Insider risk management continued, device onboarding and protection
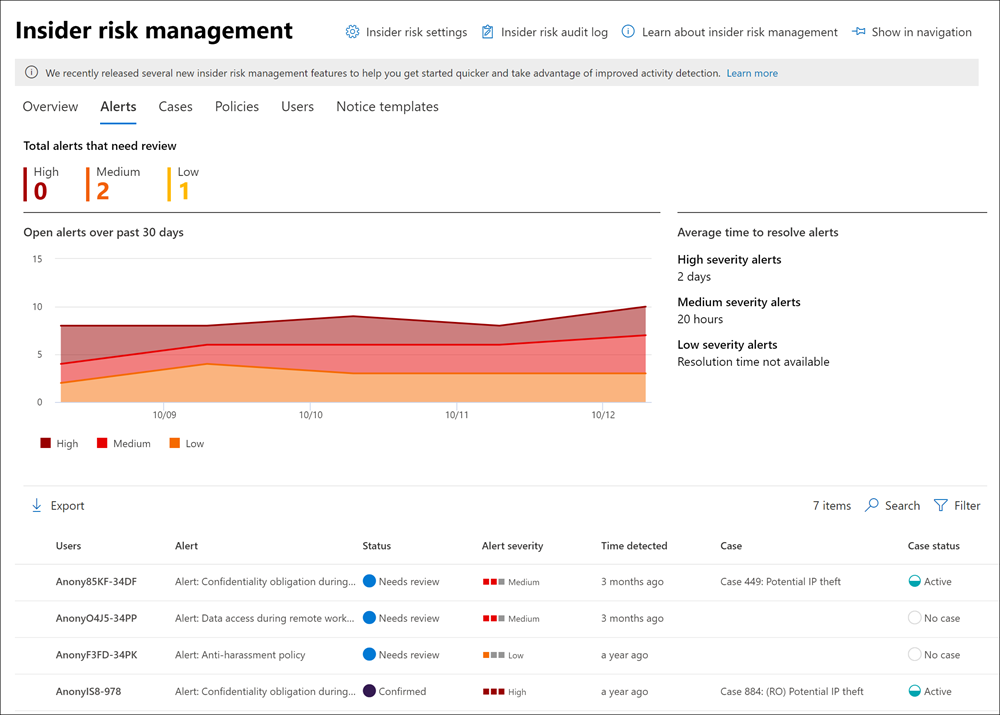
Now to part two of this series and onboarding devices to Compliance center.
Continuing device onboarding.
Go to device onboarding.
You have these options to onboard.
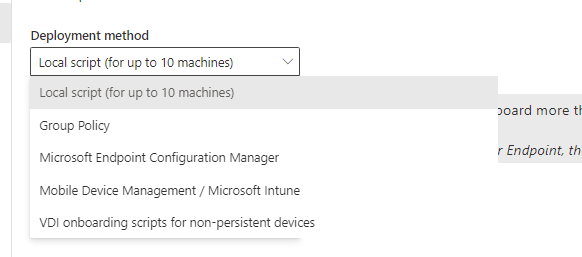
I will be choosing local scripts but the fundamentals will be the same no matter what onboarding option you choose.
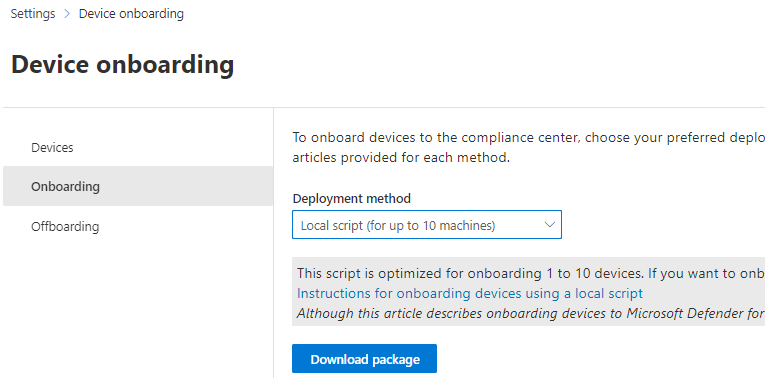
Download the script, extract and run.
