Defender for Cloud security alerts

The scenario
You have a Windows server with a public IP-address and RDP (TCP 3389) is exposed to internet.
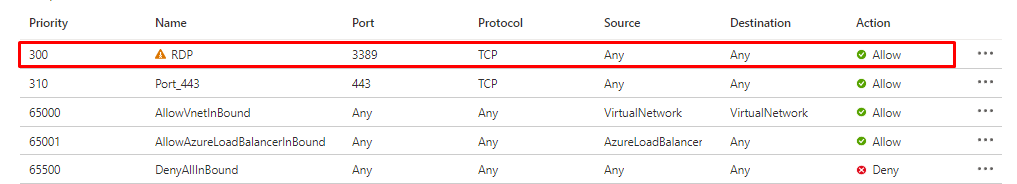
And there is still over 3 million open TCP 3389 ports out there.
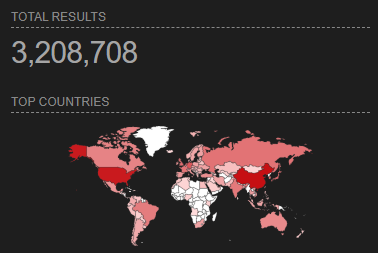
Stupid right but if you are one of them this is what it will eventually look inside Defender for Cloud.
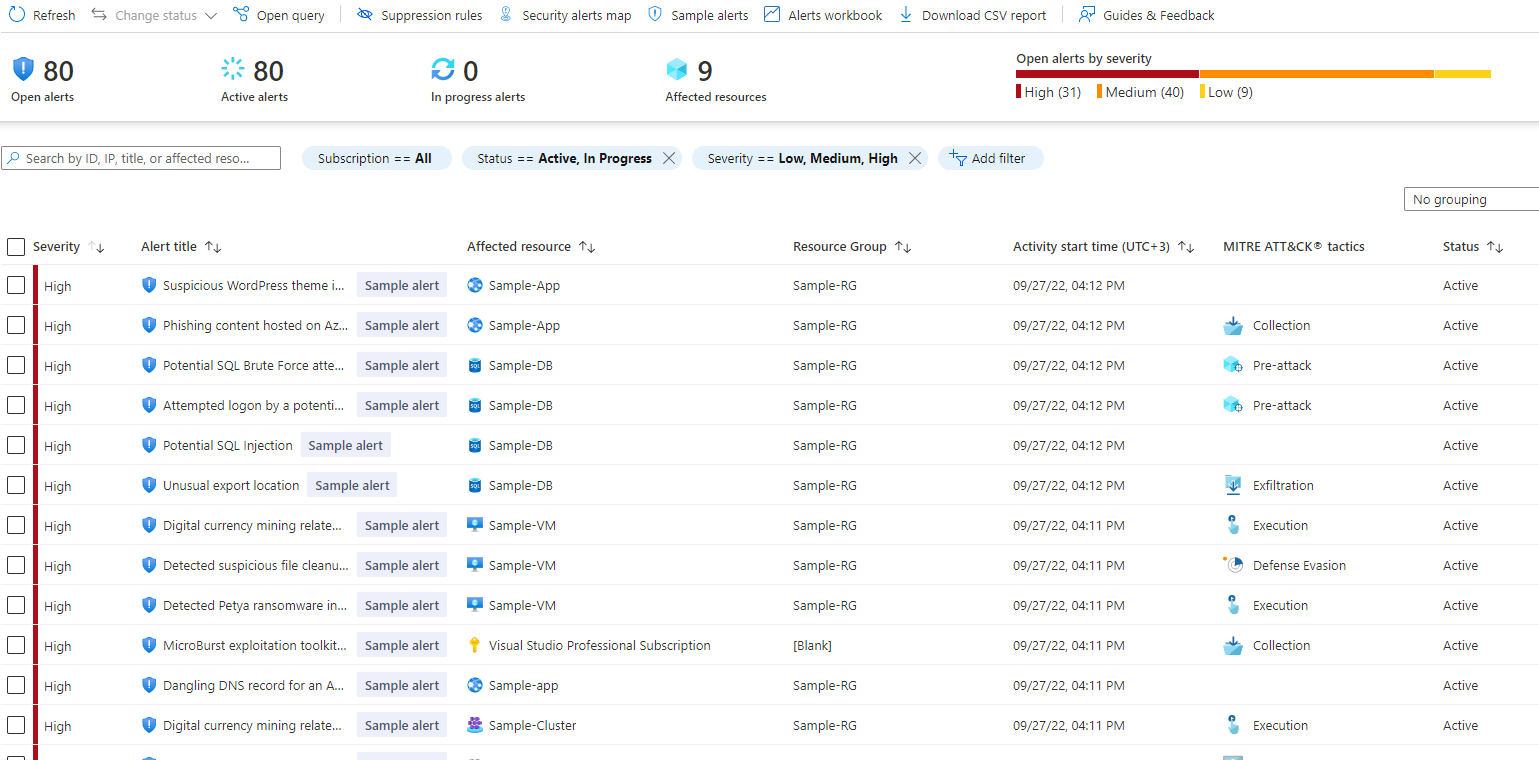
Main page
You will see the alerts under security alerts
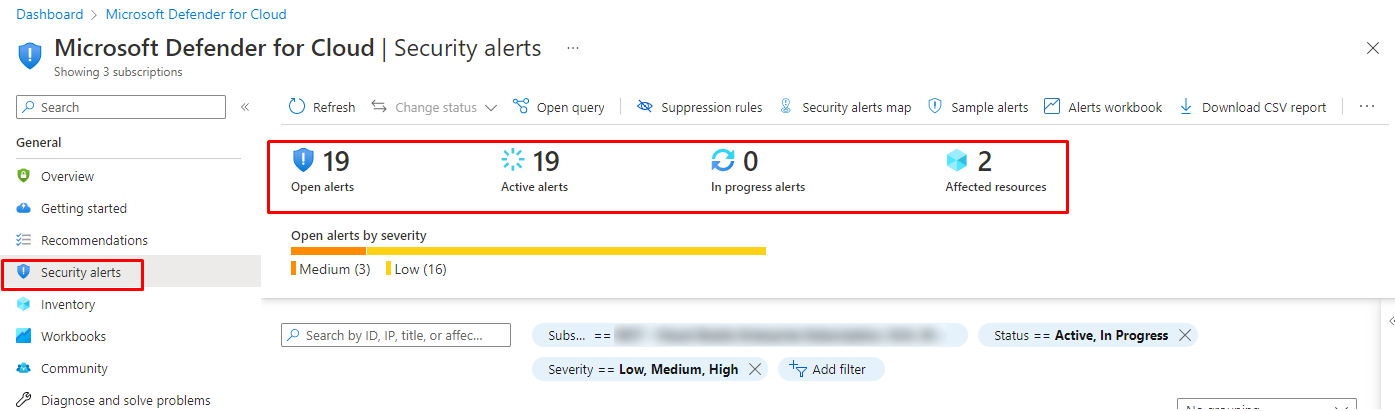
And below you have list of the affected resources with the severity Microsoft has chosen based on MITRE ATT&CK framework.
