Cross-tenant access settings (Preview)
- The access settings you configure for users and groups must match the access settings for applications. Conflicting settings aren't allowed, and you’ll see warning messages if you try to configure them.
- If you block access to all apps by default, users will be unable to read emails encrypted with Microsoft Rights Management Service (also known as Office 365 Message Encryption or OME). To avoid this issue, we recommend configuring your outbound settings to allow your users to access this app ID: 00000012-0000-0000-c000-000000000000. If this is the only application you allow, access to all other apps will be blocked by default.
- To configure cross-tenant access settings in the Azure portal, you'll need an account with a Global administrator or Security administrator role.
- To configure trust settings or apply access settings to specific users, groups, or applications, you'll need an Azure AD Premium P1 license.
PowerShell
Cross-tenant sign-in activity PowerShell script
You can get sign-in activity with the following. https://github.com/AzureAD/MSIdentityTools/wiki/Get-MSIDCrossTenantAccessActivity
Get-MSIDCrossTenantAccessActivity -SummaryStats -ResolveTenantId
Sign-in logs PowerShell script
To determine your users' access to external Azure AD organizations, you can use the Get-MgAuditLogSignIn cmdlet in the Microsoft Graph PowerShell SDK to view data from your sign-in logs for the last 30 days.
Get-MgAuditLogSignIn ` -Filter “ResourceTenantID ne ‘your tenant id’” ` -all:$True| ` group ResourceTenantId,AppDisplayName,UserPrincipalName| ` select count, @{n=’Ext TenantID/App User Pair’;e={$_.name}}]How to create or edit those settings?
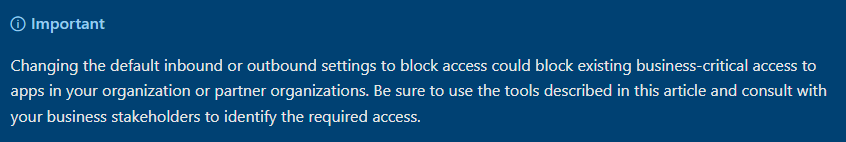
Adding organization
First You will add the external tenant to Your settings.
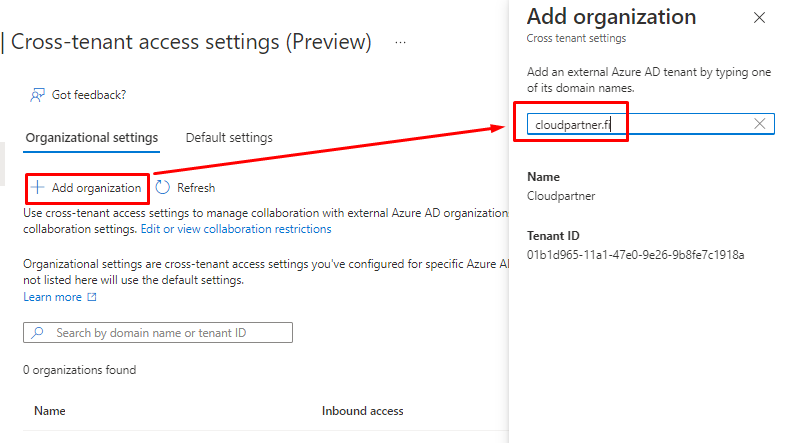
You will see the tenant name and ID. You can also add the original onmicrosoft.com name.