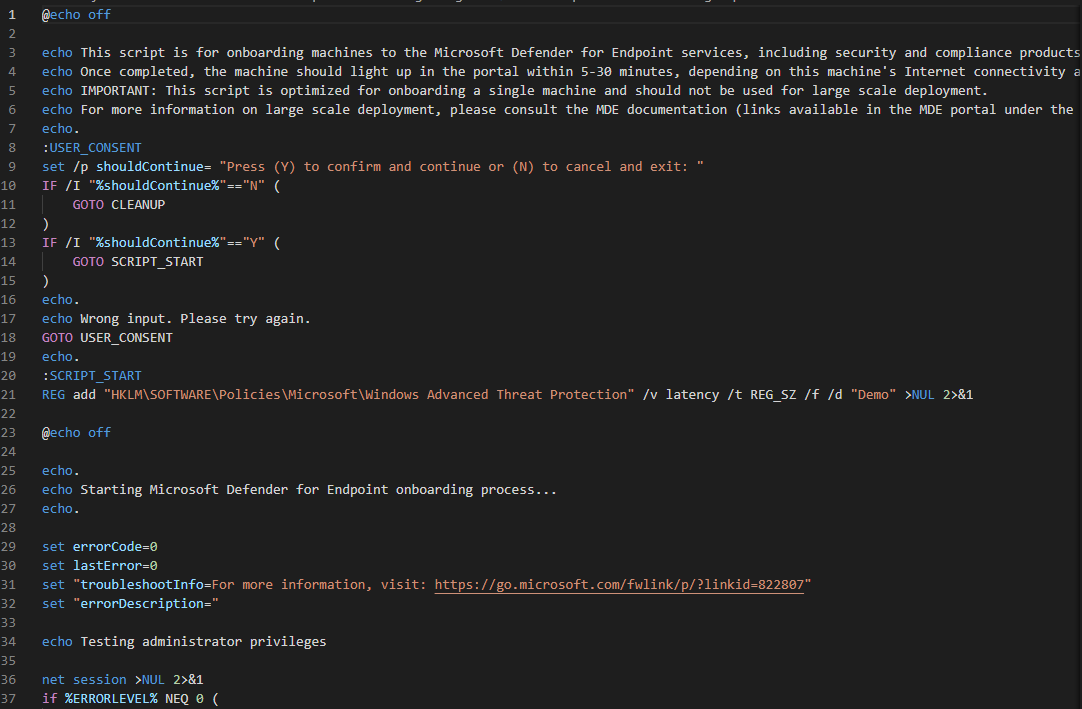
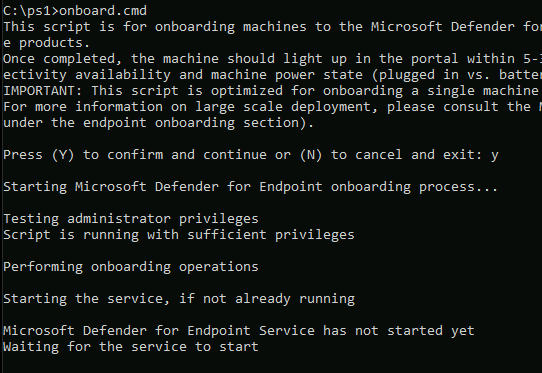
It will check your rights and start the service.
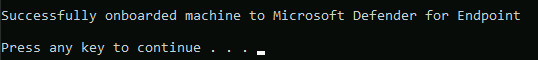
And done.
It will take 5-30 minutes so be populated to the portal.