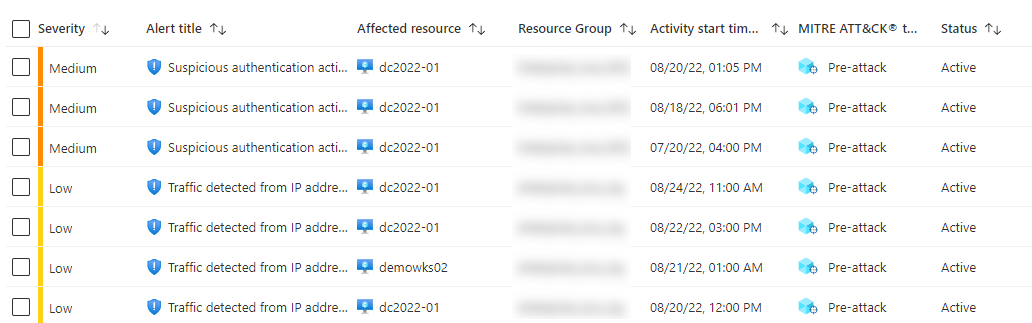
MITRE ATT&CK tactics
Defender for cloud

Reference table for all security alerts in Microsoft Defender for Cloud
| Tactic | ATT&CK Version | Description |
|---|---|---|
| PreAttack | PreAttack could be either an attempt to access a certain resource regardless of a malicious intent, or a failed attempt to gain access to a target system to gather information prior to exploitation. This step is usually detected as an attempt, originating from outside the network, to scan the target system and identify an entry point. |
Microsoft Sentinel | MITRE ATT&CK (Preview)
And you can see the framework also from Sentinel, excellent all-in-one shop.
