Cross-tenant access settings and Teams connect shared channels

Teams have some excellent solutions for collaborating but one big annoying things has been switching the accounts when You need to access another tenant.
Microsoft release Shared channel and it's currently in public preview after it was announced in late 2021.
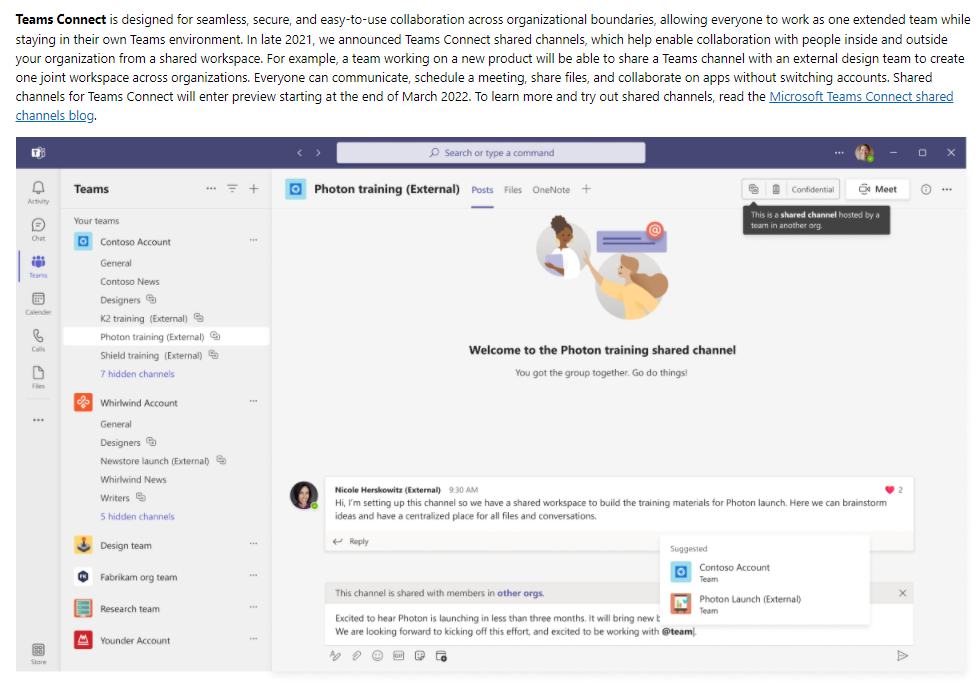
And the full page here.

3 ways to meet new hybrid expectations with Microsoft Teams and Microsoft 365 - Microsoft 365 Blog
Shared Channels
What's the difference between the channels?
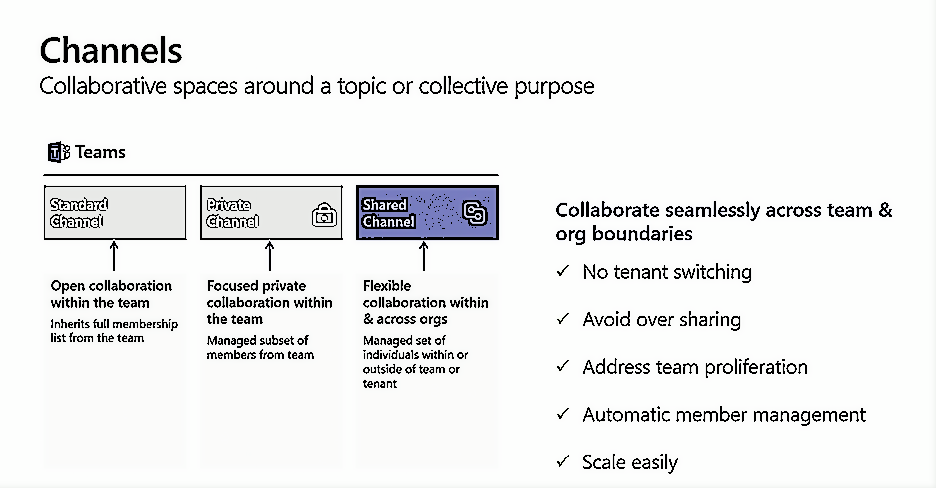
Limits for shared channels (could change after Globally available)
The following table describes the maximum number of channels and members.