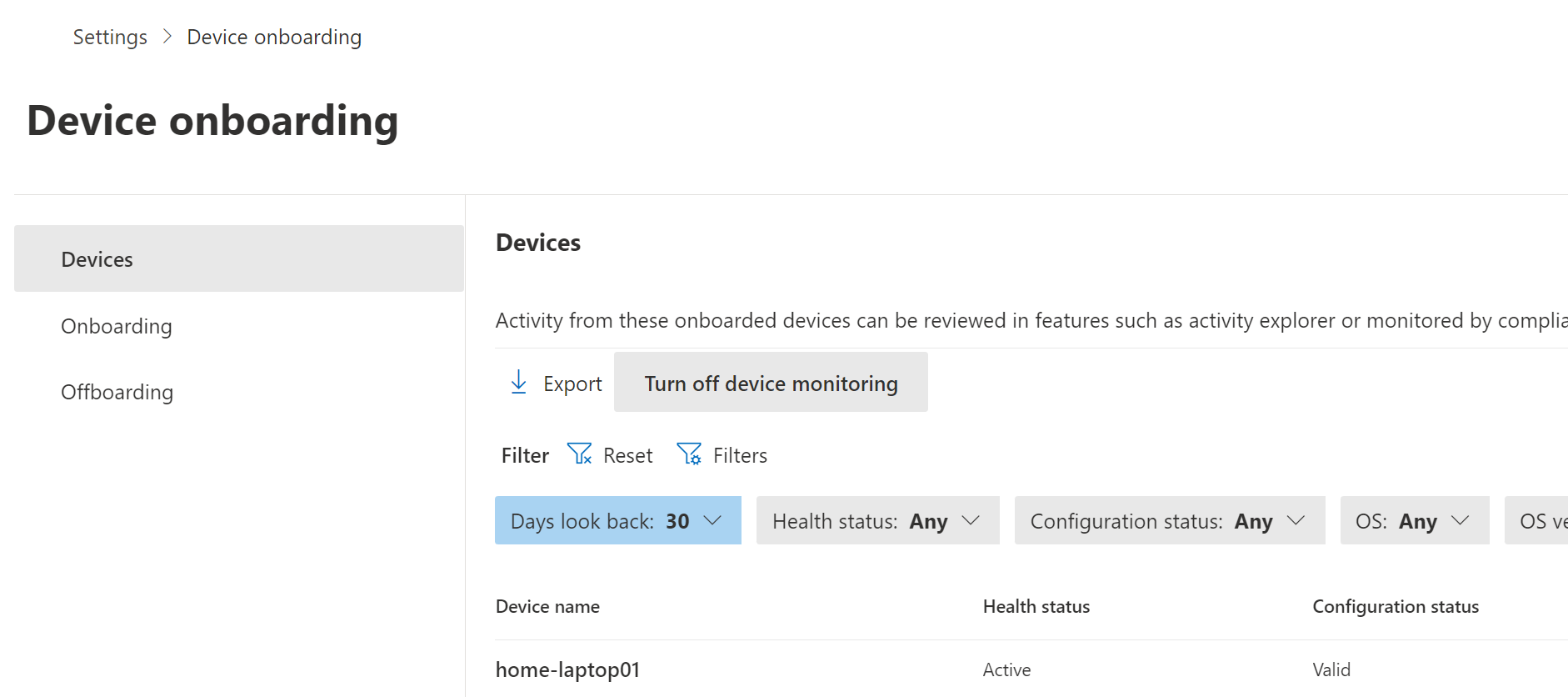
Adding device to Insider risk management
Once you have the device onboarded you can add device indicators for it.