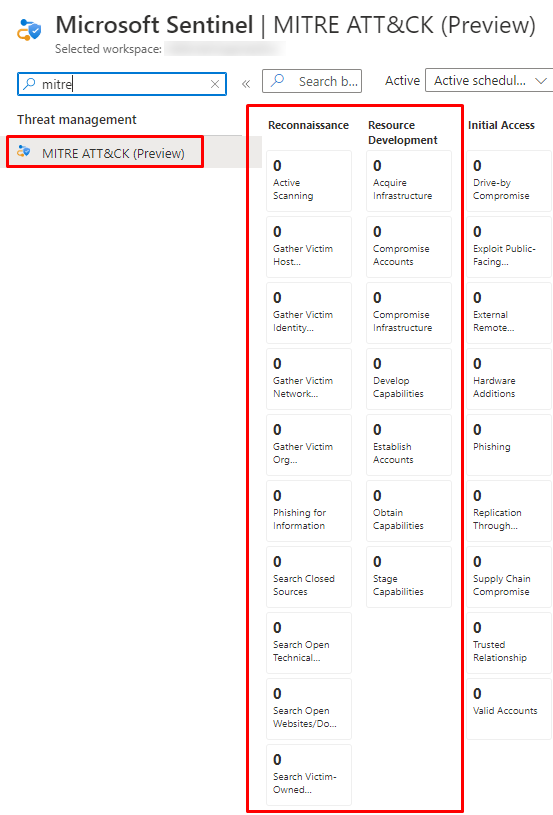
MITRE ATT&CK for preparatory techniques

Matrix - Enterprise | MITRE ATT&CK®
And the full framework for you to search.

MITRE ATT&CK®
Continuing the Pre-Attack recon
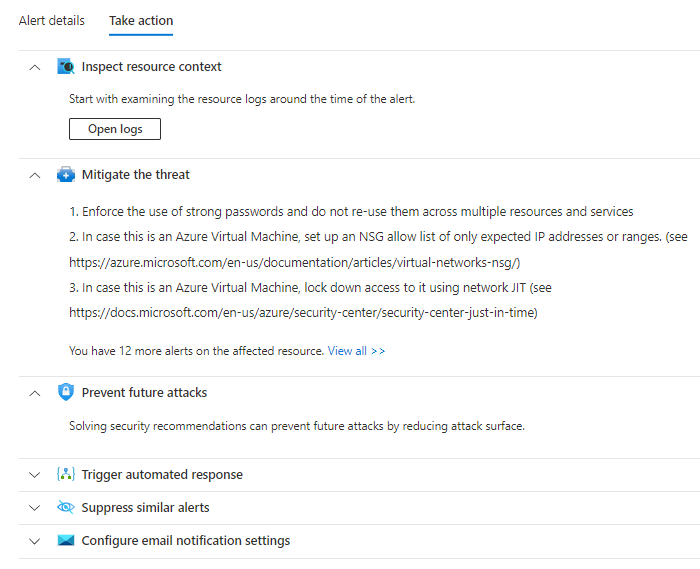
Under alert you can view full details or take actions
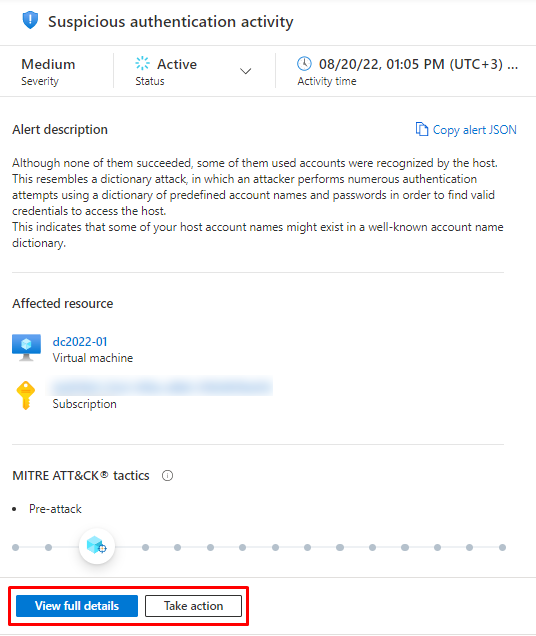
Under full details you will see what is happening with your little box. It seems to be a brute force attack, trying out the user accounts that could be active, scary.