| Maximum... | Value | Notes |
|---|---|---|
| Members in a team | 25,000 | Includes all users in the team and direct members in shared channels. |
| Shared channels per team | 50 | Hosted and shared with the team. (Includes deleted channels during their 30-day recovery window.) |
| Teams a channel can be shared with | 50 | Excluding parent team |
| Members in a shared channel | 1,000 direct members, including up to 50 teams. (Each team the channel is shared with counts as one member for purposes of this limit.) | Real time updates are only available to 25,000 users at a time and only 25,000 users will appear in the channel list. |
Shared channel owner and member actions
The following table outlines what actions owners, members, and guests can do in shared channels.
| Action | Team owner | Team member | Team guest | Shared channel owner | Shared channel member | Shared channel external participant |
|---|---|---|---|---|---|---|
| Create shared channel | Admin controlled | Admin and team owner controlled | No | N/A | No | No |
| Delete shared channel | Yes | No | No | Yes | No | No |
| Leave shared channel | N/A | N/A | N/A | Yes unless they are the last owner | Yes | Yes |
| Edit shared channel | No | N/A | N/A | Yes | No | No |
| Restore deleted shared channel | Yes | No | No | Yes | No | No |
| Add members | No | N/A | N/A | Yes | No | No |
| Edit settings | No | N/A | N/A | Yes | No | No |
| Manage tabs and apps | No | N/A | N/A | Yes, apps must be installed for the team | Channel owner controlled | No |
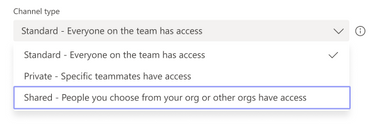
How to create a Shared channel?
When You have a Team, you will create a channel under it and once channel types below are available inside Your tenant, you will choose Shared as it's type.
I won't cover the Teams features any more than this. I will let Mr. Metaverse to explain more as he is the expert in this area.

Shared Channels: Collaborate beyond borders in Microsoft Teams
How does Cross-tenant access settings come in the picture?
But then to my favorite area, Identity and Access management.
Admins will always have the steering wheel
Collaborate externally in shared channels powered by B2B Direct Connect, a new way to collaborate with other Azure AD organizations. It is not necessary to add external users as B2B guests. Azure AD admins can manage B2B direct connections using cross-tenant access policies. External collaboration is disabled by default. To enable a shared channel between organizations, both parties must configure a multi-tenant access policy. Administrators can grant, restrict, or revoke access for external users at the individual, group, or tenant level.
So what is Cross-tenant access?
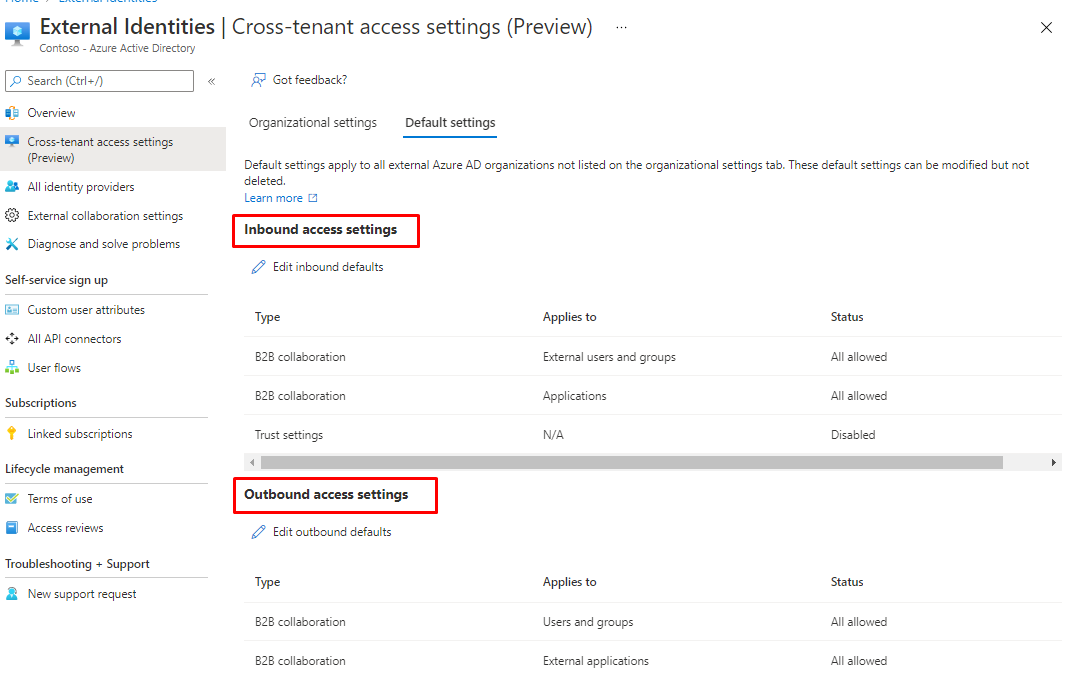
External Identities cross-tenant access settings to manage how you collaborate with other Azure AD organizations through B2B collaboration. These settings determine both the level of inbound access users in external Azure AD organizations have to your resources, as well as the level of outbound access your users have to external organizations. They also let you trust multi-factor authentication (MFA) and device claims (compliant claims and hybrid Azure AD joined claims) from other Azure AD organizations.