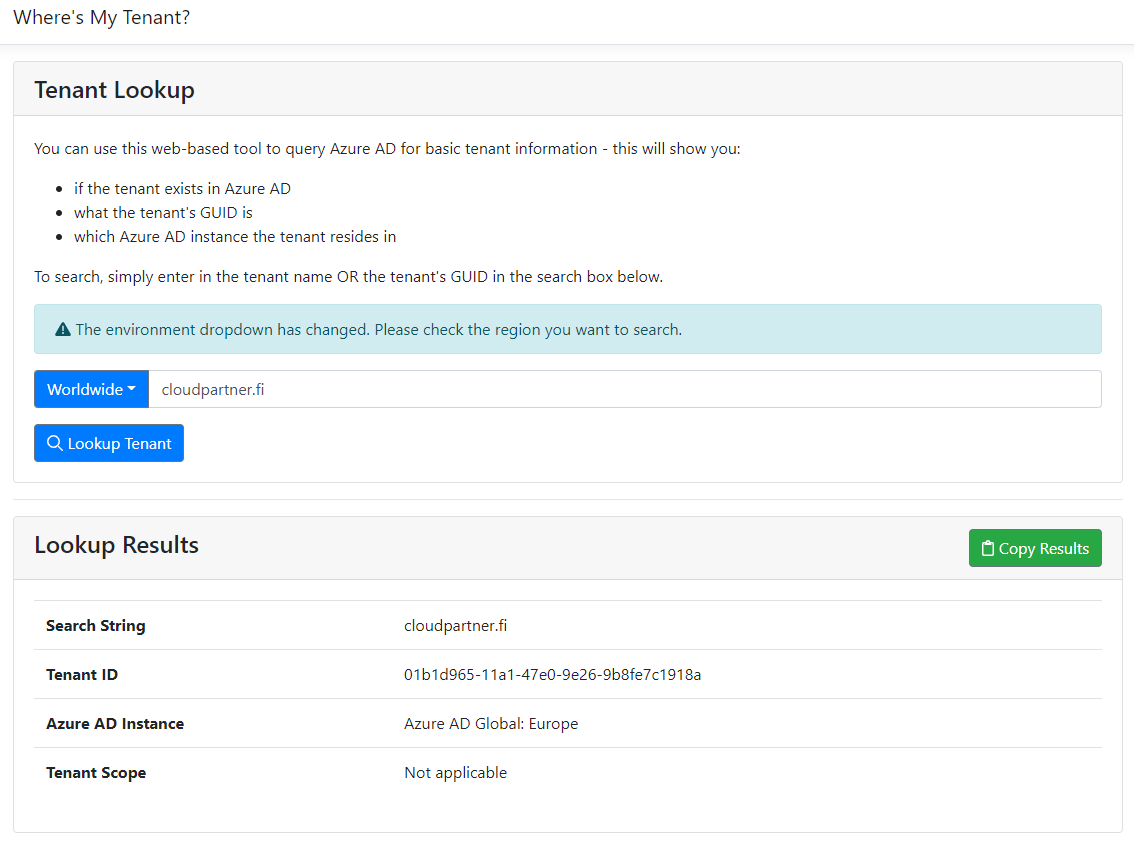
Quick tip! You can use this webpage to check out any tenants ID
Tenant Lookup
When You add the tenant it will use default settings.
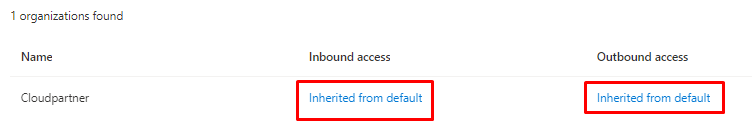
Editing the Inbound settings - External users and groups
Opening settings opens the following page, from there You can example add specific users. Although at this time You have to add the object ID for the users or groups.