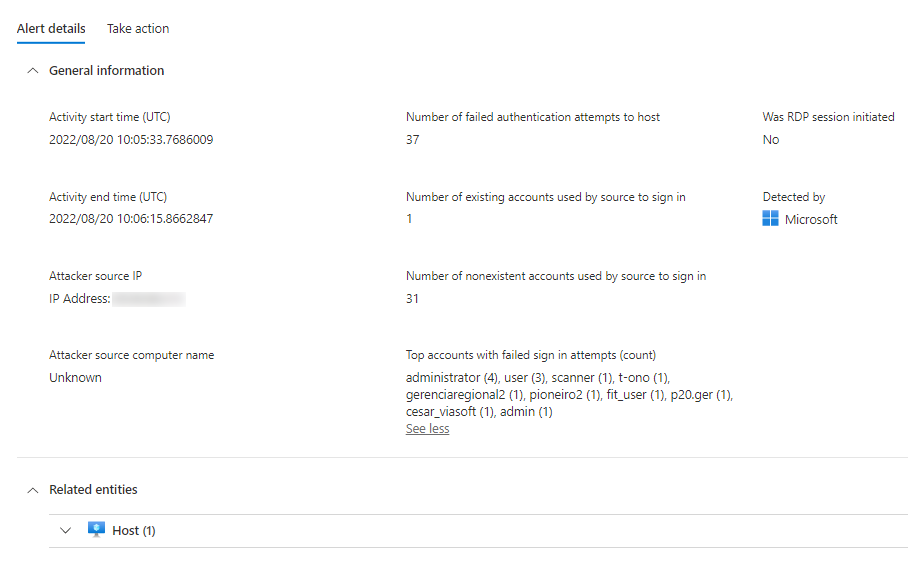
And some probing for RDP ports.
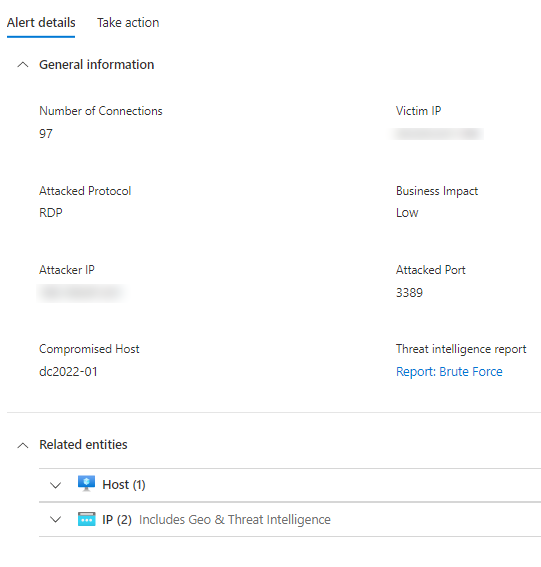
On take action page you can see the obvious actions, block RDP, use JIT and enable MFA. Which are the first ones to take.
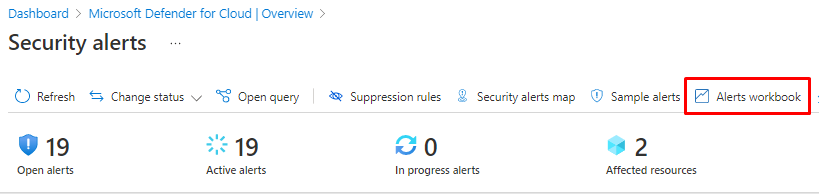
You can more data under alerts workbook.