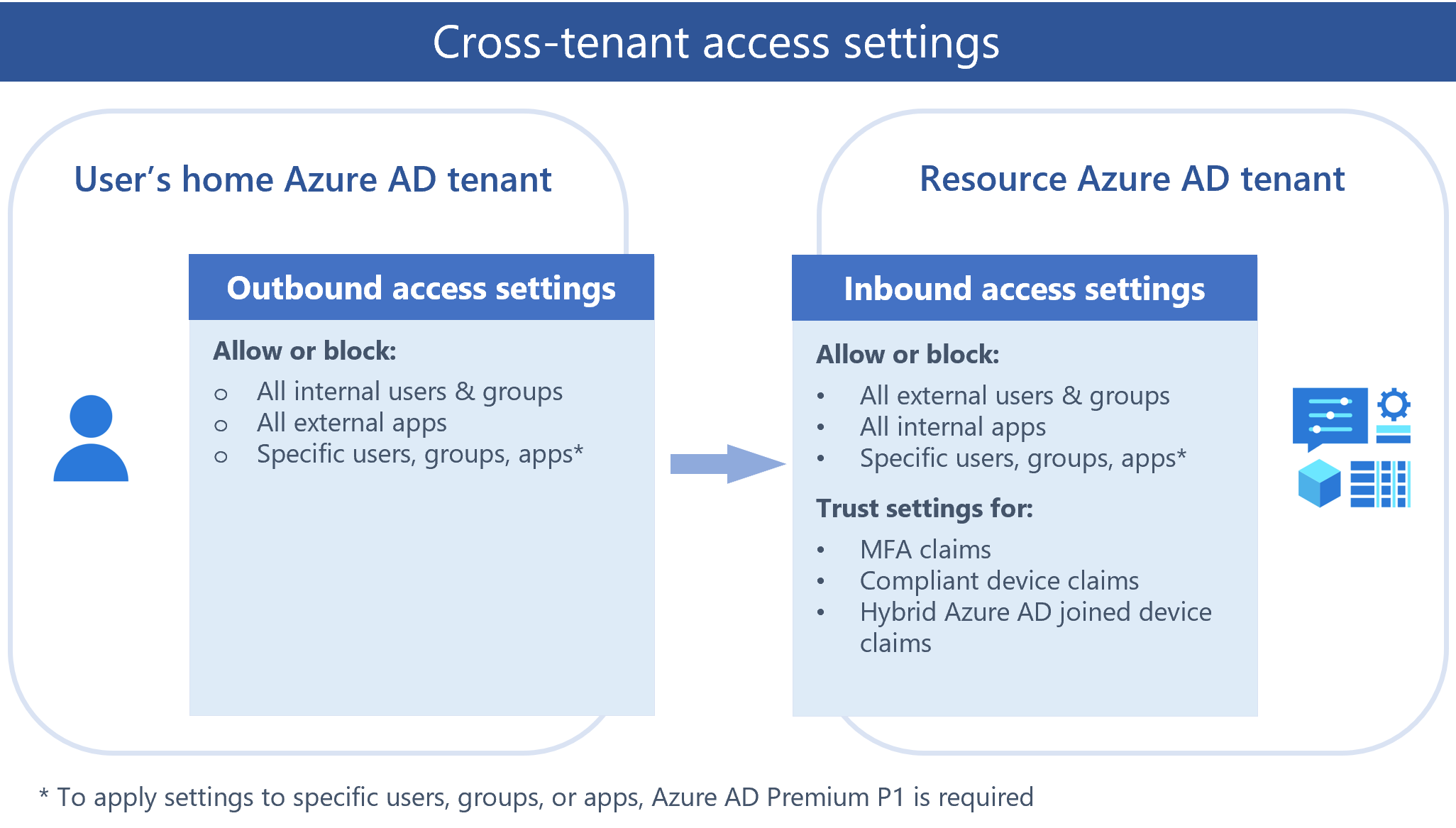
Cross-tenant access settings in now in preview. You can use cross-tenant access settings to manage collaboration with external Azure AD organizations but for non-Azure AD organizations, use collaboration settings.
