Azure Landing Zone Design Areas—A practical, 2025-ready guide
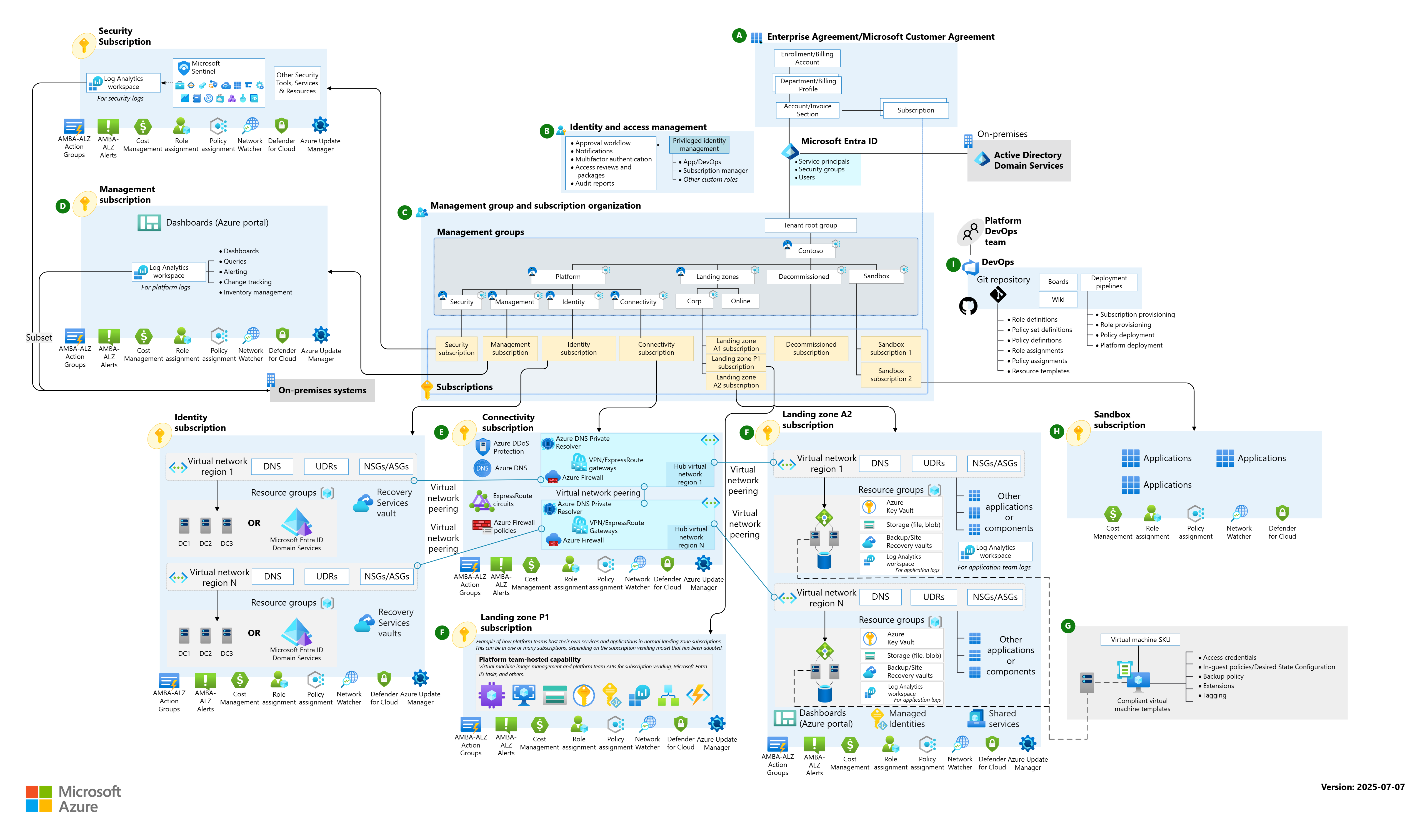
If you’re setting up an enterprise-grade Azure platform, the Cloud Adoption Framework (CAF) “design areas” are your blueprint. Below is a practitioner-friendly take on each area, how they fit together, and what’s new in 2025—plus concrete choices, pitfalls, and implementation options you can put to work right away.
TL;DR
Azure landing zones are built around eight design areas—four “environment” foundations and four “compliance & operations” capabilities. Treat these as the control plane for scale, security, and day‑2 operations. Microsoft’s conceptual architecture and the design‑area articles are the canonical source; use them as your baseline and tailor cautiously.