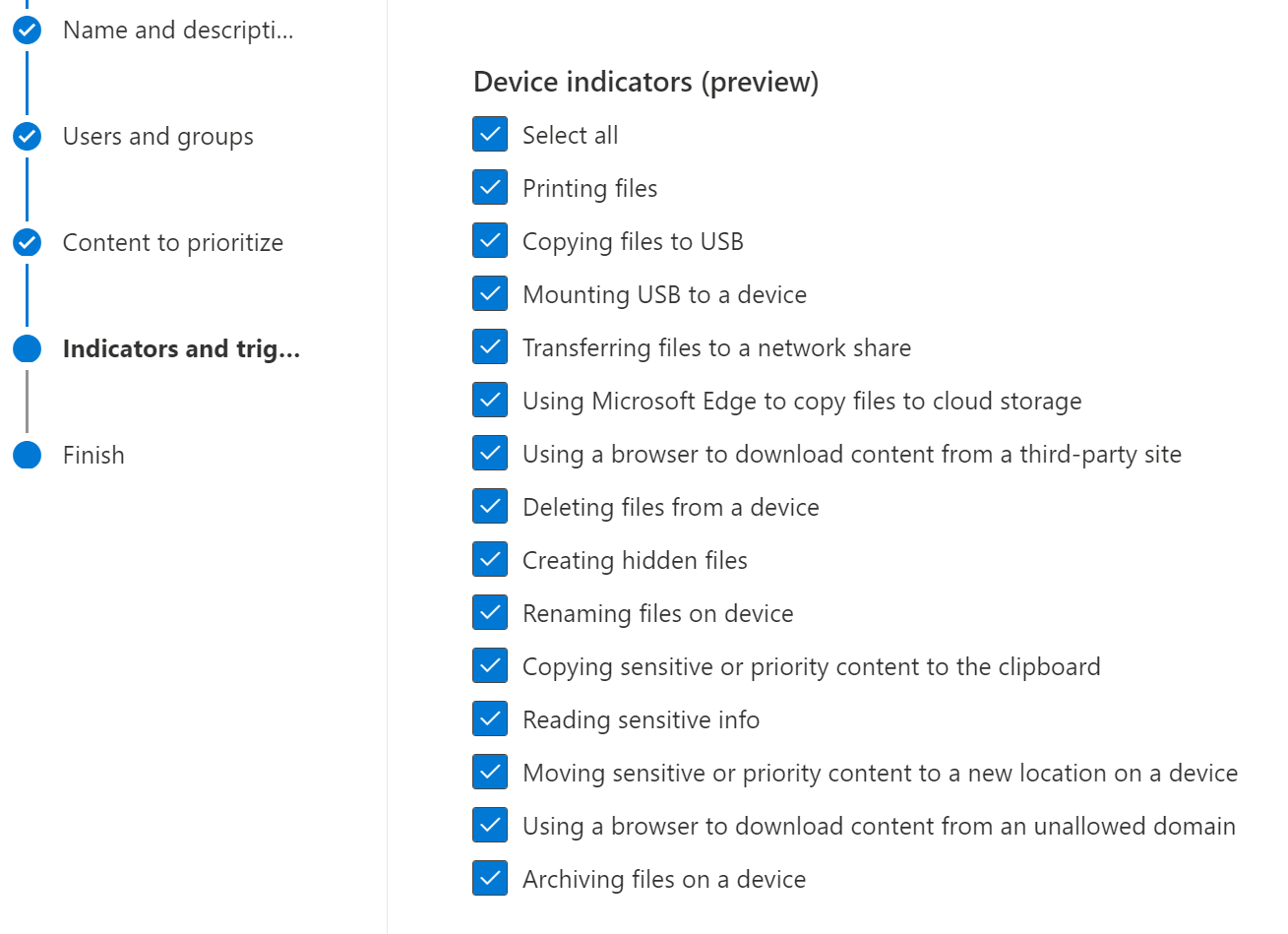
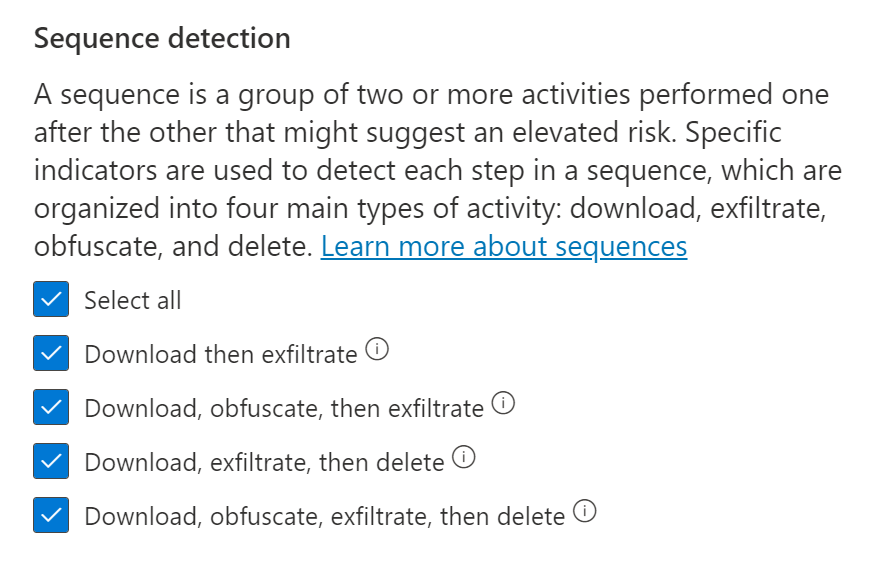
And you can choose the detections for the sequence.