You can find the settings under https://portal.azure.com/#blade/Microsoft_AAD_IAM/AllowlistPolicyBlade
Manage external access with inbound and outbound settings
B2B collaboration is enabled by default, but comprehensive admin settings let you control your B2B collaboration with external partners and organizations
- Outbound access settings control whether your users can access resources in an external organization. You can apply these settings to everyone, or you can specify individual users, groups, and applications.
- Inbound access settings control whether users from external Azure AD organizations can access resources in your organization. You can apply these settings to everyone, or you can specify individual users, groups, and applications.
- Trust settings (inbound) determine whether your Conditional Access policies will trust the multi-factor authentication (MFA), compliant device, and hybrid Azure AD joined device claims from an external organization if their users have already satisfied these requirements in their home tenants. For example, when you configure your trust settings to trust MFA, your MFA policies are still applied to external users, but users who have already completed MFA in their home tenants won't have to complete MFA again in your tenant.
How does it affect Your tenant?
- The access settings you configure for users and groups must match the access settings for applications. Conflicting settings aren't allowed, and you’ll see warning messages if you try to configure them.
- If you block access to all apps by default, users will be unable to read emails encrypted with Microsoft Rights Management Service (also known as Office 365 Message Encryption or OME). To avoid this issue, we recommend configuring your outbound settings to allow your users to access this app ID: 00000012-0000-0000-c000-000000000000. If this is the only application you allow, access to all other apps will be blocked by default.
- To configure cross-tenant access settings in the Azure portal, you'll need an account with a Global administrator or Security administrator role.
- To configure trust settings or apply access settings to specific users, groups, or applications, you'll need an Azure AD Premium P1 license.
PowerShell
Cross-tenant sign-in activity PowerShell script
You can get sign-in activity with the following. https://github.com/AzureAD/MSIdentityTools/wiki/Get-MSIDCrossTenantAccessActivity
Get-MSIDCrossTenantAccessActivity -SummaryStats -ResolveTenantId
Sign-in logs PowerShell script
To determine your users' access to external Azure AD organizations, you can use the Get-MgAuditLogSignIn cmdlet in the Microsoft Graph PowerShell SDK to view data from your sign-in logs for the last 30 days.
Get-MgAuditLogSignIn ` -Filter “ResourceTenantID ne ‘your tenant id’” ` -all:$True| ` group ResourceTenantId,AppDisplayName,UserPrincipalName| ` select count, @{n=’Ext TenantID/App User Pair’;e={$_.name}}]How to create or edit those settings?
Adding organization
First You will add the external tenant to Your settings.
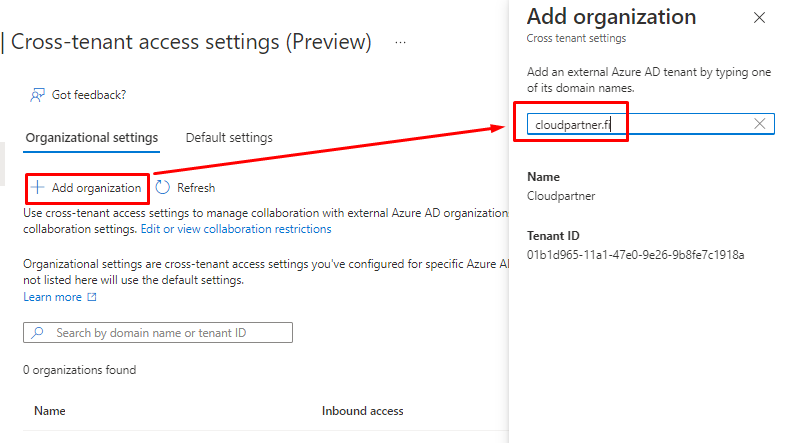
You will see the tenant name and ID. You can also add the original onmicrosoft.com name.
