Application Cleanup in Microsoft Entra: A Practical Deep Dive
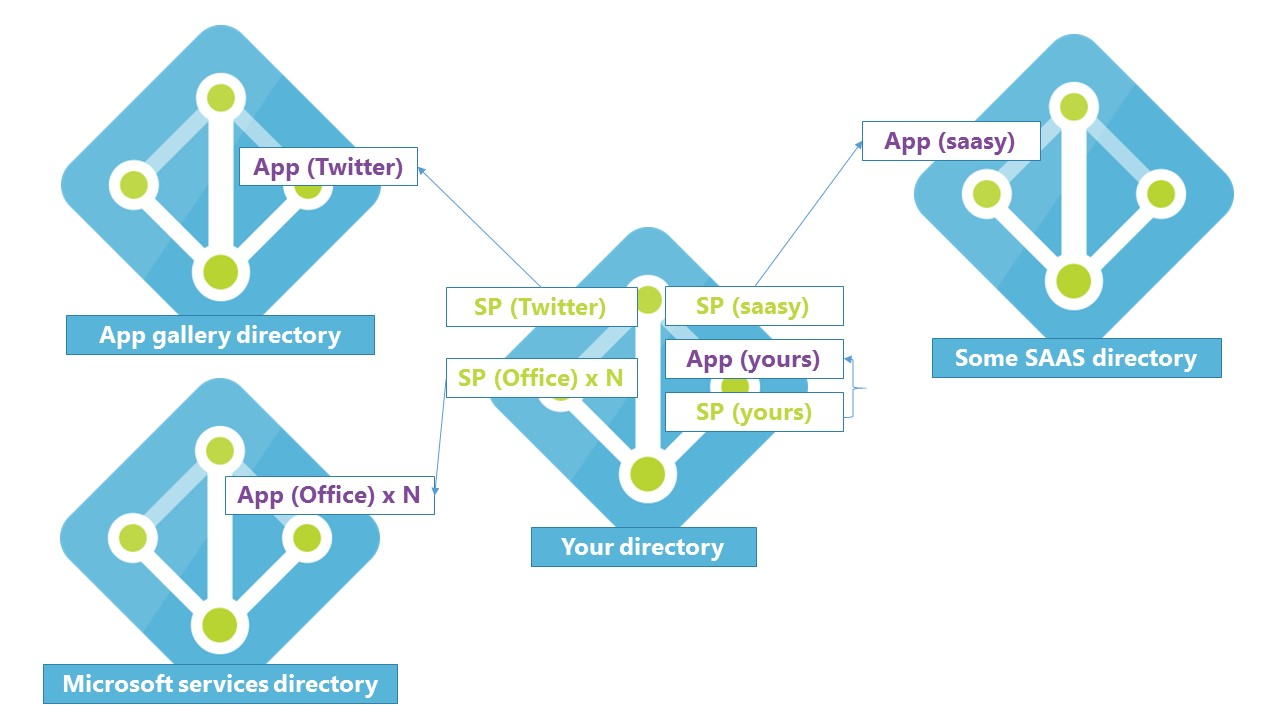
Keeping your Microsoft Entra application registry organized is more than just cleanliness—it's about security, governance, and operational clarity. Years of onboarding apps without a cleanup strategy can leave you with orphaned service principals, excessive permissions, and leakage risk. Let’s dive deeper into how to clean this up using real tooling and best practices.
Understanding Application Management in Microsoft Entra ID
Application management in Microsoft Entra ID involves registering, configuring, and maintaining applications that integrate with your organization's identity platform. This process includes:
- App Registrations: Creating entries for applications that require authentication and authorization.
- Enterprise Applications: Managing access to third-party applications integrated with your directory.
- Service Principals: Representing applications within your directory to facilitate access control.
For a comprehensive overview, refer to Microsoft's documentation on What is application management?
Step 1: Inventory All Applications (Registrations & Service Principals)
Start with a full listing of your registered applications:
# Using Microsoft Graph PowerShell SDK: Connect-MgGraph -Scopes "Application.Read.All","Directory.Read.All" Get-MgApplication -All | Select DisplayName, AppId, Id Get-MgServicePrincipal -All | Select DisplayName, AppId, IdThis gives you a snapshot of your app footprint and lets you cross-reference registrations with service principals.