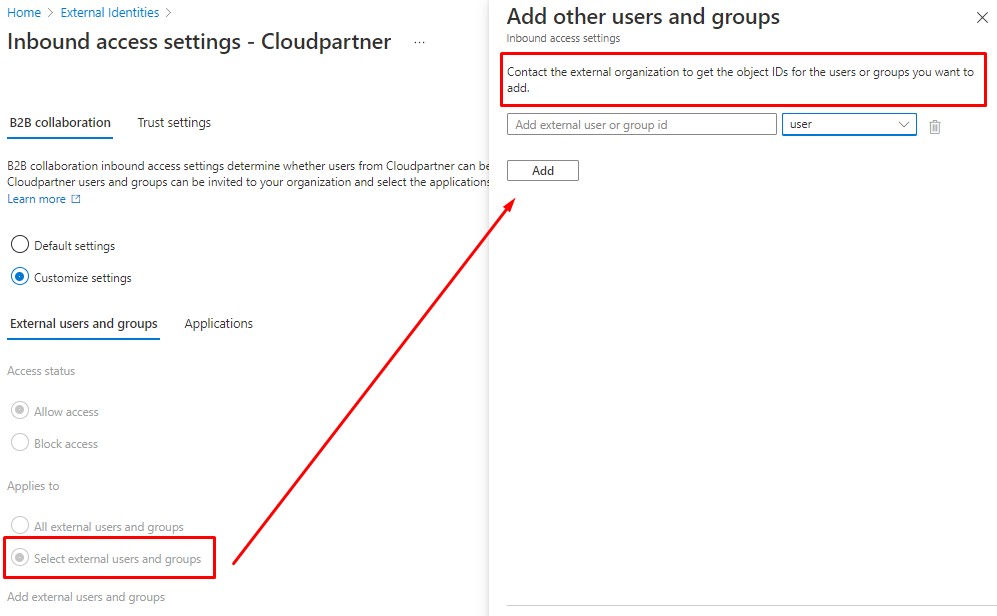
Applications
You can add Your own published applications or Microsoft applications.
Trust settings
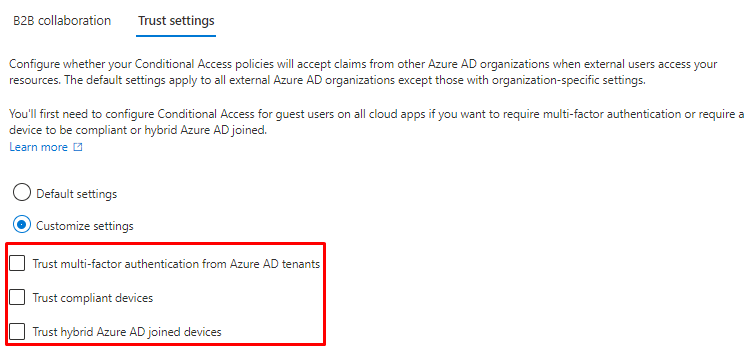
- Trust multi-factor authentication from Azure AD tenants: Select this checkbox to allow your Conditional Access policies to trust MFA claims from external organizations. During authentication, Azure AD will check a user's credentials for a claim that the user has completed MFA. If not, an MFA challenge will be initiated in the user's home tenant.
- Trust compliant devices: Allows your Conditional Access policies to trust compliant device claims from an external organization when their users access your resources.
- Trust hybrid Azure AD joined devices: Allows your Conditional Access policies to trust hybrid Azure AD joined device claims from an external organization when their users access your resources.
Editing the Outbound settings
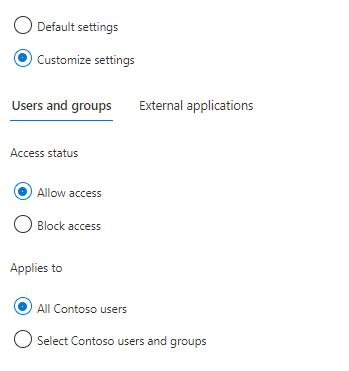
Users and groups
B2B collaboration outbound access settings determine whether your users can be invited to the external tenant for B2B collaboration and added to their directory as guests. Below, specify whether your users and groups can be invited to external tenant and the external applications they can access.