The eight design areas at a glance
Use this as a checklist during platform reviews and as headings in your Architecture Decision Records (ADRs).
How the design areas fit together
Microsoft’s latest conceptual architecture shows platform landing zones (shared services) clearly separated from application landing zones (workloads), with subscriptions as the core unit of management—this supports subscription democratization and policy‑driven governance. Use the Visio/PDF if you need to brief stakeholders visually.
Key decisions & anti‑patterns—by design area
What’s new (or newly emphasized) in 2025
1) Security Management Group & Subscription
The ALZ conceptual architecture now
calls out a dedicated Security MG and Security Subscription (empty by default) so you
can deploy Sentinel and security tooling independently of operational logs. This
improves separation of duties and aligns with customers’ observed operating models. Tooling updates
follow the guidance over time.
2) From the “ESLZ” monolith to AVM modules
The long‑lived
terraform‑azurerm‑caf‑enterprise‑scale module is now in extended
support and slated for archiving on August 1, 2026. For new deployments,
Microsoft recommends Azure Verified Modules (AVM) for Platform Landing Zones, surfaced
via the ALZ IaC Accelerator. This shift gives you smaller, well‑tested modules and
faster feature velocity.
3) Out‑of‑the‑box compliance assignments
The ALZ portal accelerator makes it easier
to assign regulatory initiatives (ISO, PCI DSS, etc.) to your MG hierarchy during
deployment—great for establishing a baseline posture on day one.
Implementation options (Terraform‑centric)
Sequencing the work: a pragmatic order of operations
1) Identity & tenant → 2) Resource organization → 3) Governance (baseline policy initiatives) → 4) Network topology → 5) Management (telemetry, update, backup) → 6) Security (enable plans, sentinel placement) → 7) Platform automation (pipelines, canary) → 8) Regions (add new regions via tested patterns). The CAF docs provide region‑agnostic guidance and steps for adding regions to an existing platform.
Subscription vending: scale without chaos
Automate subscription creation with vending modules to enforce: MG placement, tags, RBAC, network attach (hub/vWAN), and DDoS plans—before teams deploy anything. This operationalizes subscription democratization while keeping governance intact.
Quick “definition of done” per design area
Field tips (learned the hard way)
- Separate ops vs. security telemetry: Keep operational logs in the Management subscription and security telemetry in the Security subscription to simplify RBAC and SoD—and to control Sentinel costs independently.
- Treat policies as code: Store initiative parameters and exemptions in source control; track policy assignment drift with AzGovViz and close gaps in sprints.
- Design for region moves: Even if you start single‑region, ensure the platform can add regions without refactoring (vWAN or dual‑region hub patterns).
- Modernize your IaC stack: Prefer AVM modules and the ALZ Accelerator for new work; plan a managed transition from the ESLZ module where it’s still in place.
Further reading & resources
- Design areas & conceptual architecture (Microsoft Learn) — the authoritative baseline.
- What is an Azure landing zone? — platform vs. application LZs, conceptual diagram.
- Design principles — subscription democratization, policy‑driven governance, and trade‑offs.
- Regions & landing zones — adding/migrating regions safely.
- Start with enterprise‑scale — background and evolving guidance.
- AVM for Platform Landing Zones (Learn) — Terraform AVM patterns overview.
- AVM project hub (GitHub) and Terraform Registry examples for ALZ connectivity.
- GA announcement: AVM for ALZ — details and Accelerator updates.
- ALZ update: Security MG & Subscription — why Sentinel moved and how to adopt the new design.
- Regulatory initiatives at deploy time — assign compliance policies at MG scope.
- Subscription vending — automate subscription creation aligned to governance.
- ESLZ module deprecation — extended support through Aug 1, 2026. Plan migrations.
