From B2C to EEID: What You Need to Know?
Microsoft is evolving its customer identity and access management (CIAM) solutions with the introduction of Microsoft Entra External ID. This new platform aims to unify and modernize the management of external identities, including customers, partners, and citizens, within a single, integrated system.
Understanding the Transition: Azure AD B2C and Azure AD External Identities
Microsoft Entra External ID is not merely a rebranding of Azure AD B2C; it represents a next-generation CIAM solution that combines customer identity and access management with B2B collaboration features into one unified platform. While Azure AD B2C and Azure AD External Identities have served distinct purposes in managing external identities, Entra External ID consolidates these functionalities to provide a more streamlined and secure experience.
Key Features of Microsoft Entra External ID
Entra External ID offers several enhancements over its predecessors:
- Unified Platform: Combines CIAM and B2B collaboration features, allowing organizations to manage all external identities within a single system.
- Modern Authentication Protocols: Supports OpenID Connect (OIDC) for federated authentication, enabling seamless integration with various identity providers.
- Enhanced Security and Compliance: Provides advanced security features and compliance capabilities to protect sensitive information and meet regulatory requirements.
- Scalability: Designed to handle large volumes of external users, making it suitable for organizations of all sizes.
Implications for Existing Azure AD B2C Users
For organizations currently using Azure AD B2C, it's important to note that Microsoft will continue to support Azure AD B2C as a separate product offering with no change in SLA. However, the introduction of Entra External ID indicates a strategic shift towards a more integrated and modern approach to managing external identities.
While there is no immediate requirement to migrate from Azure AD B2C to Entra External ID, organizations should consider evaluating the new platform to determine if it better aligns with their long-term identity management strategies.
Quick Start with Microsoft Entra External ID
Getting started with Microsoft Entra External ID is straightforward, thanks to Microsoft's comprehensive quickstart guides. These guides help you set up an external tenant, customize the sign-in experience, and test user sign-up flows.
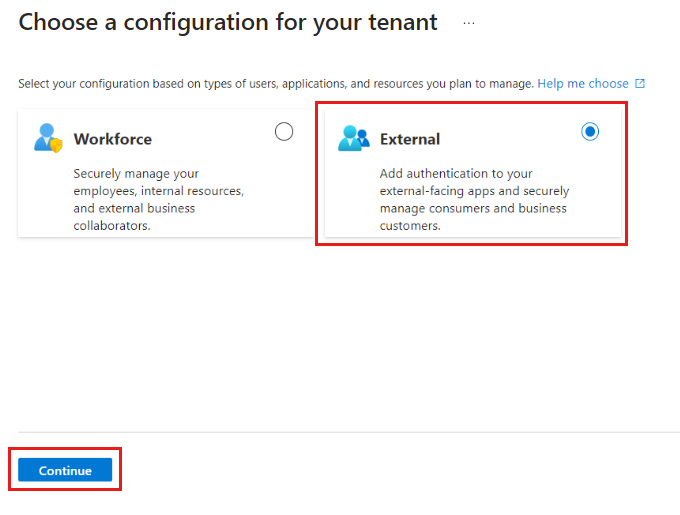
Create an External Tenant
- Sign in to the Microsoft Entra admin center.
- Navigate to Identity > Overview > Manage tenants.
- Select Create, choose External, and follow the prompts to set up your tenant.
Customize the Sign-In Experience
- Access the Get started guide from your tenant's overview page.
- Choose sign-in methods (e.g., email and password or one-time passcode).
- Add branding elements like your company logo and background color.
- Configure external identity providers such as Google, Facebook, Apple, or custom OIDC accounts.
Test the Sign-Up Flow
- Use the guide to run a sample app and simulate user sign-up and sign-in.
- Create a test user and observe the authentication process.
- Review the issued tokens and understand the user journey.
For a more integrated development experience, consider using the Microsoft Entra External ID extension for Visual Studio Code. This extension allows you to create tenants, customize sign-in experiences, and set up sample apps directly within your development environment.
Migrating Users to Microsoft Entra External ID
Migrating users from your existing identity provider to Microsoft Entra External ID involves a structured process to ensure a seamless transition. The official Microsoft guide outlines a two-stage approach.
User Data Migration
Begin by transferring essential user data from your legacy identity provider to Entra External I. This includes usernames, email addresses, phone numbers, and any other relevant attributes. Utilize the Microsoft Graph API to create user accounts in the External ID directory. If you have access to plaintext passwords, you can set them directly during this migration. Otherwise, assign a temporary password that users will update upon their first sign-in.
Recommendations:
- DO: Migrate usernames, passwords, email addresses, phone numbers, and consent markers
- DO NOT: Migrate sensitive data like credit card numbers, social security numbers, medical records, or marketing preferences
Password Migration
If you don't have access to users' plaintext passwords, implement a password migration strategy
- Self-Service Password Reset (SSPR): Encourage users to reset their passwords upon their first sign-in. This can be facilitated through a custom policy or a user-friendly reset portal
- Seamless Migration: For a smoother experience, consider a phased approach where users authenticate using their existing credentials until they are prompted to reset their password. It's important to note that Microsoft Entra External ID does not support direct migration of hashed passwords from legacy systems. Therefore, users will need to reset their passwords as part of the migration process.

Learn how to migrate users to Microsoft Entra External ID - Microsoft Entra External ID
Planning for the Future
As Microsoft continues to develop and enhance Entra External ID, organizations should stay informed about new features and capabilities that may benefit their operations. Evaluating the potential advantages of transitioning to Entra External ID, such as improved security, unified management, and scalability, can help organizations make informed decisions about their identity management solutions.
| Date | Information |
|---|---|
| May 1, 2025 | Microsoft will discontinue the sale of Azure AD External Identities Premium P1 and P2 licenses to new customers. Which was primarily used with Azure AD B2C |
| May 1, 2025 | Existing Azure AD B2C customers can continue using the product without disruption. |
| May 1, 2025+ | User experience, including creating new tenants or user flows for existing customers, will remain unchanged. |
| May 1, 2025+ | Operational commitments (SLAs, security updates, compliance) for existing customers will remain unaffected. |
| At least May 2030 | Microsoft has committed to supporting Azure AD B2C until at least this date. |
For more detailed information and guidance on Microsoft Entra External ID, refer to the official Microsoft documentation: Microsoft Entra External ID Frequently Asked Questions.