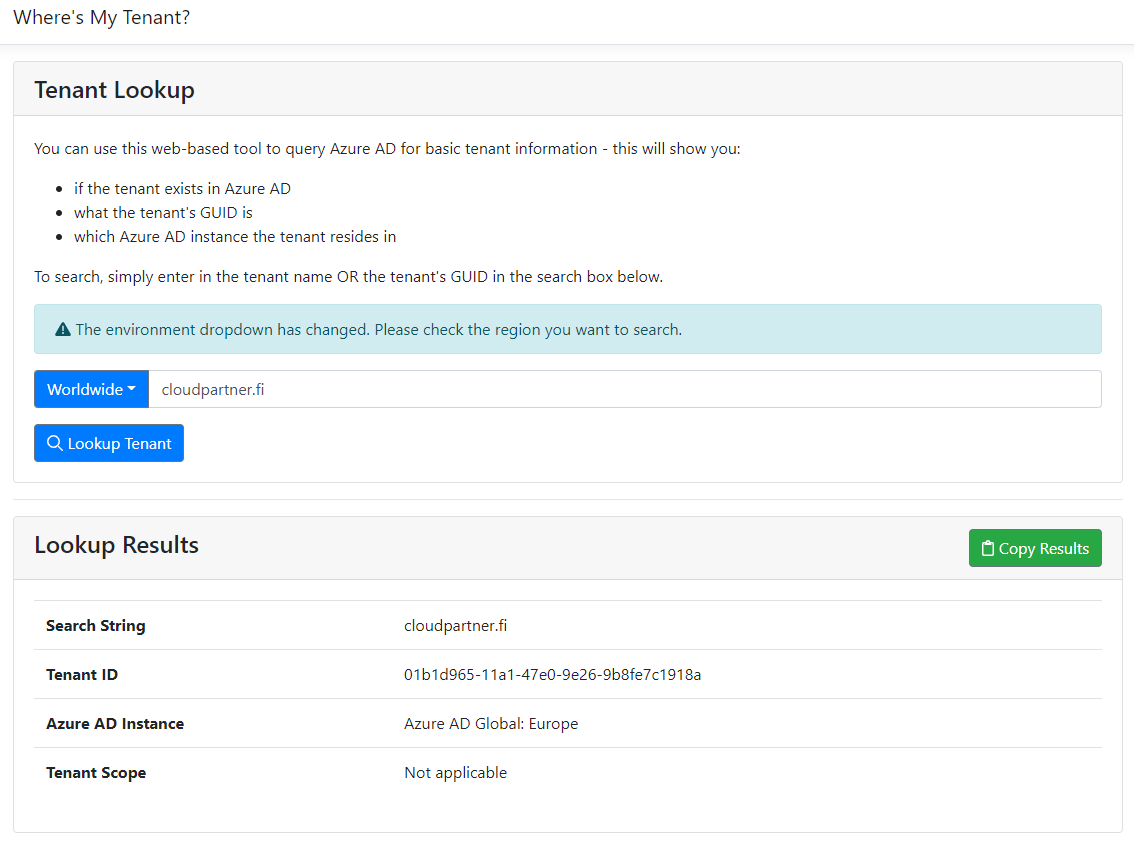
Quick tip! You can use this web page to check out any tenants ID
Tenant Lookup
When You add the tenant it will use default settings.
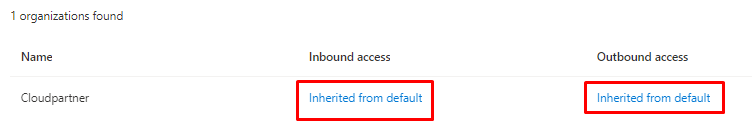
Editing the Inbound settings - External users and groups
Opening settings opens the following page, from there You can example add specific users. Although at this time You have to add the object ID for the users or groups.