External applications
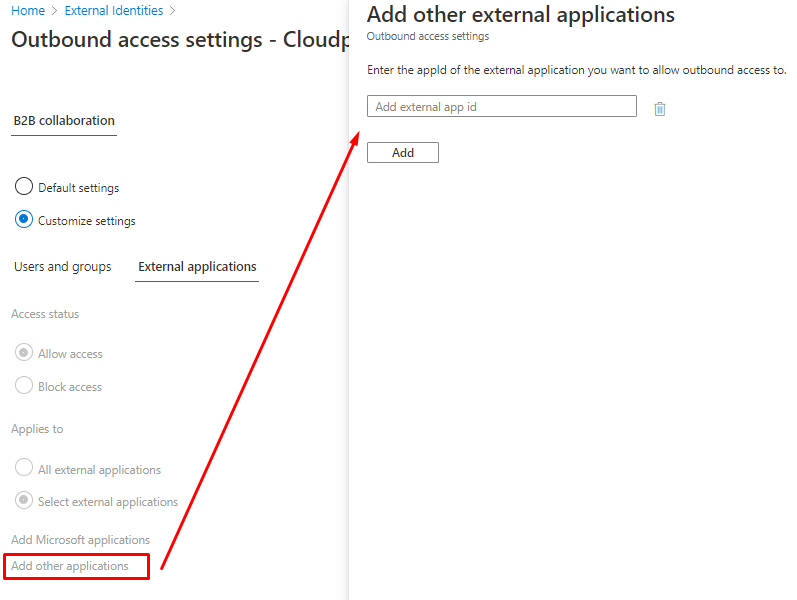
How to find the Application ID?
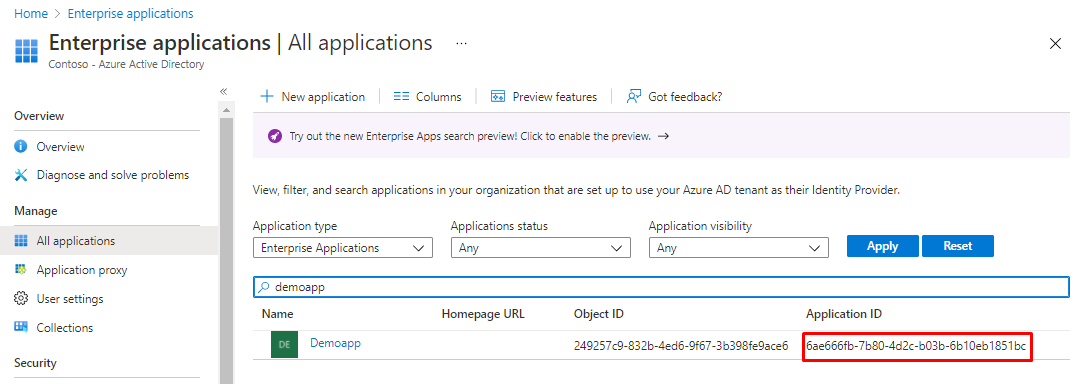
Every published application has an unique GUID as ID, You can find it from Enterprise application page
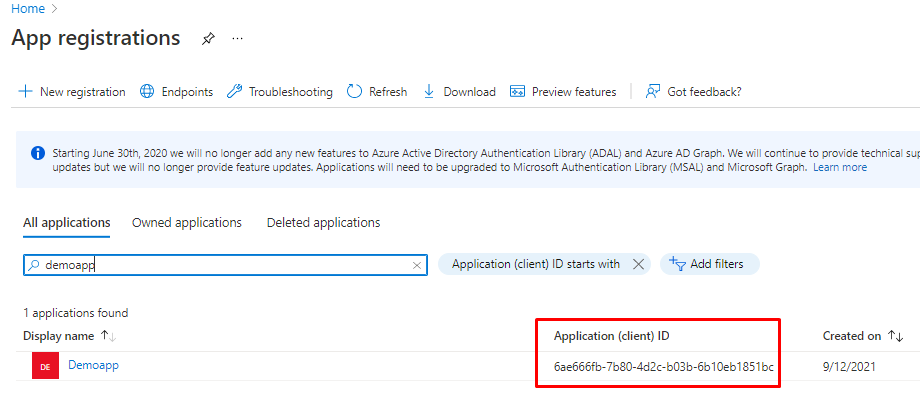
Or from App registrations page.
What are default settings?
External user experience
The experience is the same than with any Invited Azure AD guest user. Cross-tenant settings will only enforce chosen settings for the tenant specified or all tenants if You choose this setup.
Azure AD guest users and how to manage them?