Step 2: Find the Unused or Stale Apps – Let Microsoft Help You
Microsoft Entra provides a built-in recommendation: Remove unused applications. It flags any app with no token issuance in the past 90 days, helping you quickly identify cleanup candidates. You can review these in the Microsoft Entra admin center under Recommendations, or query via Graph API:
GET https://graph.microsoft.com/beta/directory/recommendations/{tenantId}_staleApps/impactedResourcesUse this to list stale applications (Microsoft Learn).
Step 3: Drill Down on Application Permissions
Clean inventory isn’t enough—you need to know who has access to what. Use the Microsoft Graph API or PowerShell to report on app permissions:
Get-MgServicePrincipalOAuth2PermissionGrant -All | Select ClientId, ResourceId, ConsentTypeFor a more polished report, check out Vasil Michev’s inventory script that captures app registration details, permission scopes, and credential expiry status (Blog, Practical 365).
Or use PnP PowerShell to pull key/certificate expiry information at scale (PnP Community).
Step 4: Plan Your Clean-Up Workflow
A safe, methodical plan can help avoid accidental service disruptions:
- Notify stakeholders — Tag app owners or teams that might be impacted.
- Backup configuration — Export app details or capture via scripting for recovery if needed.
- Soft-delete first, especially for flagged stale apps, and allow a 15-day recovery window (via Recycle Bin in Entra). You can also dismiss or postpone recommendations if needed (Microsoft Learn).
- Track sign-in logs post-cleanup to monitor for unexpected errors.
Step 5: Automate Governance
Establish guardrails to avoid accumulating technical debt:
- Access Reviews: Regularly review app ownership and permissions via Entra ID’s governance features.
- Automation Scripts: Schedule scripts to flag stale apps or report expiring credentials.
- Zero Trust Hygiene: Encourage managed identities, certificate-based auth, and short-lived secrets.
Sample PowerShell: Report Stale Apps and Permissions
# Connect to Microsoft Graph with the required permissions # The scopes you chose are correct for these tasks. Connect-MgGraph -Scopes "Directory.Read.All","DirectoryRecommendations.Read.All" # --- Stale Apps Report --- # Get recommendations from the beta endpoint Write-Host "Fetching directory recommendations..." $recommendations = Invoke-MgGraphRequest -Method GET -Uri "https://graph.microsoft.com/beta/directory/recommendations" # Filter for the 'staleApps' recommendation(s) $staleAppRecommendations = $recommendations.value | Where-Object recommendationType -eq "staleApps" if ($staleAppRecommendations) { $allStaleApps = foreach ($rec in $staleAppRecommendations) { Write-Host "Found stale app recommendation with ID: $($rec.id). Fetching impacted resources..." # Construct the correct URI to get the impacted resources for this specific recommendation $uri = "https://graph.microsoft.com/beta/directory/recommendations/$($rec.id)/impactedResources" # Get the impacted apps using the correct URI $impactedApps = Invoke-MgGraphRequest -Method GET -Uri $uri # Output the value property to be collected in the $allStaleApps variable $impactedApps.value } # Export the list of stale apps to a CSV with correct properties $allStaleApps | Select-Object id, appId, displayName | Export-Csv staleApps.csv -NoTypeInformation Write-Host "Successfully exported stale apps to staleApps.csv" } else { Write-Host "No 'staleApps' recommendation found." } # --- Permissions Report --- # Get all OAuth2 permission grants for the entire tenant Write-Host "Fetching all OAuth2 permission grants..." Get-MgOauth2PermissionGrant -All | Export-Csv appPermissions.csv -NoTypeInformation Write-Host "Successfully exported app permissions to appPermissions.csv"These exports empower you to review cleanup candidates in Excel or Power BI.
Final Checklist
| Action | Detail |
|---|---|
| Inventory Apps | Use Graph SDK or scripts to catalog registrations & principals |
| Flag Stale Apps | Rely on Entra recommendation or Graph query for unused apps |
| Audit Permissions | Pull OAuth consent grants and credential expiry data |
| Backup & Notify | Export configs and inform stakeholders before removal |
| Cleanup Safely | Soft-delete stale apps, wait 15 days before hard deletion |
| Automate Governance | Use Access Reviews, scheduled scripts, and naming conventions |
Cleaning up Entra ID app registrations is more than spring cleaning—it’s a critical security practice. Start with inventory and stale-app flags, then layer in permissions audits and automated controls to keep your environment lean, secure, and well governed.
Extra tip! If you want to learn more on App registrations, check out my previous part of AZ-500 Study Guide from this link.

AZ-500 Study guide – Section 4 – Manage identity and access – Manage Microsoft Entra application access