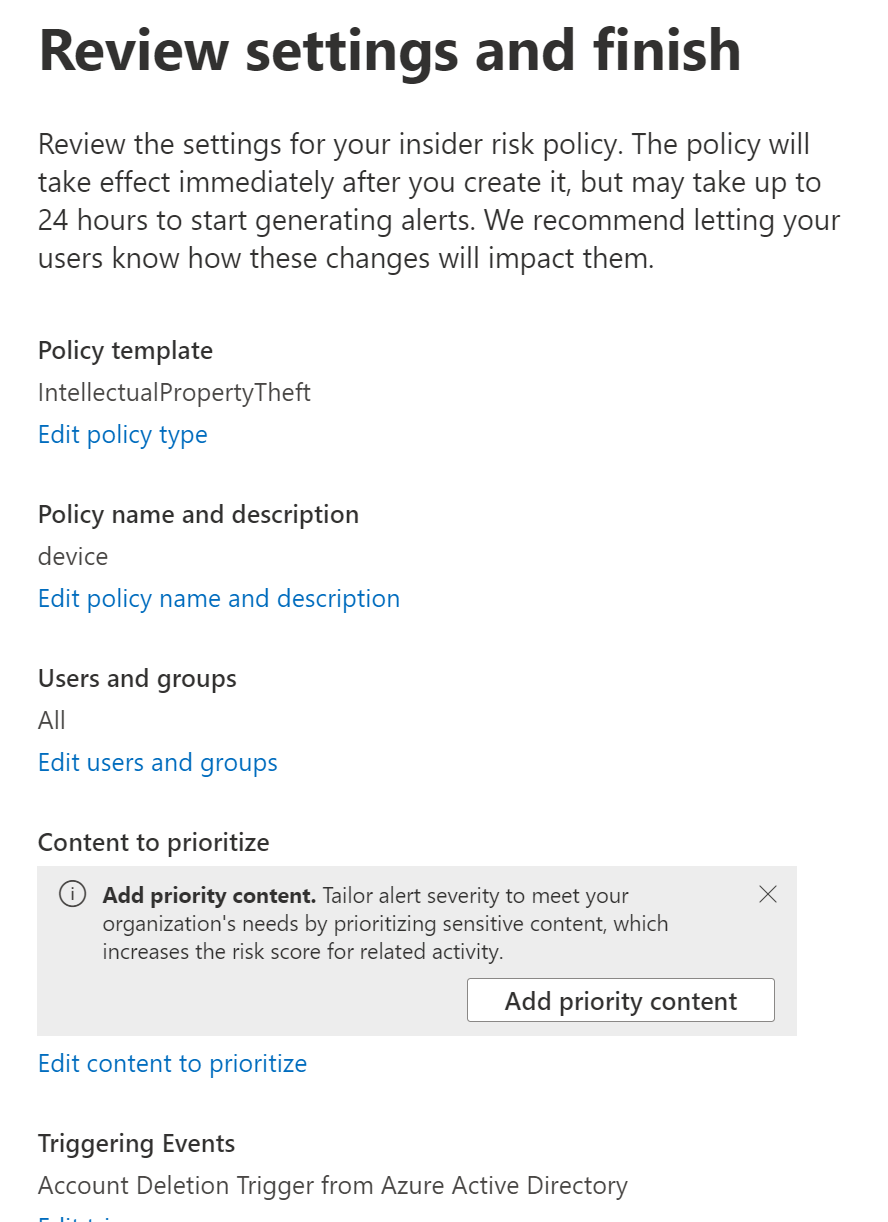
And you can finish policy creation.