Example Terraform-based deployment script
Here’s an example Terraform-based deployment script using Azure Verified Modules (AVM) and the ALZ IaC Accelerator pattern. This script bootstraps a Platform Landing Zone with:
- Management Group hierarchy
- Policy assignments
- Logging & monitoring
- Connectivity (Hub-and-Spoke)
- Security MG & Subscription placeholder
main.tf – Example Deployment Script
terraform { required_version = ">= 1.5.0" required_providers { azurerm = { source = "hashicorp/azurerm" version = "~> 3.100" } } } provider "azurerm" { features {} } # ------------------------- # 1. Management Groups & Policy # ------------------------- module "alz_management" { source = "Azure/avm-ptn-alz/azurerm" version = "x.y.z" # pin exact version root_management_group_id = "alz-root" deploy_policy = true policy_assignments = ["alz-default", "alz-security", "alz-compliance"] subscription_ids = { platform = "00000000-0000-0000-0000-000000000000" security = "11111111-1111-1111-1111-111111111111" } tags = { environment = "platform" owner = "cloud-team" } } # ------------------------- # 2. Management Resources (Log Analytics, Automation) # ------------------------- module "alz_management_resources" { source = "Azure/avm-ptn-management-alz/azurerm" version = "x.y.z" location = "westeurope" log_analytics_workspace = { name = "law-platform" sku = "PerGB2018" retention_in_days = 30 } enable_update_management = true } # ------------------------- # 3. Connectivity (Hub-and-Spoke) # ------------------------- module "alz_connectivity" { source = "Azure/avm-ptn-alz-connectivity-hub-and-spoke-vnet/azurerm" version = "x.y.z" location = "westeurope" hub_virtual_network = { name = "hub-vnet" address_space = ["10.0.0.0/16"] } enable_firewall = true enable_ddos = true } # ------------------------- # 4. Security Subscription Placeholder # ------------------------- # Sentinel and security tooling will be deployed here later variables.tf – Key Inputs
variable "root_management_group_id" { description = "Root MG for ALZ" type = string } variable "subscription_ids" { description = "Platform and Security subscription IDs" type = map(string) } pipeline.yml – ALZ Accelerator CI/CD (Azure
DevOps)
trigger: branches: include: - main stages: - stage: Validate jobs: - job: terraform_validate steps: - script: terraform init && terraform validate displayName: "Validate Terraform" - stage: Deploy jobs: - job: terraform_apply steps: - script: | terraform init terraform plan -out=tfplan terraform apply -auto-approve tfplan displayName: "Deploy ALZ Platform" How to run locally
terraform init terraform plan -var="root_management_group_id=alz-root" \ -var="subscription_ids={platform=\"<GUID>\",security=\"<GUID>\"}" terraform applyWhy this matters:
- Uses AVM modules (future-proof, modular).
- Aligns with CAF design areas (MGs, governance, connectivity, management).
- Compatible with ALZ IaC Accelerator pipelines for GitHub or Azure DevOps.
References
Azure landing zone design areas - Cloud Adoption Framework
What is an Azure landing zone? - Cloud Adoption Framework
Azure landing zone design principles - Cloud Adoption Framework ...
Subscription Vending, now and beyond | Microsoft Community Hub
A New Platform Management Group & Subscription for Security in Azure ...
Keep your Azure Landing Zones policy assignments up to date with Azure ...
Azure Verified Modules for Platform Landing Zones (ALZ)
Azure landing zones Terraform module - GitHub
Announcing General Availability of Terraform Azure Verified Modules for ...
New feature: easily assign regulatory compliance policies to your Azure ...
GitHub - Azure/Azure-Verified-Modules: Azure Verified Modules (AVM) is ...
avm-ptn-alz-connectivity-hub-and-spoke-vnet - Terraform Registry
Landing zone regions - Cloud Adoption Framework | Microsoft Learn
Start with Cloud Adoption Framework enterprise-scale landing zones ...
Why this matters — especially for security
Landing zones are not just an architectural nicety; they are the security backbone of your Azure estate. Here’s why:
- Identity is the first perimeter
Without a well‑designed Entra tenant and RBAC model, attackers can exploit privilege sprawl or stale accounts. PIM, MFA, and conditional access are non‑negotiable. - Management Groups and Policy enforce guardrails at scale
A single misconfigured subscription can expose sensitive data. Policy‑driven governance ensures every workload inherits the same security posture from day one. - Network topology defines your blast radius
Hub‑and‑spoke or vWAN patterns with Private Link and firewalls prevent lateral movement and reduce exposure to the public internet. - Dedicated Security Subscription = Separation of Duties
Placing Sentinel and security tooling in their own subscription isolates telemetry, simplifies RBAC, and prevents operational teams from tampering with security data. - Automation is your ally
Manual deployments invite drift and human error. Using AVM modules and the ALZ Accelerator ensures repeatable, tested, and auditable changes—critical for compliance and incident response. - Regulatory alignment from day zero
Assigning ISO, PCI DSS, or NIST initiatives at the management group level means you’re not retrofitting compliance later under pressure.
Bottom line
A landing zone designed with these principles is your control plane for trust. It reduces attack surface, enforces least privilege, and provides the telemetry you need to detect and respond quickly. In a world of increasing cloud breaches, this isn’t optional—it’s your first and best line of defence.