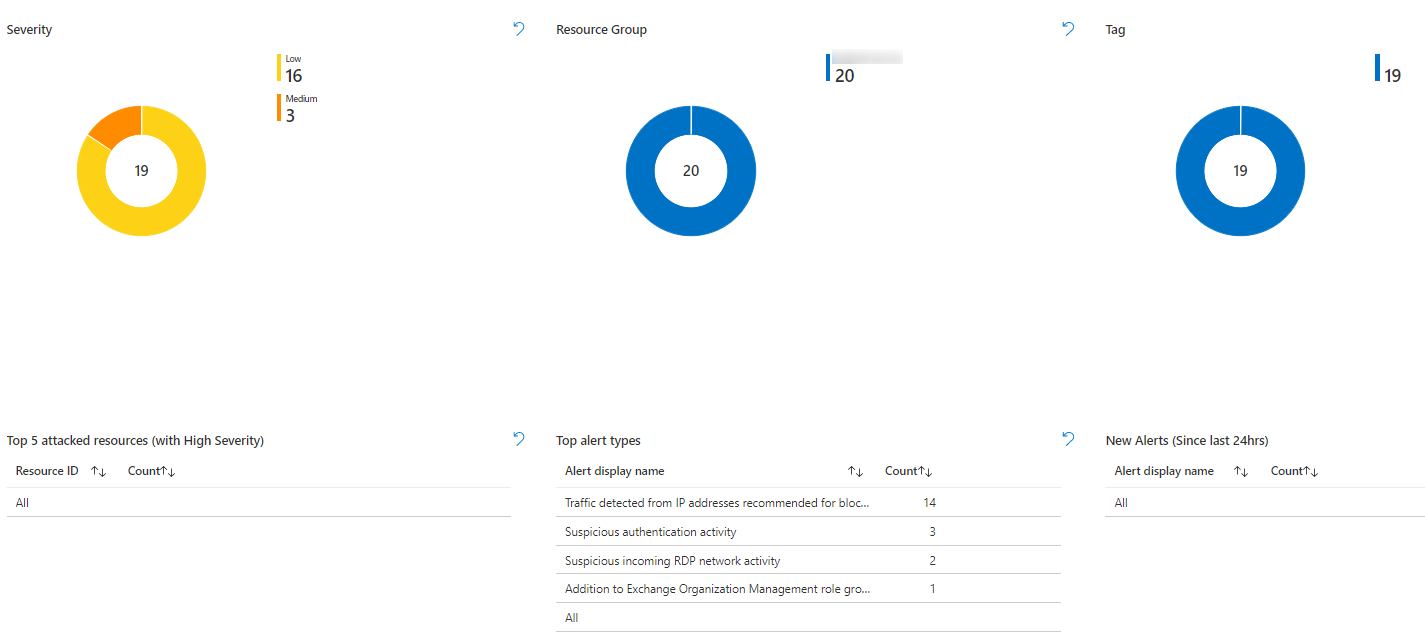
You will see more details in the attack.
Generating alerts
If you don't have and want to try the feature out, you can generate your own alerts with
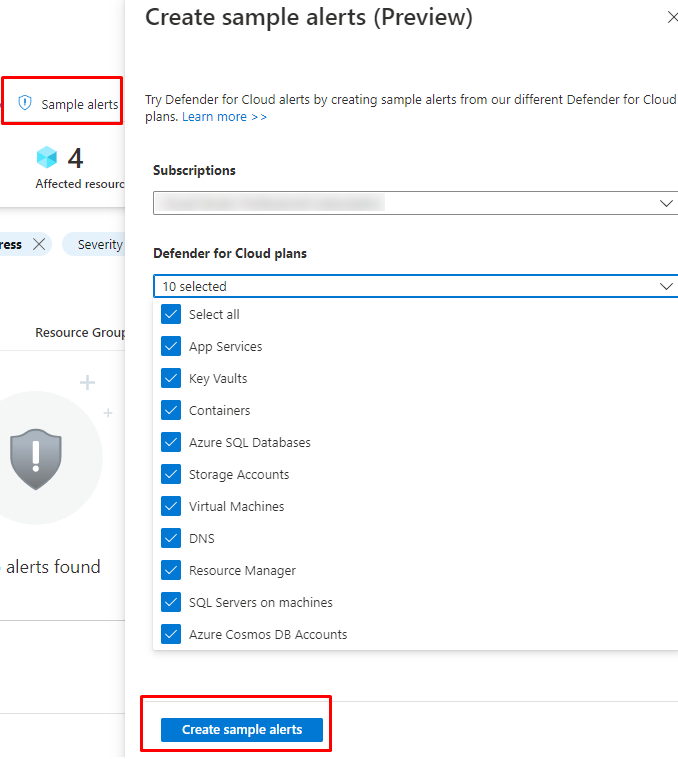

Alert validation in Microsoft Defender for Cloud
And the result, table full of stuff to play with.
Closure
Keep the story short, don't keep RDP open, use Bastion or allow only IP's you need and use. I prefer Bastion. Let's get to number down from 3,208,708 million.
Use preventive measures to scout your environment, Defender for Cloud and other Defender family products are just for this purpose.
Some functions are for free, some have trials and some cost money but all of them will help to be more secure than yesterday.