Endpoint DLP
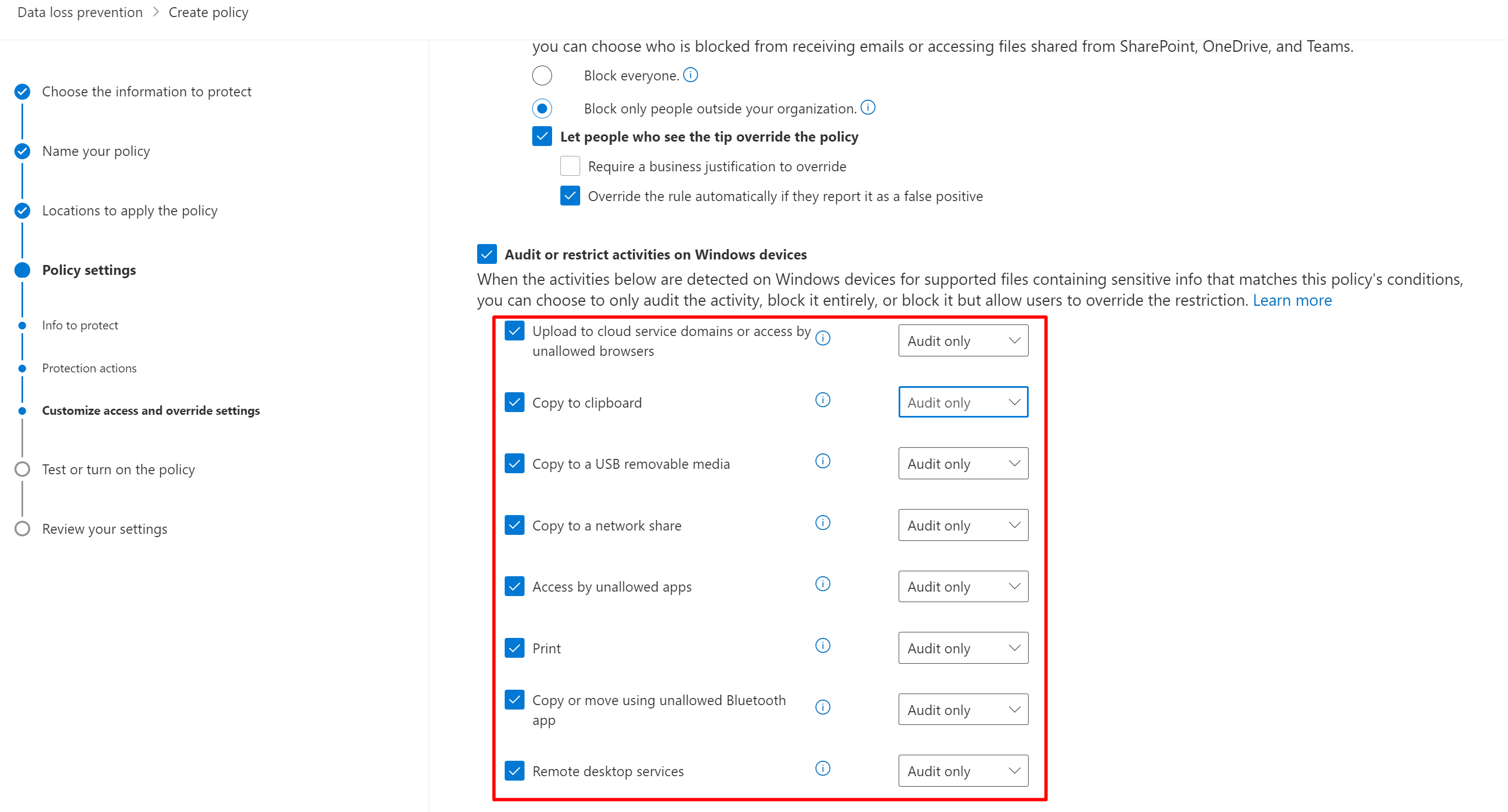
Then you can enable Endpoint DLP to protect your content inside your devices.
Go to create a new policy and choose devices.