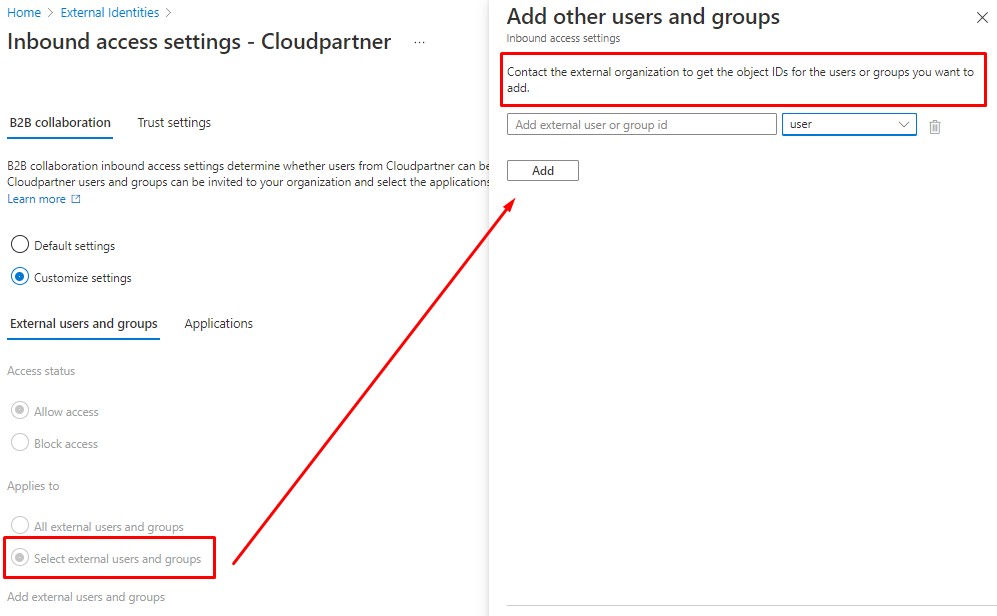
Applications
You can add Your own published applications or Microsoft applications.
Trust settings
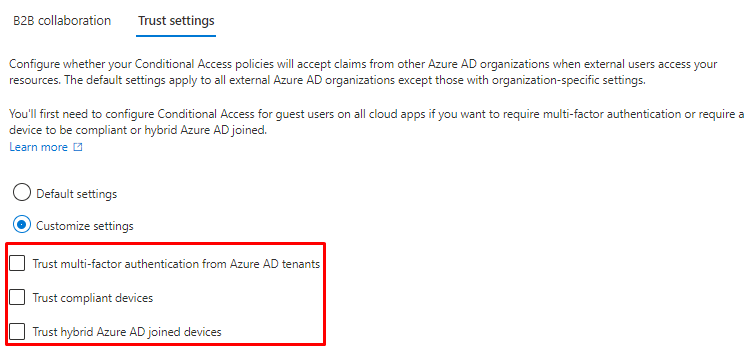
- Trust multi-factor authentication from Azure AD tenants: Select this checkbox to allow your Conditional Access policies to trust MFA claims from external organizations. During authentication, Azure AD will check a user's credentials for a claim that the user has completed MFA. If not, an MFA challenge will be initiated in the user's home tenant.
- Trust compliant devices: Allows your Conditional Access policies to trust compliant device claims from an external organization when their users access your resources.
- Trust hybrid Azure AD joined devices: Allows your Conditional Access policies to trust hybrid Azure AD joined device claims from an external organization when their users access your resources.
Editing the Outbound settings
Users and groups
B2B collaboration outbound access settings determine whether your users can be invited to the external tenant for B2B collaboration and added to their directory as guests. Below, specify whether your users and groups can be invited to external tenant and the external applications they can access.
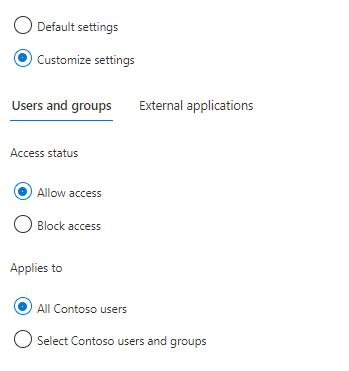
What about External applications?
