nformation (P)rotection why and how?
Your organization has different kind of files. User personal files, patent pending studies, agreements, receipt, applications, copies of super duper secret documents scattered all over and you don’t even where. These a risk of leaking those documents externally either by mistake or knowingly doing so. You send internally something that you wan’t to be printed,
AIP Scanner and how to dig your content
What Is AIP scanner? Azure Information Protection Scanner is combination of Azure Information Protection Viewer, SQL DB and Azure App registration. It will discover the data from File shares, SharePoint content and it also has a network discovery functionality (that I will not be covering in this post) Installation prerequisites https://docs.microsoft.com/en-us/azure/information-protection/deploy-aip-scanner-prereqs Read them thru, not
Retention
Retention policies why and how?
The picture above is from one of the many CISSP videos that I have watched but it came to good point as I was planning to write a posts about data retention and why it matters. So why it matters? In Europe we have GDPR regulations and they state that every individual can ask organizations
Compliance manager
Why to use Compliance Manager for assessments and attack simulator to educate users.
Today I will be talking about Compliance Manager and in next part about Attack Simulator and why they matter for your organization. Compliance is based on organization industry or customer requirements. Compliance improves your security posture. It will help you define baseline for security requirements, but also minimize costs during possible breaches and lost of
Insider risks
Insider risk management, what, why and how
What is Insider risk management Insider risk management is a solutions for example to prevent leavers to take precious company data with them when to go. But there is also options to lower the risk for users, example anonymizing usernames. Compliance analysts and investigators can easily use Microsoft Teams for collaboration on insider risk management
Insider risk management continued, device onboarding and protection
Now to part two of this series and onboarding devices to Compliance center. Continuing device onboarding. Go to device onboarding. You have these options to onboard. I will be choosing local scripts but the fundamentals will be the same no matter what onboarding option you choose. Download the script, extract and run. It will check
Adaptive scopes
Information governance and adaptive scopes
Adaptive scopes in now in preview and will be soon released to general availability. With adaptive scopes you can define a attribute based filtering for content. Really nice addition to filtering locations easily. How to create Adaptive scopes? Go to Information governance and choose Adaptive scopes then create scope Choose what kind of scope you
Information barriers
Information barriers, the GUI experience (Public preview)
This pic above is exactly the opposite of how information barriers work. So how it works? When information barrier policies are in place, people who should not communicate or share files with other specific users won’t be able to find, select, chat, or call those users. With information barriers, checks are in place to prevent
Final words
Microsoft has really invested in the Compliance offering landscape, which is excellent as the data is undiscovered and unprotected until you handle the content somehow.
For this need Microsoft has an excellent pack of solutions which keep getting better many times in a year.
From here you can see the list of What's new for Compliance.

What’s new in Microsoft Purview - Microsoft Purview
Whether it be adding new solutions to the compliance center, updating existing features based on your feedback, or rolling out fresh and updated documentation, Microsoft 365 helps you stay on top of the ever-changing compliance landscape. Find out what we’ve been up to this month.
Keep doing what you do Microsoft! There is a lot of environments to make compliant!
