Automatic assignment policy in Entitlement management
If you are not familiar with Entitlement management, read this first.
Azure AD Entitlement Management
Microsoft keeps evolving Azure AD Entitlement management solution, here is a feature added previously.
Multi-stage access review (preview)
And there is again a new feature added, let us see what it is.
Automatic assignment policy
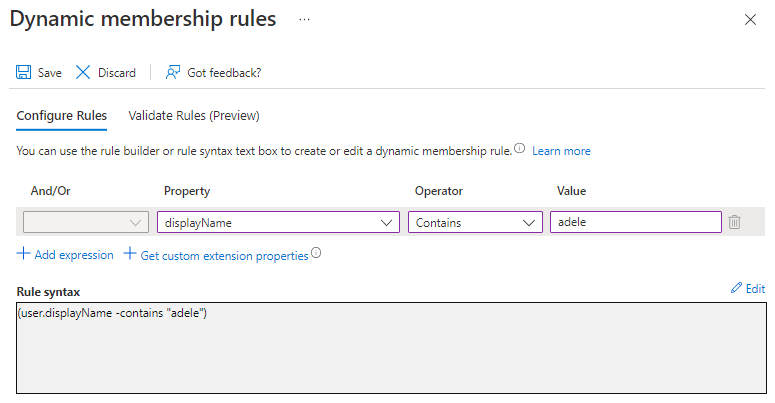
You can now create a Dynamic query for any attribute, the interface is identical to other Dynamic group interfaces.
If you want to learn more on Dynamic groups and the possible use cases, read this one.
Azure Dynamic Groups and how to use Extended attribute.
Once you have added the rule, you can create an assignment.
And you can choose custom extensions to be used.
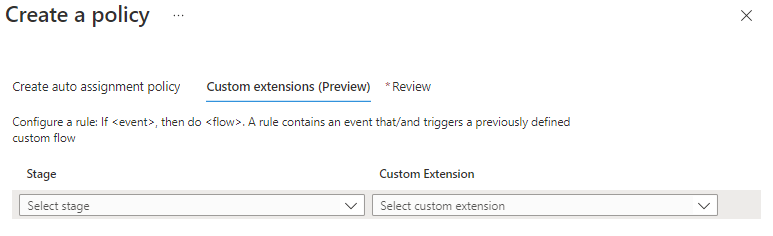
Custom extensions can be Logic apps that you have created and want to be initiated when policy kicks in.

Trigger custom Logic Apps with Azure AD entitlement management - Microsoft Entra
Then you will give it a name and description. Once done hit create!
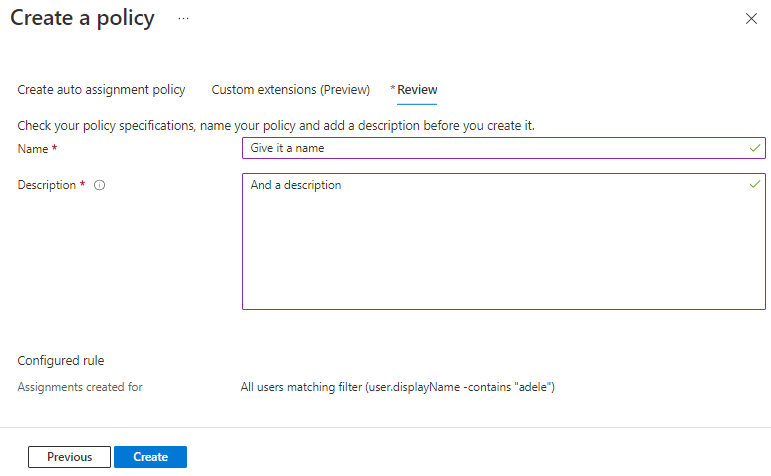
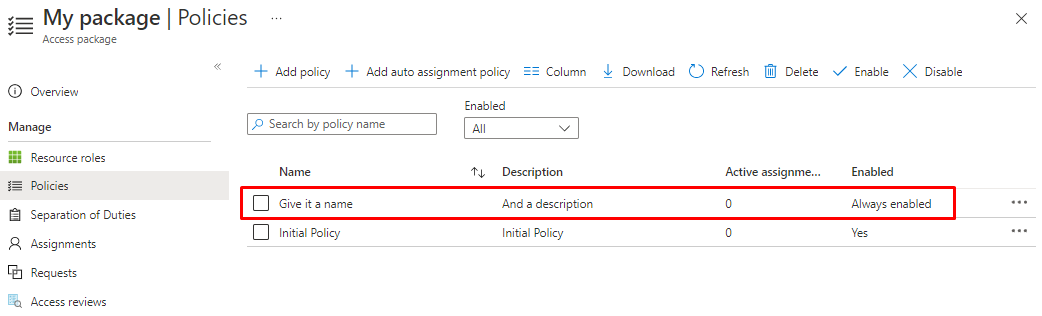
Now you have a Dynamic query based policy that will assign you defined assignments. Easy as that!
Microsoft Graph
You can also use Graph for the following actions.
Why to use Entitlement Management?
Some of the scenarios could be the following:
- Access control for a variety of resources, such as software, SharePoint Online sites, already-existing Azure AD groups and Teams, and groups deployed to on-premises AD.
- Using a combination of policies to manage access so that both rules (such as granting access to everyone in a department) and exceptions (such as employees in other departments who require the same access) may be reviewed and deleted as necessary on a regular basis
- By using custom extensions for entitlement management, which launch workflows when users gain or lose assignments, duties across Microsoft and third-party applications are further automated.