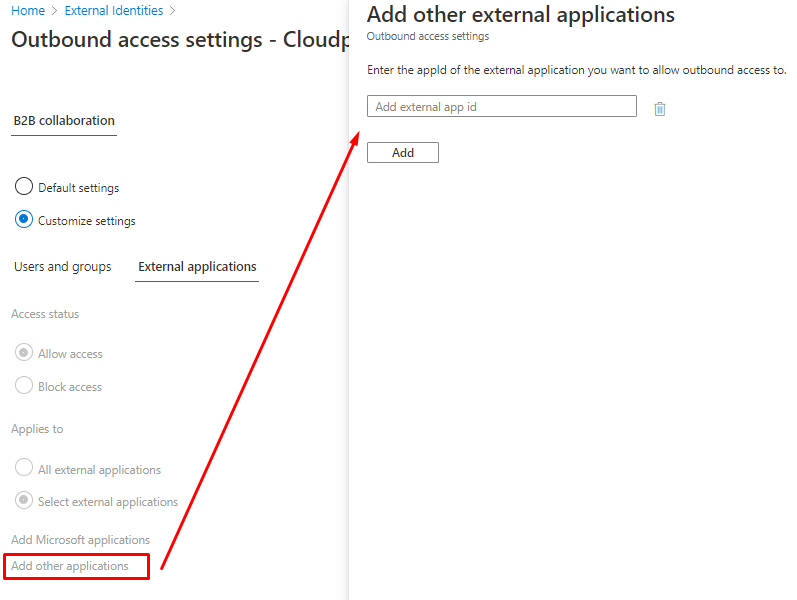
How to find the Application ID?
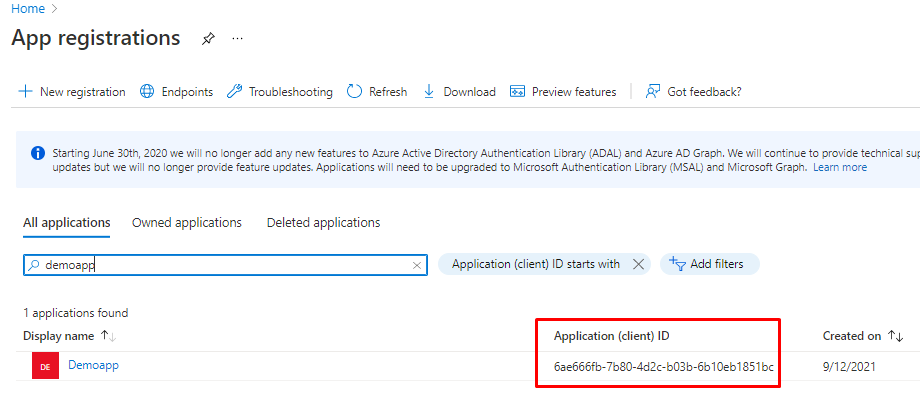
Every published application has an unique GUID as ID, You can find it from Enterprise application page
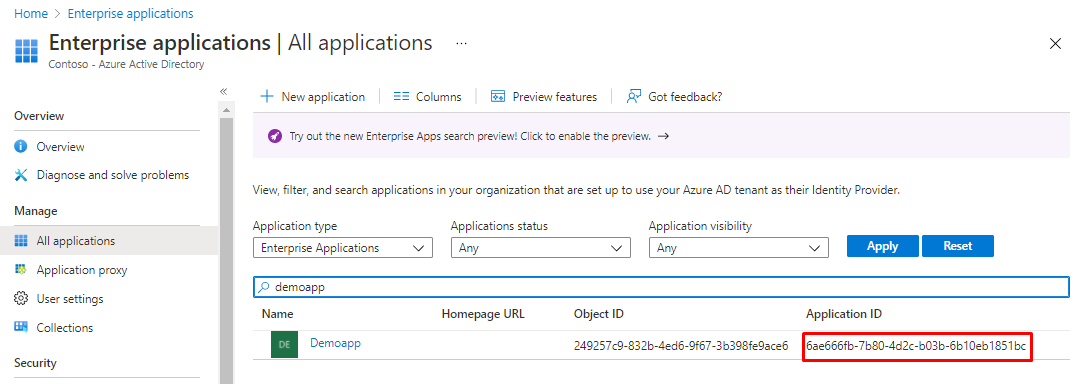
Or from App registrations page.
What are default settings?
External user experience
The experience is the same than with any Invited Azure AD guest user but no Guest user will be created. Cross-tenant settings will only enforce chosen settings for the tenant specified or all tenants if You choose this setup.
More information on the feature

Microsoft Teams Connect shared channels is rolling out to public preview
Maybe You also want to check out my post about Guest users and how to manage them?
Azure AD guest users and how to manage them?