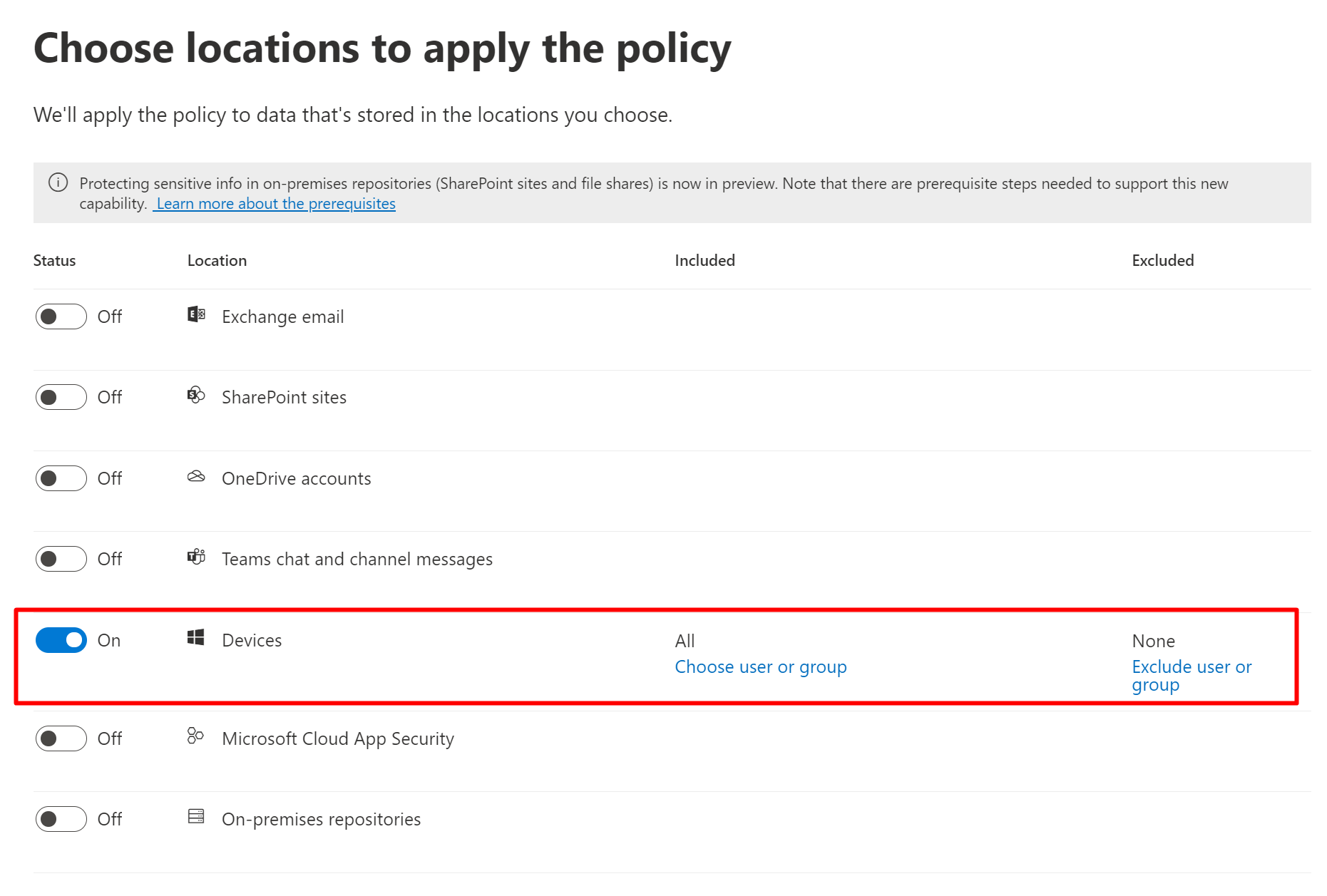
And then you can choose Audit, Block or and Block with Override
Supported file types
Endpoint DLP supports monitoring of these file types. DLP audits the activities for these file types, even if there isn't a policy match.
- Word files
- PowerPoint files
- Excel files
- PDF files
- .csv files
- .tsv files
- .txt files
- .rtf files
- .c files
- .class files
- .cpp files
- .cs files
- .h files
- .java files
Quick tip! To ensure activities are audited for all supported file types, create a custom DLP policy.
Here's link to part one of this series.
Insider risk management, what, why and how
